Container Security Services and Solutions
Container Security Services : Best Practices, Vulnerabilities & Attacks
Container Security Services: Overview
Container security is the security of their ethics of containers. This consists of sets from the applications
which they hold into the infrastructure that they rely on. Container security should be incorporated and
continuous. Generally, constant container security for your business is all about:
- Securing the container pipeline and the application
- Preventing the container deployment environment(s) and infrastructure
- Integrating with enterprise security tools and meeting or enhancing existing security policies
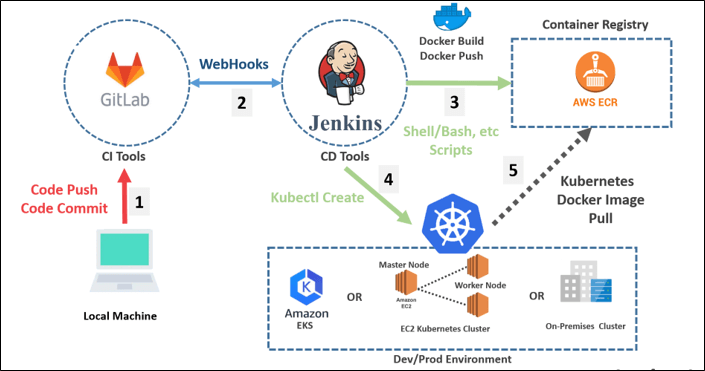

Containers are very popular since they allow it to be effortless to build, package, and promote an application or service, and its dependencies, all through its whole life cycle and across different surroundings and installation objectives. Static security policies and checklists do not climb for containers at the venture. The distribution chain demands more security coverage providers. Teams will need to balance both the media and governance demands of containers. Build and run time services and tools need decoupling.
Because they build security to the container and safeguarding your infrastructure, then you can ensure that your containers are more reliable, scalable, as well as trusted.
Container Security Methodology


Build security into the container pipeline
Containers are created out of layers of files. The container community often calls these files “container images.” The base image is the most important for security purposes because it is used as the starting point from which you create derivative images. Container security starts with finding trusted sources for base images. Even when using trusted images, though, adding applications and making configuration changes will introduce new variables. When bringing in external content to build your apps, you need to have proactive content management in mind.
- Are the container images signed and from trusted sources?
- Are the runtime and operating system layers up to date?
- How quickly and how often will the container be updated?
- Are known problems identified, and how will they be tracked?
Manage accessibility
When you have got your graphics, the following phase is always to manage access to, and promotion of all container graphics your own team uses. This means protecting the graphics you down load in addition to the people which you build. Utilizing an individual registry will permit one to regulate access through role-based missions while also assisting you to manage articles by assigning metadata into the container. Metadata will offer information for example monitoring and identifying known vulnerabilities. An individual registry additionally provides you the capacity to automate and delegate coverages to the container pictures you need stored, reducing human mistakes which could introduce vulnerabilities to your container.


When determining the best way to handle accessibility, inquire:
What role-based access controls can you use to manage container images?
Are there tagging abilities, to help sort images? Can you tag images as approved only for development, and then testing, and then production?
Does the registry offer visible metadata that allows you to track known vulnerabilities?
Can you use the registry to assign and automate policy (e.g. checking signatures, code scans, etc.)?
Container security testing and enhance installation
The previous step of this pipeline is installation. When you have completed your assembles, you have to manage them based on standards. The secret here is to learn just how to automate coverage to flag assembles with security problems, notably as fresh security vulnerabilities can be present. Since set-top containers are less good of an alternative as fixing them. Integrating security testing should take into consideration policies that activate automated rebuilds. Running component analysis tools that may flag and track problems maybe your first portion of this measure. The 2nd part is launching tooling for an automated, policy-based setup.
When incorporating security testing and automatic installation, inquire:
What role-based access controls can you use to manage container images?
Are there tagging abilities, to help sort images? Can you tag images as approved only for development, and then testing, and then production?
Does the registry offer visible metadata that allows you to track known vulnerabilities?
Can you use the registry to assign and automate policy (e.g. checking signatures, code scans, etc.)?
Defend your infrastructure
You require a host OS that offers maximum container freedom. This is just a significant portion of everything this means to safeguard your container deployments environment. The host OS is empowered employing a container run time, ideally handled through an orchestration procedure. To produce your container platform springy, utilize system namespaces into sequester applications and surroundings, and connect storage through secure mounts.
When determining the best way to safeguard your container, inquire:
How can you prevent patching running containers, and instead use triggers to rebuild and replace containers with automated updates?
Which containers need to access one another? How will they discover each other?
How will you control access and management of shared resources (e.g. network and storage)?
How will you manage host updates?
Will all of your containers require updates at the same time?
How will you monitor container health?
How will you automatically scale application capacity to meet demand?
Container Security Best Practices
- Know and control the source and content of your images
- Eradicate vulnerabilities before container deployment
- Hardening container images, daemons, and the host environment
Container Security: Vulnerabilities & attacks
- Access and authorization
- API server access
- Image vulnerabilities
- Inter-container network traffic
eSec Forte Technologies: Container Security Company
Our Container Security Services can help you with Vulnerability management, monitor and audit container activity.
eSec Forte Technologies is a CMMi Level 3 | ISO 9001:2008 | ISO 27001-2013 certified Cyber Security Audit Company and IT Services Company with service offerings in Information Security like VAPT Services, Penetration Testing Services, Vulnerability Assessment Services, Amongst our clients we proudly count Government Organizations, Fortune 1000 Companies, and several emerging companies.
We are headquartered in Gurugram, Mumbai, Delhi, Bangalore – India, Sri Lanka & Singapore. Contact our sales team @ +91 124-4264666 you can also Drop us an email at [email protected] for Container Security Services.
