

Secured Socket Layer Pinning Bypass via Frida
INTRODUCTION
SSL pinning allows the application to only trust the valid or pre-defined certificate or Public Key. The application developer uses SSL pinning technique as an additional security layer for application traffic. As normally, application trusts custom certificate and allows application to intercept the traffic. But in the SSL Pinning implementation, application does not trust custom certificates and does not allow proxy tools to intercept the traffic.
As per Frida Website :-
Frida is a dynamic code instrumentation toolkit. It lets you inject snippets of JavaScript or your own library into native apps on Windows, macOS, GNU/Linux, iOS, Android, and QNX. Frida also provides you with some simple tools built on top of the Frida API. These can be used as-is, tweaked to your needs, or serve as examples of how to use the API.
1. REQUIREMENTS
Below are the all requirements for SSL Pinning Bypass –
– Rooted Device/Emulator
We will be needing a rooted device or an emulator, since we need to inject a script into the root directory of the device. We can download an emulator through below given URL :
https://www.genymotion.com/fun-zone/
Once Genymotion is installed, we need to install on android device version 7+.
– Python installation on ubuntu
sudo apt-get install python3.6
Other python packages to be installed :
pip install Frida
pip install objection
pip install frida-tools
– Install adb on ubuntu
sudo apt-get install adb
– Injection script
Save the following code under fridascript.js
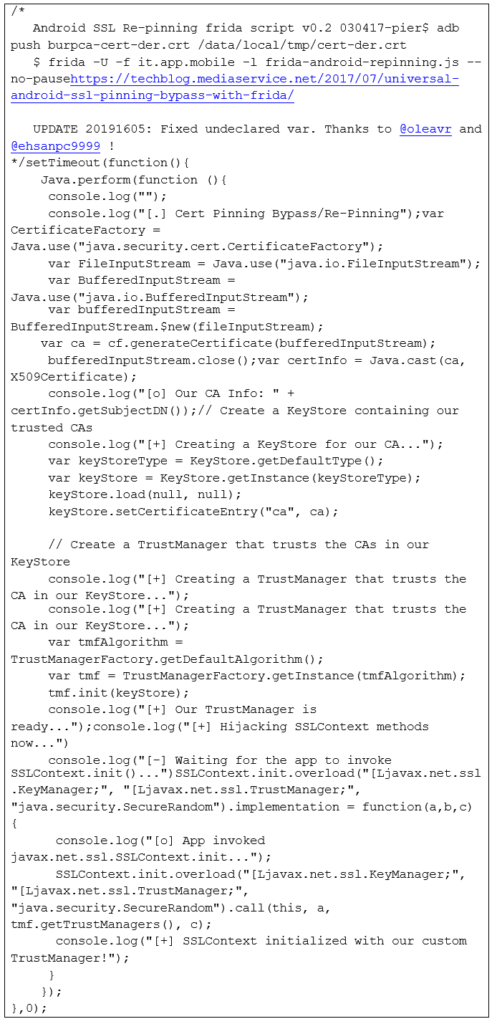

2. SETUP AND INSTALLATION
– Connect device to adb
to run commands on emulator or on android device we need to connect our device to adb. But to do that we need to go to the settings of the device or the emulator then to Developer Options and start the debugging mode, so that the device can communicate with the device.
Go to terminal in ubuntu and run the following command:
adb connect <ip address of the device>
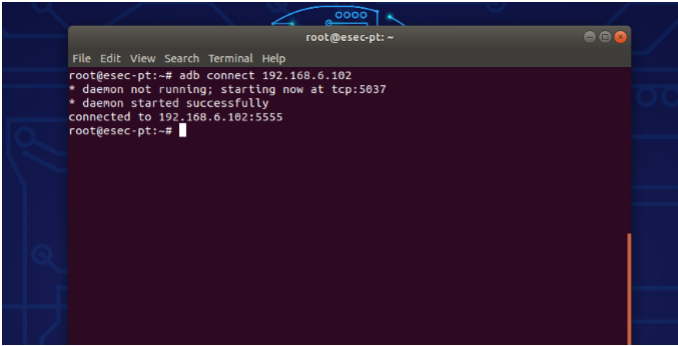

To check if the device is connected to adb:
adb devices
– Download Frida server for supported android device’s arch version:
https://github.com/frida/frida/releases/
To find out the arch version of the device, type the following command:
adb shell getprop ro.product.cpu.abi
– Install the target application in the device
Install your application who’s SSL Pinning has to be bypassed for eg: Twitter
3. Frida Server Setup:
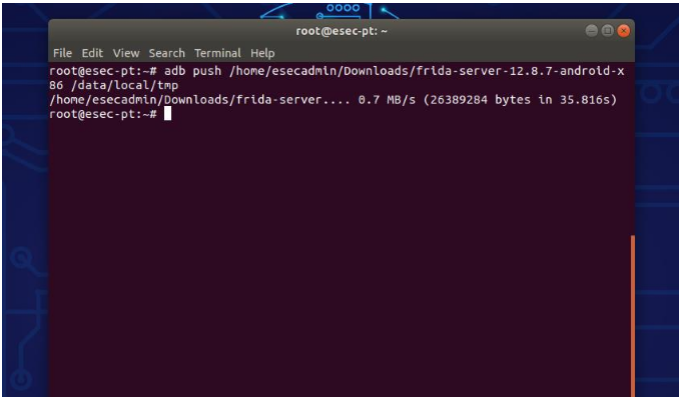
– Push Frida-server into device
Extract “frida-server-12.8.7-android-x86” and run the following command:
adb push <path_of_frida_server_installed ><space></data/local/tmp>

– Give permissions to frida-server :
adb shell chmod 777 /data/local/tmp/ frida-server-12.8.7-android-x86
4. Setup BurpSuite:
Follow the below given URL for detailed setup:
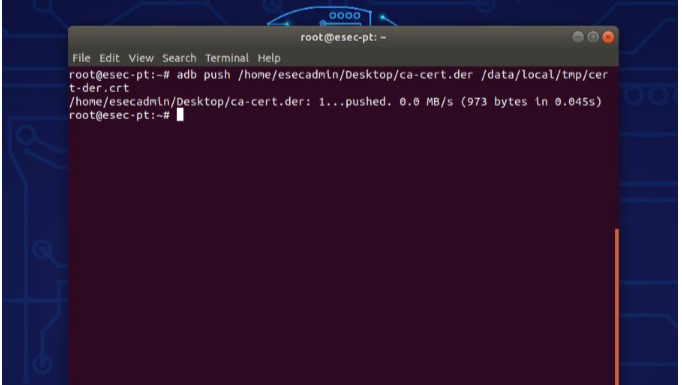
5. Pushing the proxy’s CA Certificate:
To intercept the traffic, Frida needs to have access to BurpSuite’s CA certificate. Push the certificate into the device and into the same location as the frida-server, name it cert-der.crt as this name and path has been already mentioned in fridascript.js to avoid any issues.
adb push <path to ca-cert.der> /data/local/tmp/cert-der.crt

6. Script injection to bypass SSL Pinning:
– Push fridascript.js into device:
Copy fridascript.js into adb folder and run the following command to push fridascript.js into device.
adb push <path_to_fridascript.js_folder> /data/local/tmp
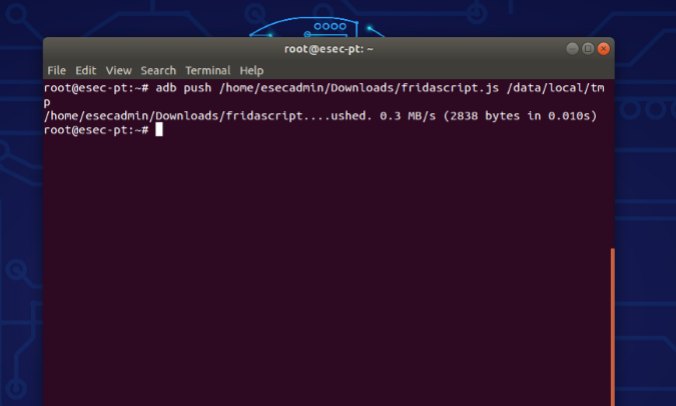

– Check and run frida server in device:
adb shell /data/local/tmp/frida-server &
– List all running processes on device:
We need to find out id of our target application. It will list all the running services on devices including your target application. Open new terminal and type the following command:
frida-ps -U
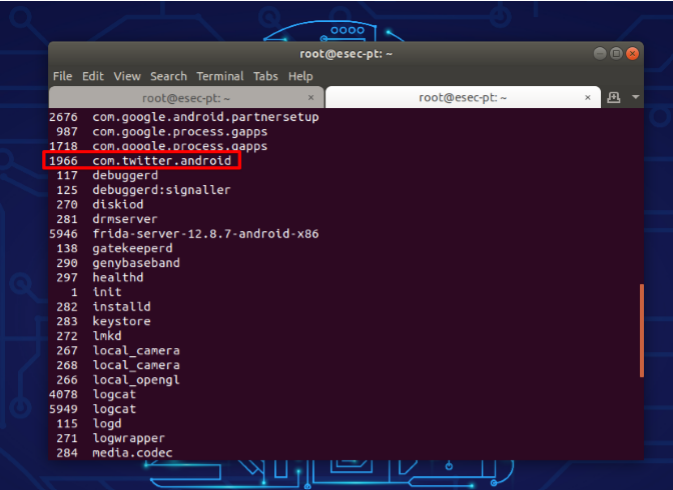

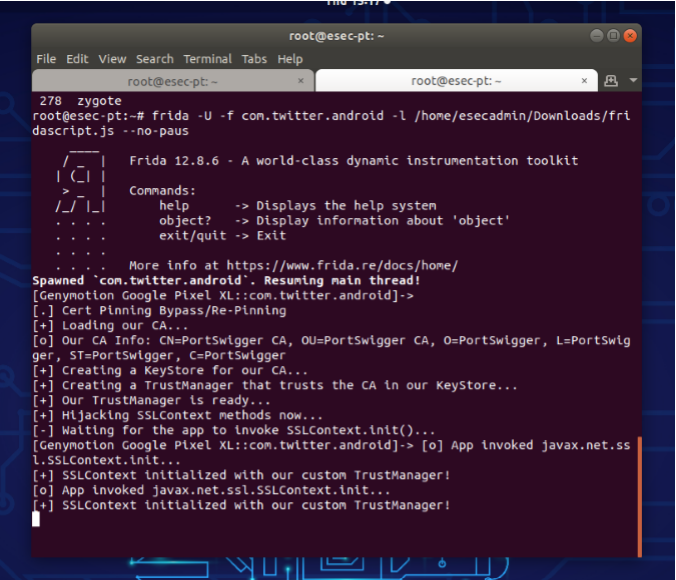
– Hook fridascript.js into target application:
frida -U -f <your_application_package_name> -l <path_to_fridascript.js_on_your_computer> –nopaus

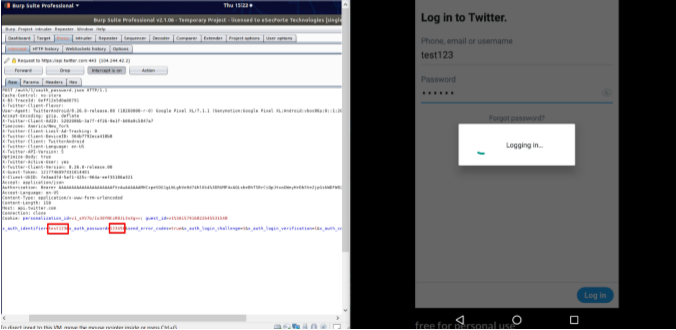
– Bypassed
Once all things go well, all traffic of the target app will get intercepted into BurpSuite. But we need to keep frida server on as long as we are intercepting the traffic into BurpSuite.

Prepared By :- Rashika Varshney
Reviewed By :- Vaibhav Rai
Approved By :- Saurabh Seth
