THREAT DETECTION AND RESPONSE
Threat Detection and Response: Overview
Our threat detection and response solution can offer essential support to your organization to enhance threat visibility and rapidly shut down cyber threats before they cause major damage. Our outcome-focused Managed Detection and Response (MDR) provides the resources, technology and cyber intelligence required to search for and eliminate threats across your organization


Threat Detection and Response: Challenges
Hackers today are designing sophisticated malware to attack business systems and cybercriminals are able to cleverly disguise their attacks through packing and encryption. Advanced malware can easily slip by traditional anti-virus software that cannot manage the constant inflow of ever-evolving threats. Borderless and hybrid business environments have made threat detection more challenging. Organizations need a holistic approach to security right from the network to the access point.
How can we help?
eSec Forte offers a comprehensive and powerful threat detection tool that can stop known
and new malware threats. Our skilled resources and automated processes can detect and
manage security breaches of any level. Our solutions help defend and protect enterprises through
advanced engineering, implementation and technology for effective threat detection. We implement
strategic planning and decision making by using the right tools and out threat intelligence is curated
from multiple data sources.
Features of our Threat Detection and Response
Benefits of our Threat Detection and Response Solutions
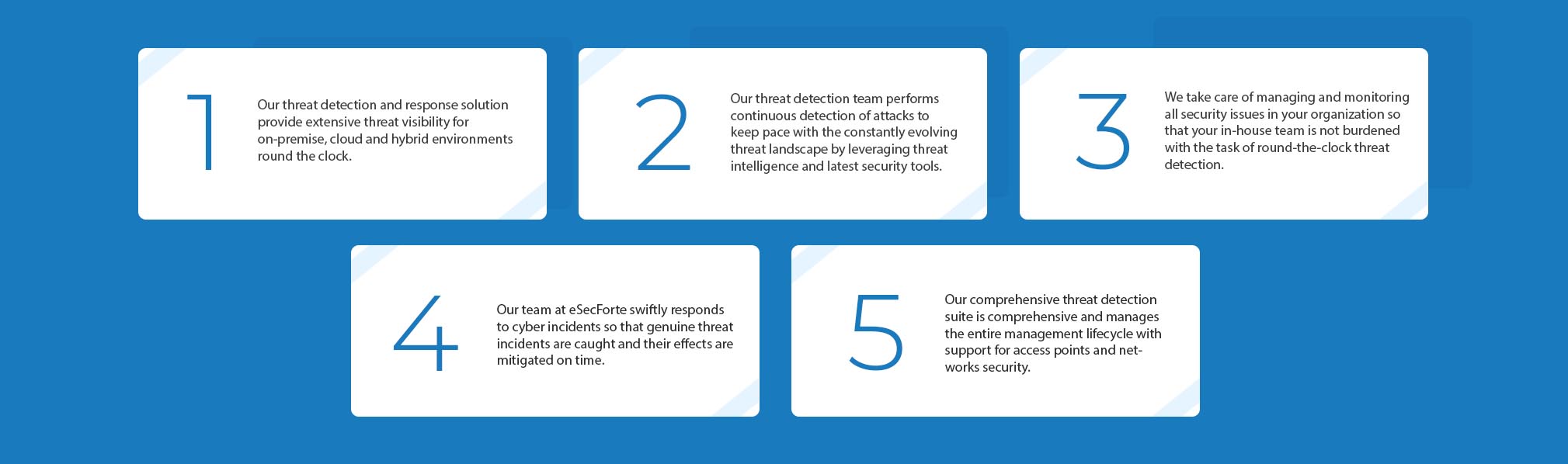

5 W’s of Threat Detection and Response
1. Why must my enterprise consider threat detection and responses solutions?
Businesses must consider threat detection and response services designed for enterprises who wish to remain safe against cybersecurity attacks but do not have the time or resources for the same.
2. Do I need it even if I have a firewall?
Firewalls are barriers and form a part of a robust cybersecurity strategy but by themselves are not the best form of defense as most hackers can get around firewalls. An organization requires a strong threat defense and response system to achieve maximum protection against all threats.
3. What types of threats can your threat detection and response system detect?
Our solution can detect common threats, targeted threats, and insider threats.
4. How can your solution help my organization?
Your organization can do 24/7 security monitoring through our solution along with incident response, threat hunting, and remediation.
5. What do you do when a threat is detected?
When our testing team at eSec Forte detects a threat, it immediately begins the mitigation efforts needed to neutralize it before it can exploit any vulnerabilities.