How to perform penetration testing with Core Impact Tool?
INTRODUCION : PENETRATION TESTING
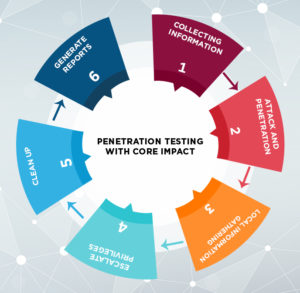
During Penetration testing, most of the testers develop some short of process and repeat it every time they perform Penetration testing. When an proper analysis is done on the basic pf pen testing, these can be broken into following six steps :
- Collecting Information
- Attack and Penetration
- Local Information Gathering
- Escalate Privileges
- Clean Up
- Generate reports
Now, I’m not saying every tester follows every step or performs these steps in this exact order, however, this is a pretty good process to follow. Let’s take a closer look at each step.
I never meant that every tester follows these steps in the exact order. But these are very good process to follow. Look at every step in detail :
Collecting Information
Testers spends majority of their time on this step. Any good pen-test involves some type of recon. The main aim is to identify as much information as possible about your target. This could include gathering information about end-users or even gathering information about the network itself. The more information we have about the target, the more precise we can be when launching attacks.
Attack and Penetration
Now, this is where the fun begins! After we’ve found out all we can about the target, we can begin attacking the target. With tools like Core Impact, you can launch specific, targeted attacks, or even launch attacks you think that will be the most likely to succeed.
Local Information Gathering
After successfully compromising a target, you should have more permissions than at the start. This allows us to find additional information such as usernames and passwords, or perhaps a list of services or applications running on the target. Once we have this information, we can proceed to the next step.
Escalate Privileges
It’s possible when we compromised the target, we only gained user access. Now that we have some additional info from the Local Information gathering step, we can use that information to elevate our privileges to that of an administrator or a privileged user. If we’re able to gain additional access, we could then go back and perform information gathering again. With more privileges, we can probably get more data.
Clean Up
Once we’ve gathered all the data we can, the next step is to clean up. Core Impact makes this very simple by clicking on the cleanup step. Core Impact will then go out and remove any agents that were deployed while the workspace was up and running.
Generate Reports
This is the most frustrating step and no one like to do it. But, you don’t have to worry, we already have the multiple templates for this according to your need. Just select the needed template and click Finish! Your report is created. You can use this info and share it with other parties.
All the above six steps in not easy as it looks but are very important and efficient. To do a successful and effective Pen-test you can follow all these steps.