

HTML Injection vulnerability in Manage Engine DesktopCentral UEM solution
INTRODUCTION
eSecForte Technologies Security Researcher – Abhinav Khanna found a HTML Injection vulnerability in the Manage Engine DesktopCentral and it has been assigned CVE-2019-16962 by the MITRE.
Manage Engine DesktopCentral is a Unified Endpoint Management (UEM) solution that helps manage servers, desktops, virtual machines, mobile phones, tablets, Its features includes Patch Management, Software Deployment, Remote Desktop Sharing, IT Asset Management, Desktop Configurations, Service Pack Installation, Active Directory Reports, User Administration, Mobile Device Management and many more.
Description:
HTML injection is a type of injection vulnerability that occurs when a user is able to control an input point and is able to inject arbitrary HTML code into a vulnerable web page.
Impact:
A possible attack scenario is demonstrated below:
- Attacker discovers injection vulnerability and decides to use an HTML injection attack
- Attacker crafts malicious link, including his injected HTML content, and sends it to a user via email
- The user visits the page due to the page being located within a trusted domain
- The attacker’s injected HTML is rendered and presented to the user asking for a username and password
- The user enters a username and password, which are both sent to the attackers server
Recommendation:
- Your script should filter metacharacters from user input.
Steps to Reproduce:
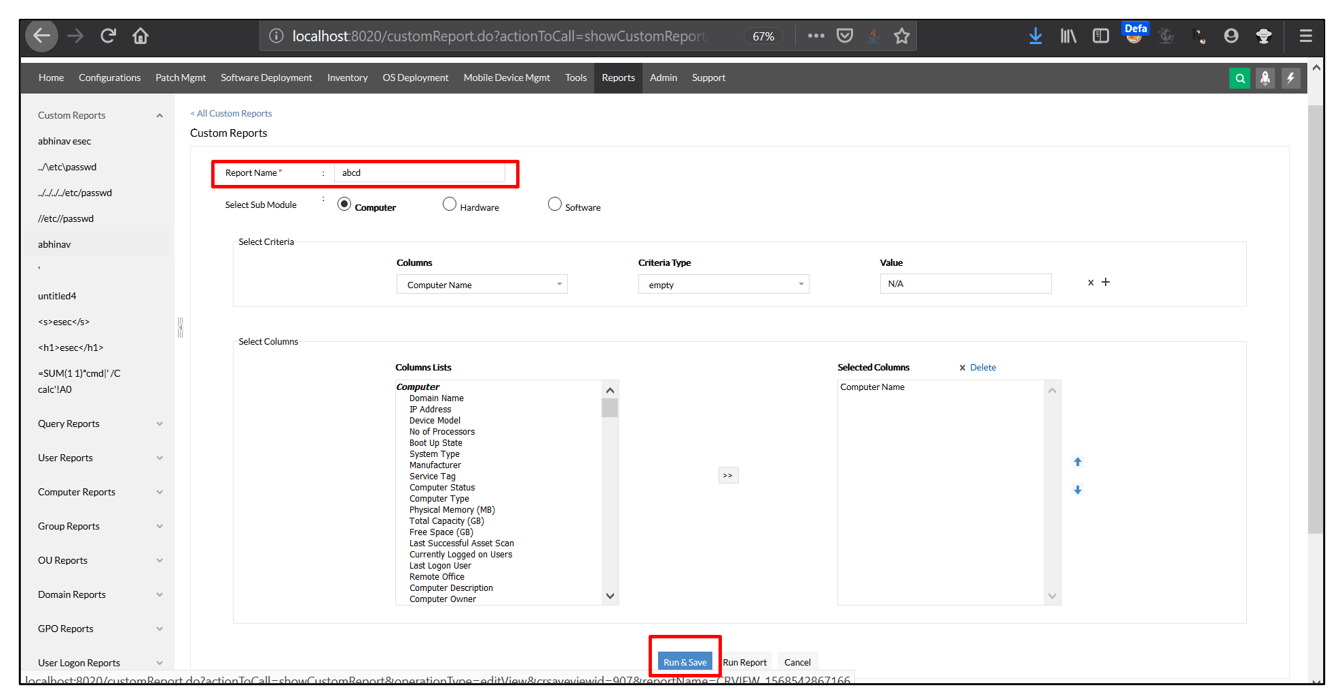
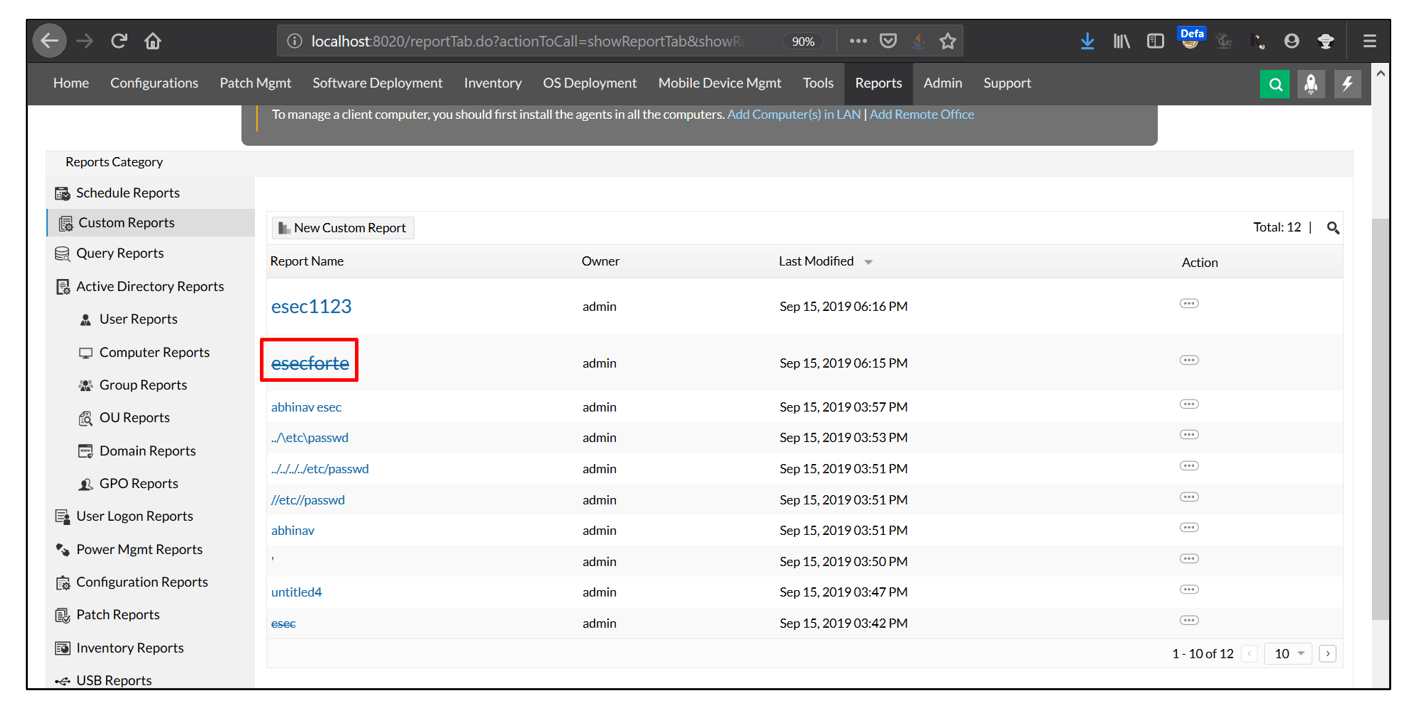
1. Login using valid credentials and go to Custom Reports



2. Create a new customer report as shown in the screenshot. Click Run&Save and intercept the request.
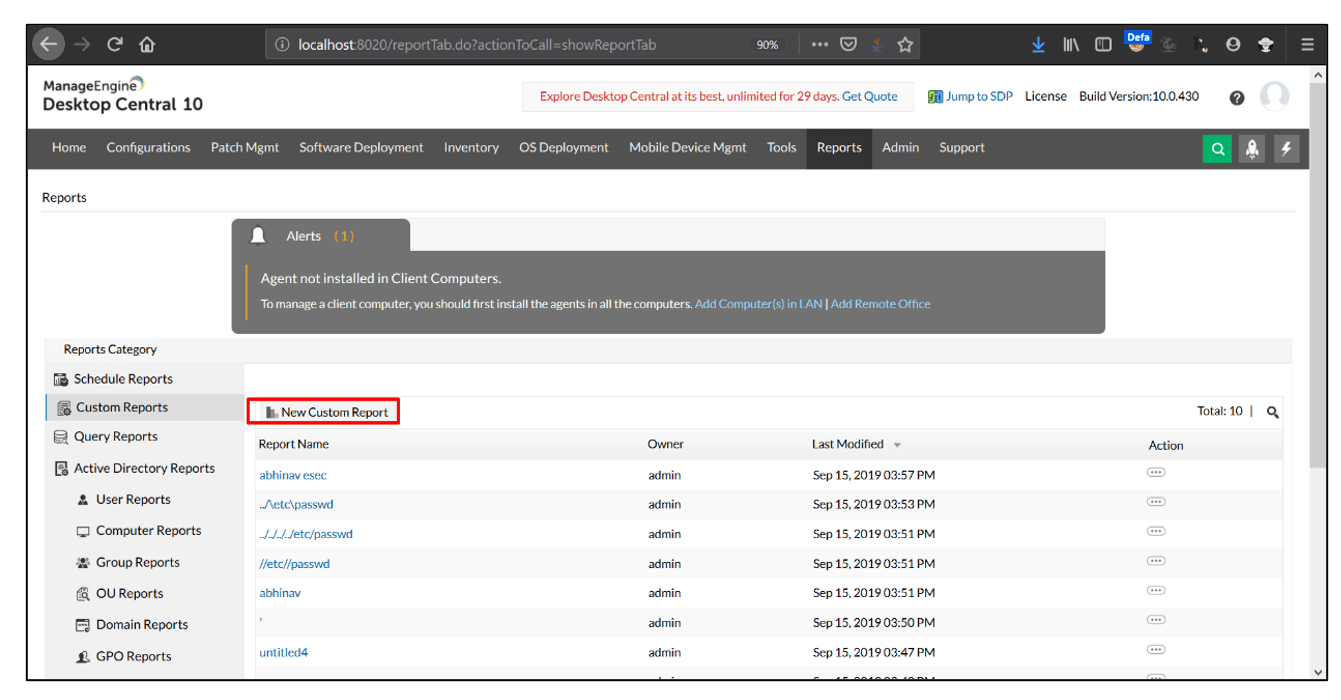




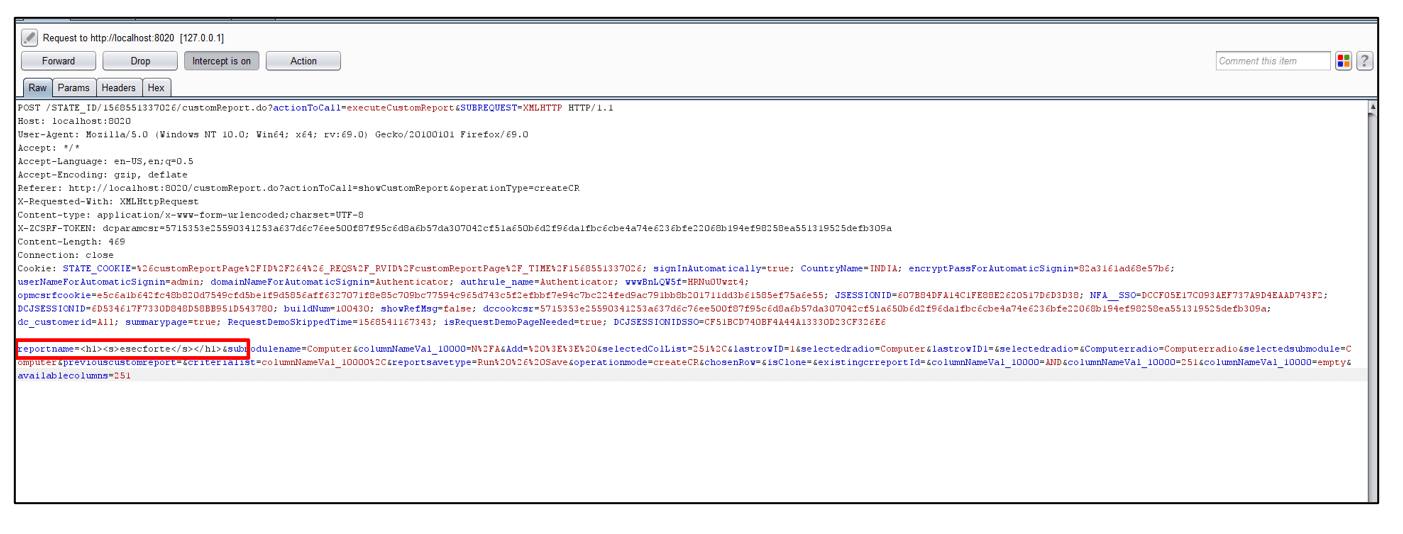
3. After intercepting the request, change the value of requestname parameter from abcd to</p> <h1><s>esecforte</s></h1> <p>.

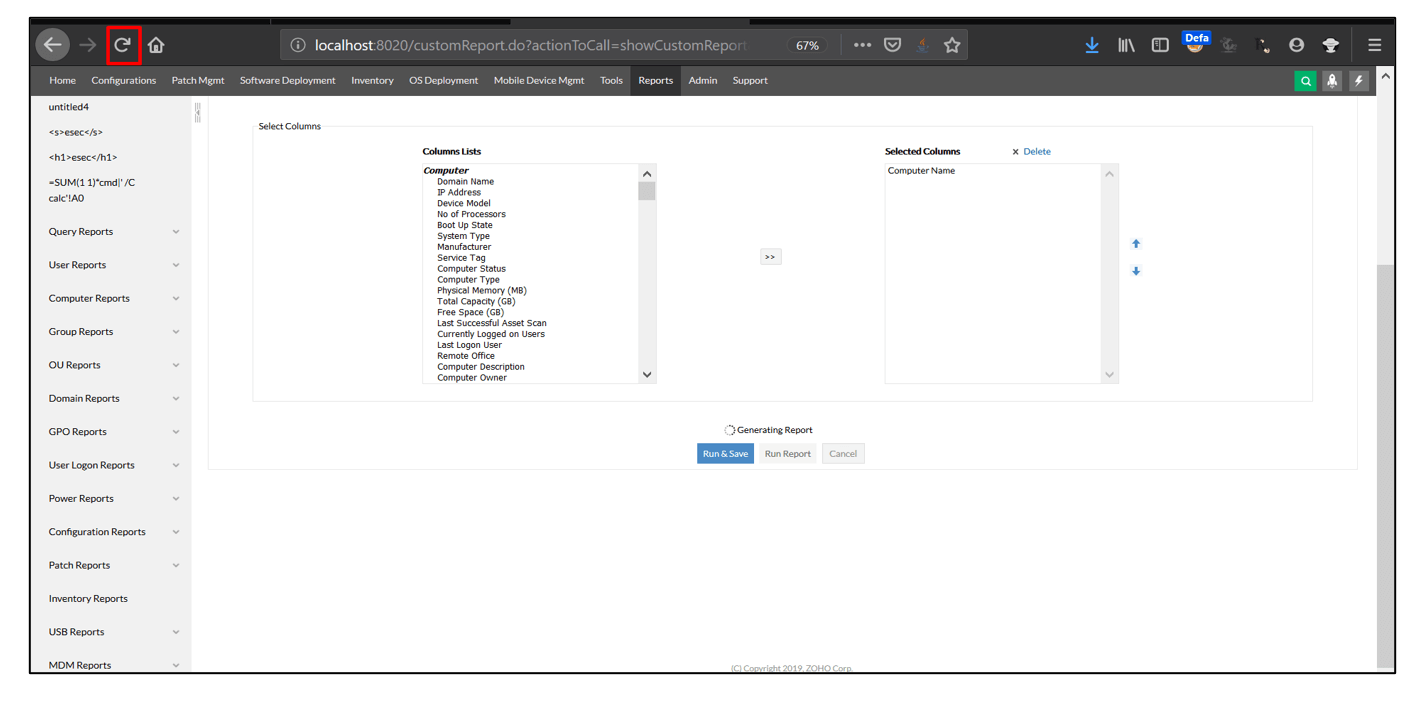
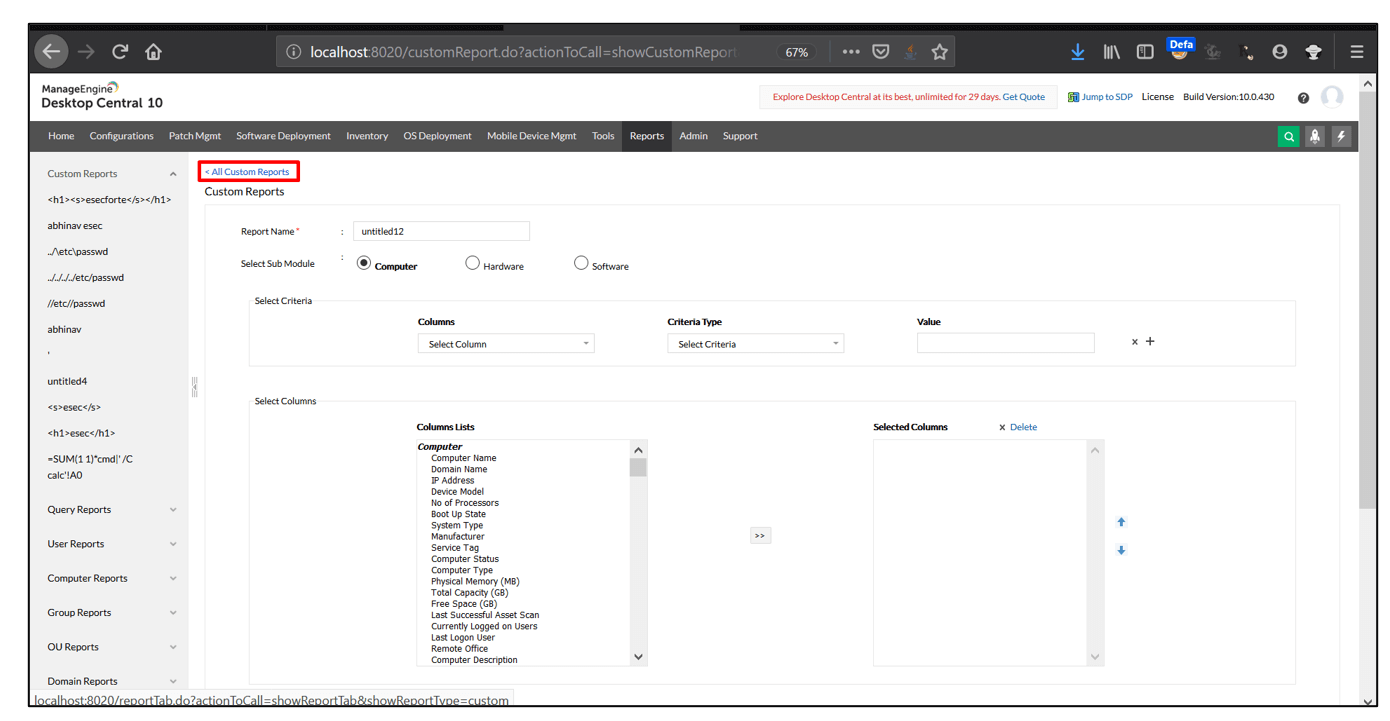
4. Open all custom reports and notice that HTML Injection payload successfully executes.



Disclosure Process
- Reported the Vulnerability to the Vendor Security or PSIRT Team.
- Acknowledged confirmed from the Vendor that vulnerability exist.
- CVE has been filed in NVD.
- Vendor confirm that the vulnerability is fixed or a latest version, patch is released.
- Vulnerability disclosed to the public.
Reference
https://www.manageengine.com/products/desktop-central/html-injection-vulnerability.html
https://www.acunetix.com/vulnerabilities/web/html-injection/
Has the vendor confirmed or acknowledged the vulnerability?
Yes
Discoverer
Abhinav Khanna from eSec Forte Technologies Pvt Ltd
