Attack IQ-Breach Assessment Simulation
Achieve Real Cybersecurity Readiness Against Cyberattacks


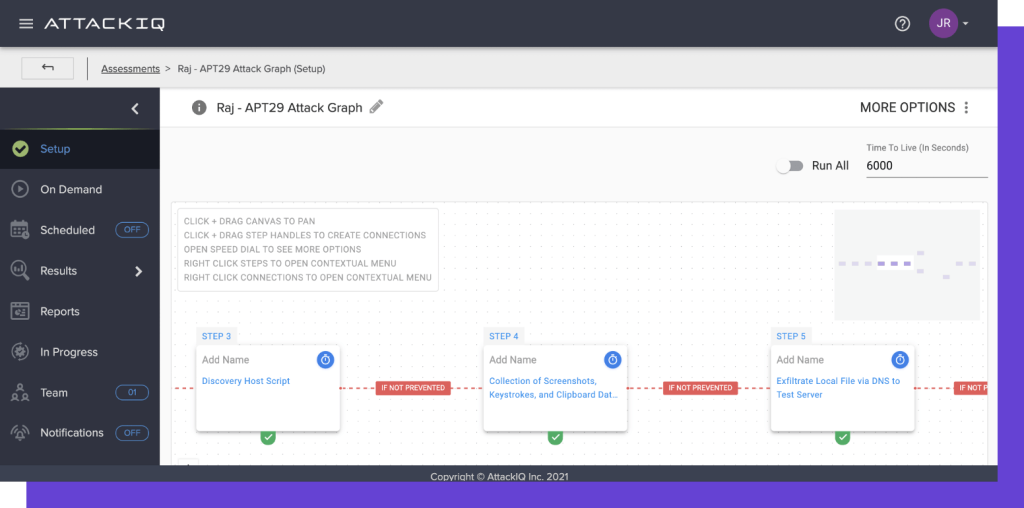

Attack IQ-Breach Assessment Simulation : Overview
Attack IQ Solutions
Automated Security Control Validation
MITRE ATT&CK
Operationalize MITRE ATT&CK and achieve a threat-informed defense through AttackIQ’s deep library of adversary emulations and research partnership with MITRE Engenuity’s Center for Threat-Informed Defense. AttackIQ is your partner not only through our technology, but through the free expert-taught courses that we curate at AttackIQ Academy, AttackIQ’s annual conference, Purple Hats, through the company’s managed security service, AttackIQ Vanguard, and by publishing research from MITRE Engenuity’s Center for Threat-Informed Defense through guides, white papers, and webinars.
Cloud Security Optimization
Test your cloud security capabilities continuously to validate that your assets and data centers are protected against the threats that matter most. The AttackIQ Security Optimization Platform validates native cloud security controls in AWS and Azure, leveraging innovative cloud security research from the Center for Threat-Informed Defense. It also validates cybersecurity solutions that operate in the cloud, to include endpoint detection and response capabilities, next generation firewalls, and micro-segmentation platforms. Learn how the AttackIQ Security Optimization Platform can help you achieve your cloud security goals.
Compliance Optimization
Align your threat and risk management frameworks to achieve security readiness, validating your compliance controls using real-world threat behaviors from the MITRE ATT&CK framework. AttackIQ’s Security Optimization Platform validates your compliance effectiveness for the NIST 800-53 family of security controls and DoD’s Cybersecurity Maturity Model (CMMC). Apply a threat-informed defense strategy to decrease your regulatory burden for a range of compliance frameworks.
Attack IQ Pricing
Its cost is dependent upon the license you wish to choose as it gives you various options. The detailed price structure can be availed through Value Added Distributor eSec Forte Technologies who are well versed with all the data associated.
Contact us today to learn more about our products and services.
We are headquartered in Gurugram & Regional Offices in Mumbai, Delhi, Bangalore – India.




