

HTML Injection vulnerability in SolarWinds web help Desk
INTRODUCTION
eSecForte Technologies Security Researcher – Abhinav Khanna found HTML Injection vulnerability in the Solarwinds Web Help Desk and it has been assigned CVE-2019-16954 by the MITRE.
Solarwinds Web Help Desk centralizes and automates ticketing management tasks so you can better support your customers. Keep track of tasks, including ticket assignment, routing, and escalation. Link incident tickets to a single problem for better organization, associate problem tickets with IT assets, and track the history of asset service requests.
Description:
HTML injection is a type of injection vulnerability that occurs when a user is able to control an input point and is able to inject arbitrary HTML code into a vulnerable web page.
Impact:
- Disclosure of a user’s session cookies.
- Modify the page content seen by the victims.
- Can be chained with CSRF attacks.
Recommendation:
- Your script should filter metacharacters from user input.
Steps to Reproduce:
1. Login using valid credentials.
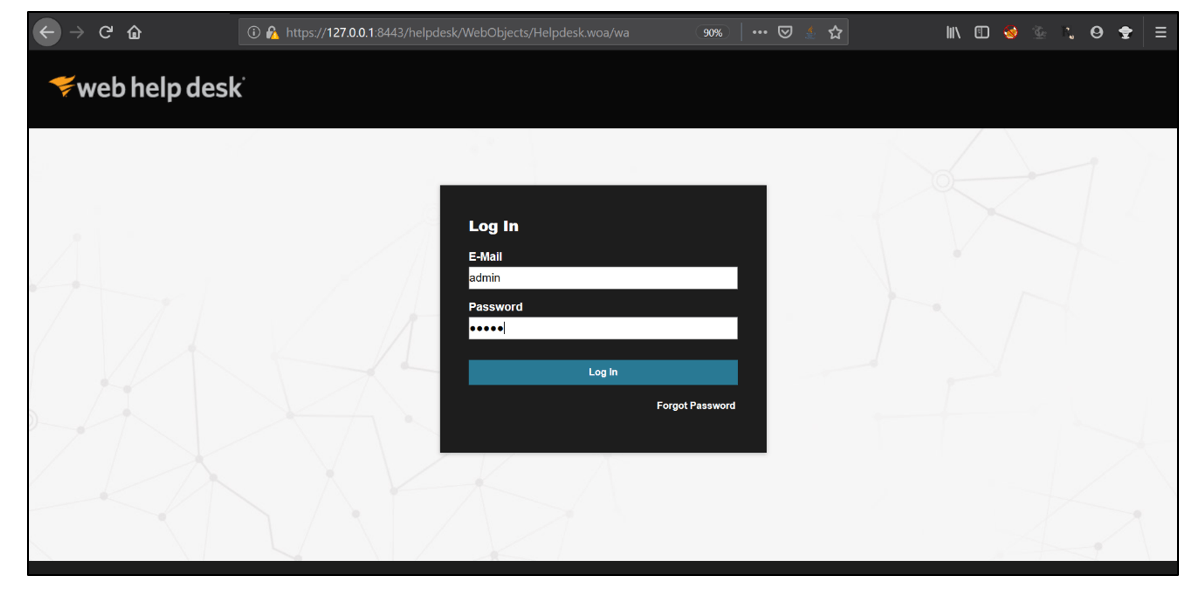

2. After logging in, click on Switch to Client account button.
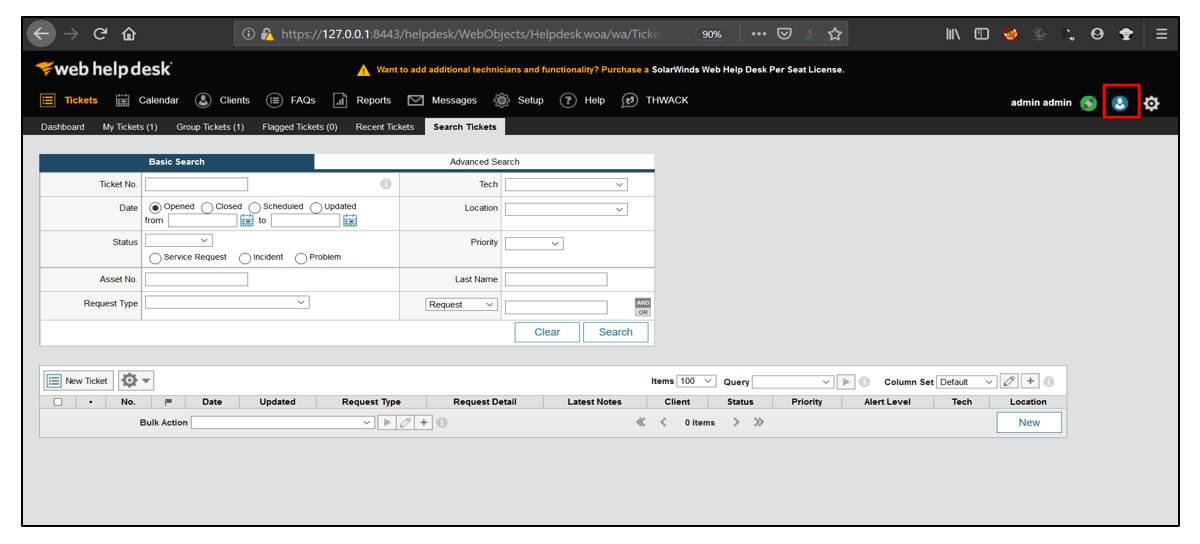

3. Then, fill the Help Request form and click on Save.
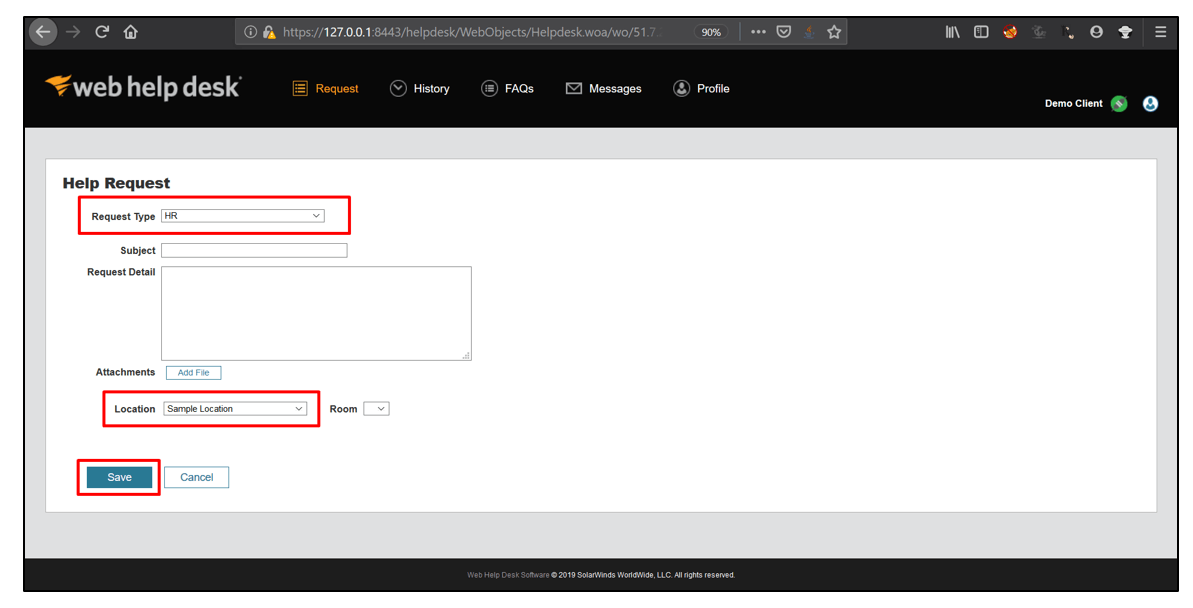

4. Note the ticket number provided and click on History.
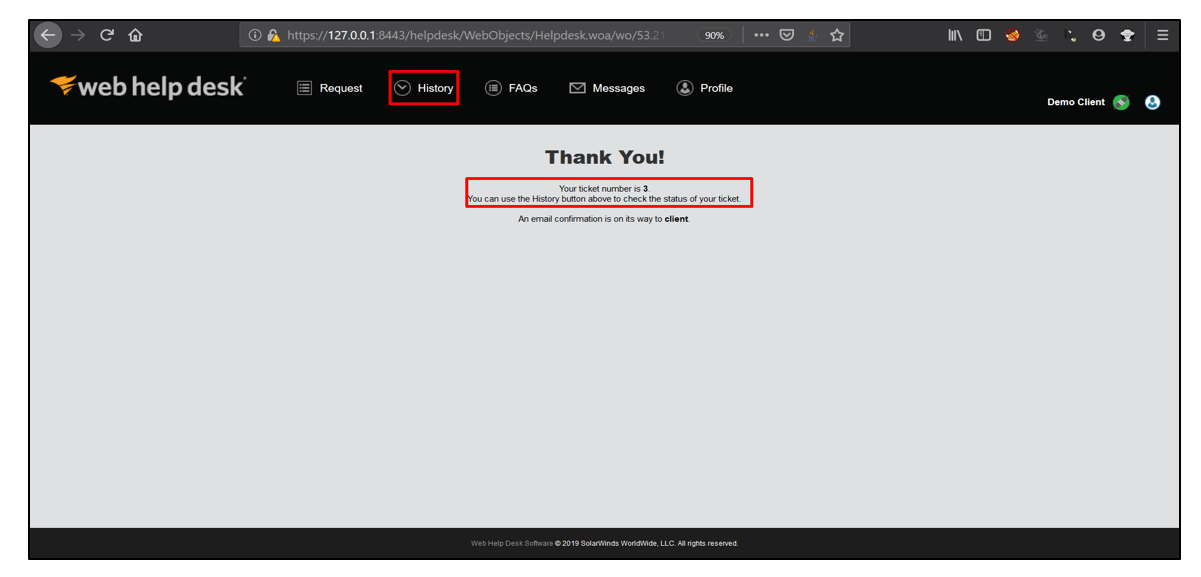

5. Click on ticket number provided to you. In the Comment box, write <s>hello</s> and click on + button.
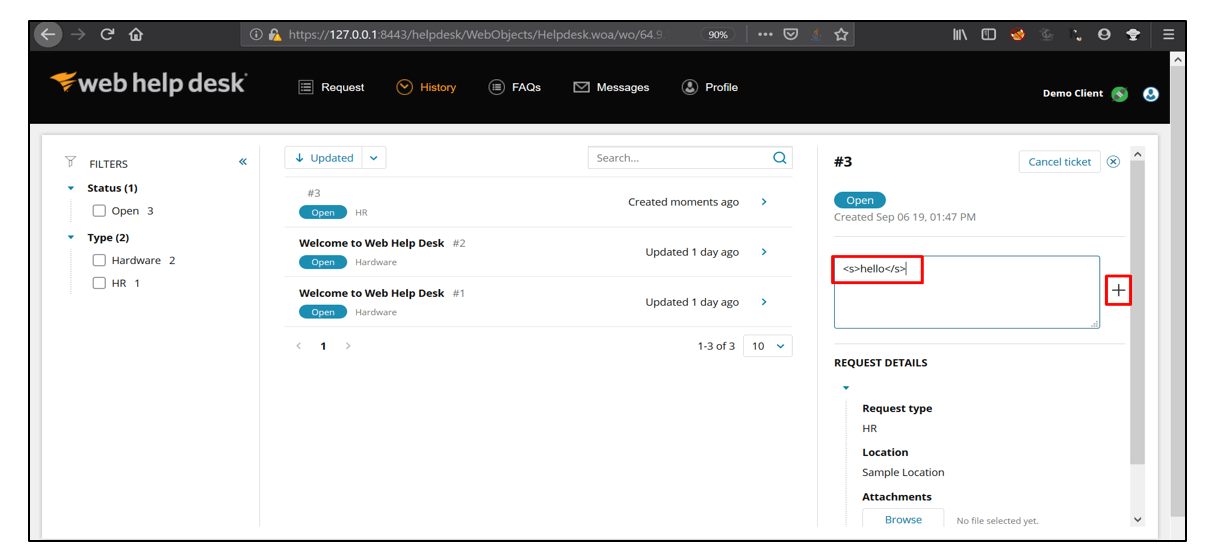

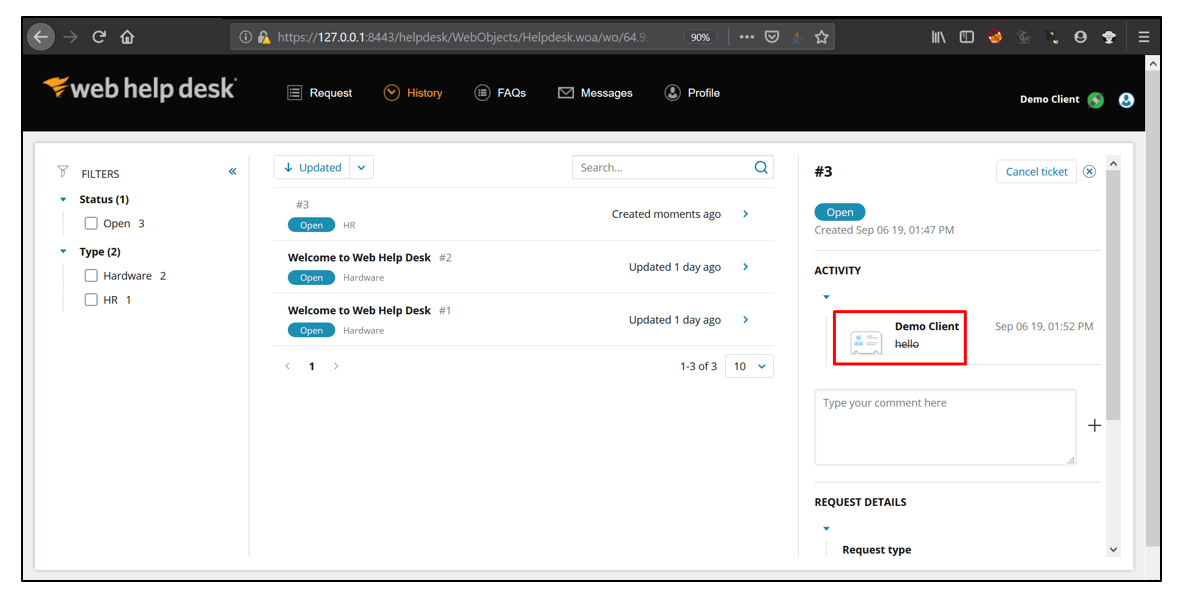
6. The HTML Injection payloads gets executed successfully

Disclosure Process
- Reported the Vulnerability to the Vendor Security or PSIRT Team.
- Acknowledged confirmed from the Vendor that vulnerability exists.
- CVE has been filed in NVD.
- The vendor confirms that the vulnerability is fixed or the latest version, the patch is released.
- Vulnerability disclosed to the public.
Reference
https://www.solarwinds.com/web-help-desk
https://www.acunetix.com/vulnerabilities/web/html-injection/
[Has vendor confirmed or acknowledged the vulnerability?]
Yes
Discoverer
Abhinav Khanna from eSec Forte Technologies Pvt Ltd
