IDENTITY MANAGEMENT
Identity Management: Overview
eSec Forte’s identity management system helps organizations streamline the process of managing information used to identify users, control access, delegate administrative authority and determine user privileges. Our automated identity management system improves organizational flexibility, lowers operational costs and enhances business flexibility


Identity Management: Challenges
The employees’, customers’, and contractors’ IT lifecycle is ever changing with their needs and responsibilities fluctuating often. Customer privileges can alter on the fly depending upon the account balance, membership level, credit rating calling for responsive identity management. Whenever employees are assigned new roles or transferred to another department, their access rights must be reviewed and updated according to their role and policies governing that role. Speed of privilege authorization and security policies are very critical to ensure smooth functioning of the organization.
How can we help?
We at eSecForte deliver an identity management system with the ability to create, modify
and enforce security policies. Our automated identity management system supports
information security audits, and our pre-defined reports allow users to view the security
activity and status of the organization. eSecForte’s identity and access management tools
enable organizations to define, create, implement, and automate information access control
and rights to ensure that only authorized users have access to the right data at the right time
for the right purpose.
Features of Identity Management
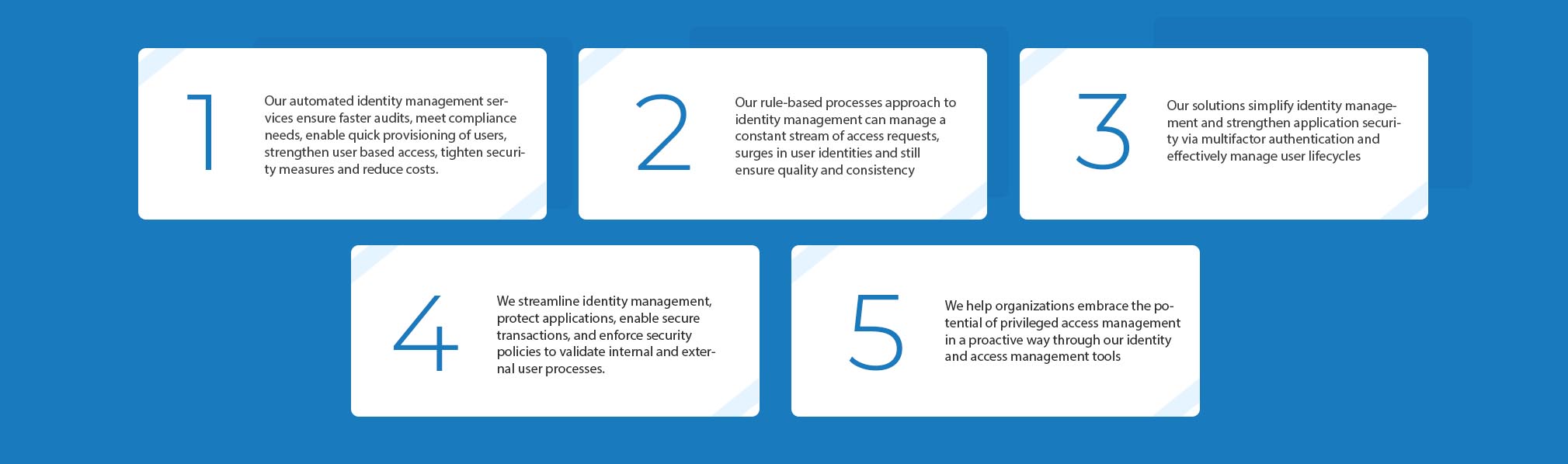
Benefits of our Identity Management Solutions

5 W’s of Identity Management
1. What is the purpose of identity and access management?
The purpose of our identity and access management solution is to enhance the overall cybersecurity infrastructure of an organization. The objectives of identity management are to maintain integrity, confidentiality, and availability of system data.
2. What is the best practice you adopt for identity access management?
One primary identity access management best practice we adopt at eSecForte is to create a centralized system of visibility to enable businesses to gain perspective into the various access rights of the users.
3. What is the primary objective of your identity access management solution?
The primary objective of our identity access management solution is to ensure that only authenticated users gain access to specific applications, systems and IT environments.
4. What is the difference between identity and access management?
Identity management is used to authenticate the user while access management determines the attributes of the user to understand what his authorization is.
5. What are the 3 main types of access controls you implement in your solution?
The 3 main types of access controls we implement in our identity access management are Discretionary access, Role-based access and Mandatory access.