

Cross-site scripting vulnerability in SolarWinds Web Help Desk
INTRODUCTION
Solarwinds Web Help Desk centralizes and automates ticketing management tasks so you can better support your customers. Keep track of tasks, including ticket assignment, routing, and escalation. Link incident tickets to a single problem for better organization, associate problem tickets with IT assets, and track the history of asset service requests.
eSecForte Technologies Security Researcher – Abhinav Khanna found a Cross-Site Scripting vulnerability in the Solarwinds Web Help Desk and it has been assigned CVE-2019-16960 by the MITRE.
Description:
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end-user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it.
Impact:
- Impersonate or masquerade as the victim user.
- Carry out any action that the user is able to perform.
- Read any data that the user is able to access.
- Capture the user’s login credentials.
- Perform virtual defacement of the website.
- Inject Trojan functionality into the website.
Recommendation:
- To prevent XSS in HTTP responses that aren’t intended to contain any HTML or JavaScript, you can use the Content-Type and X-Content-Type-Options headers to ensure that browsers interpret the responses in the way you intend.
- Properly validate the data that is entered by the end-user on both client-side and server-side.
- Use Content Security Policy to reduce the impact of Cross-Site Scripting, in case the vulnerability exists.
Steps to Reproduce:
1. Open the application and login using valid credentials.

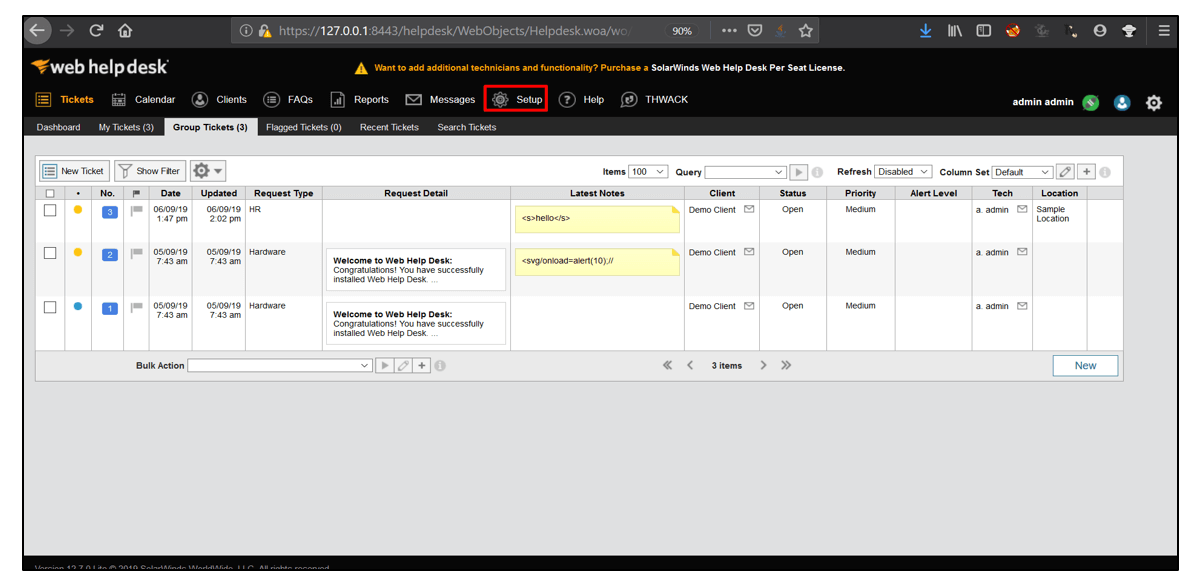
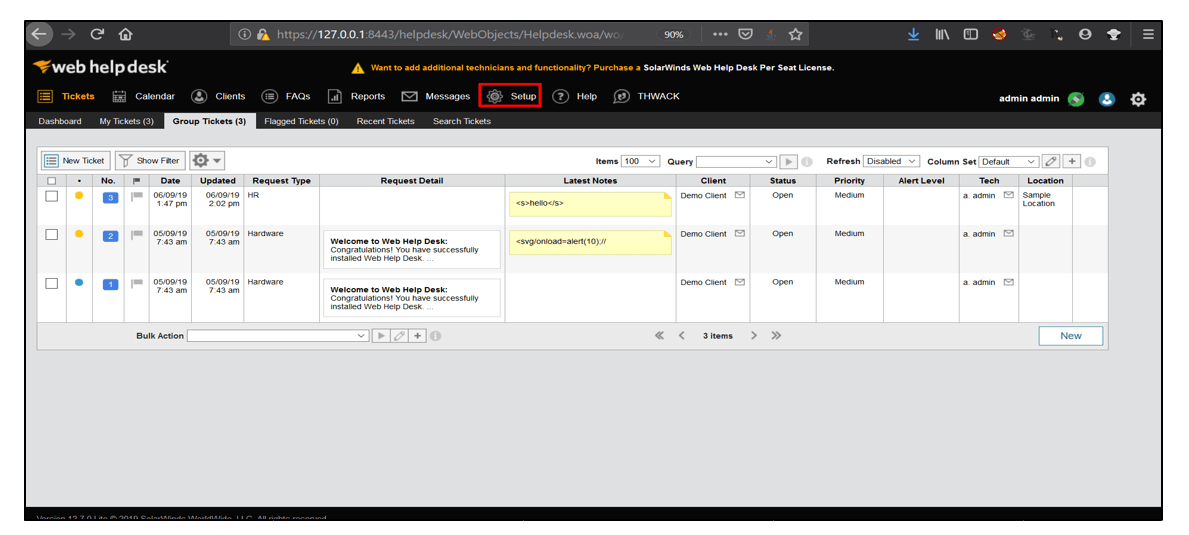
2. After logging in, go to Setup.

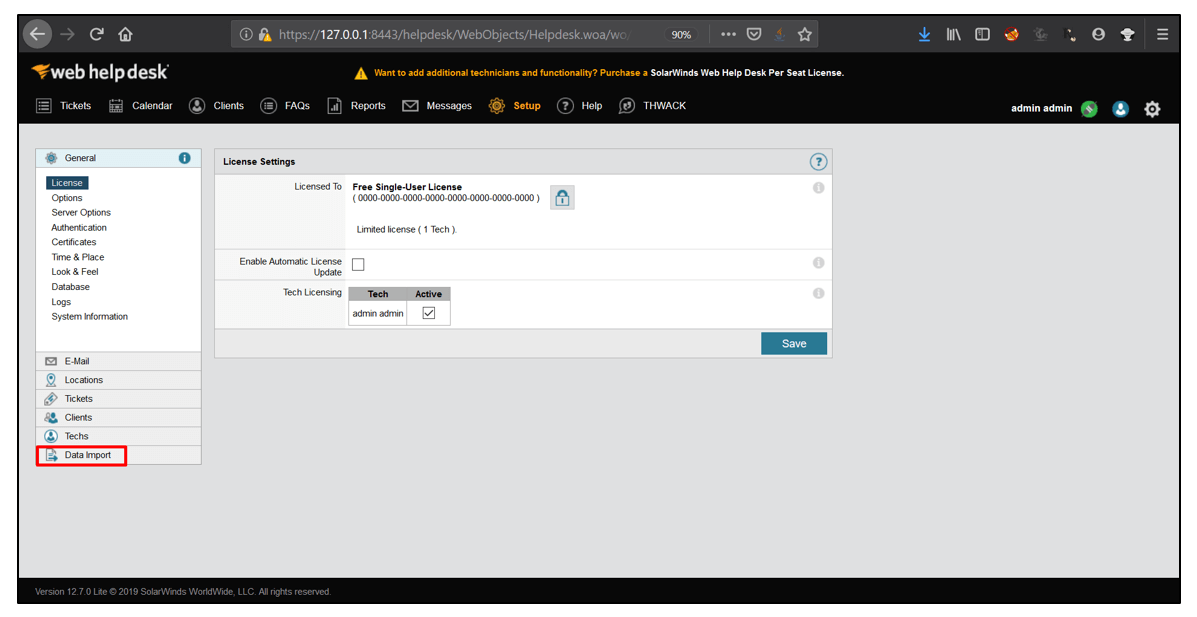
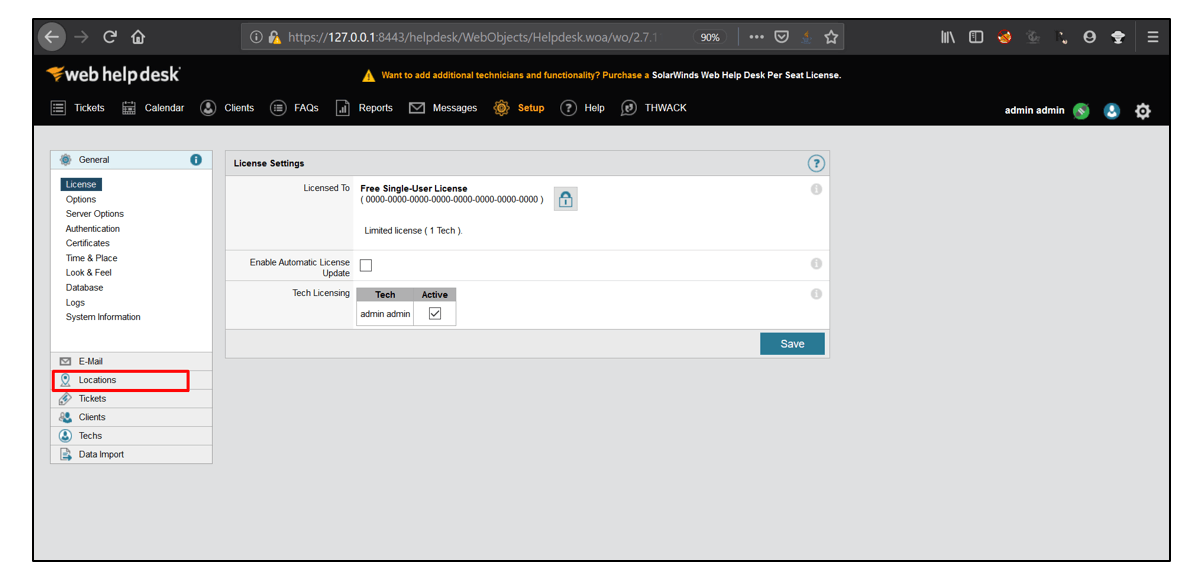
3. Then, Select Data Import and click on Import Locations.

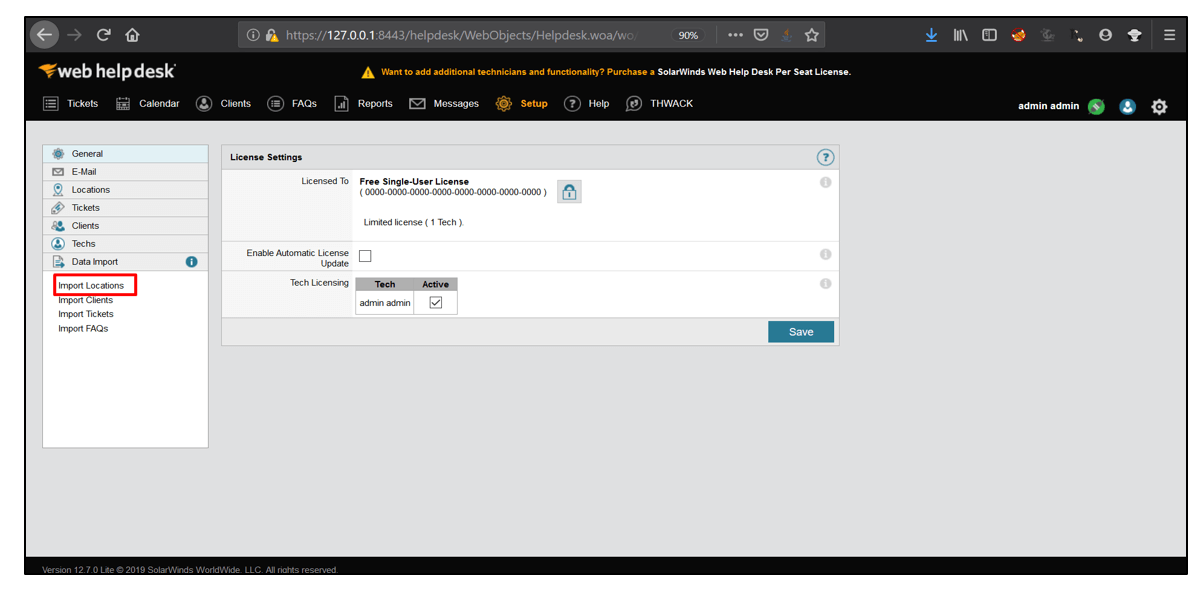

4. For Sync Based on parameter, select Location Name from the drop-down options. For Client Key, select E-Mail from drop-down options. Select the File Type as Comma Separated(CSV). Now, click on Download Template.
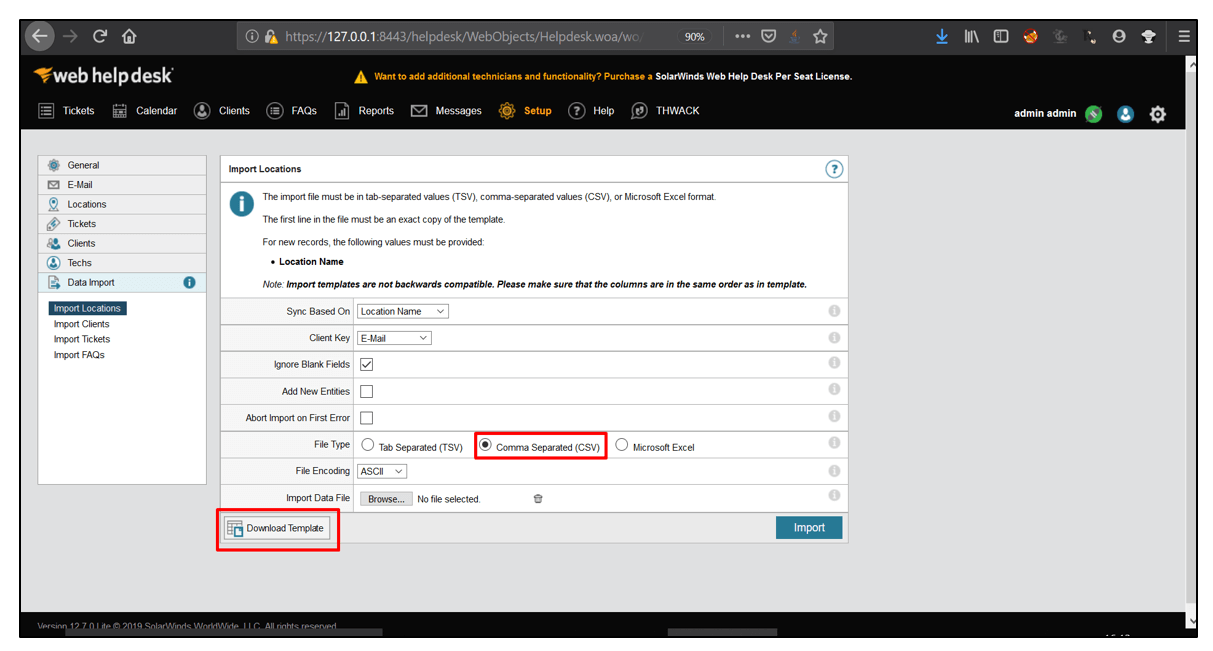

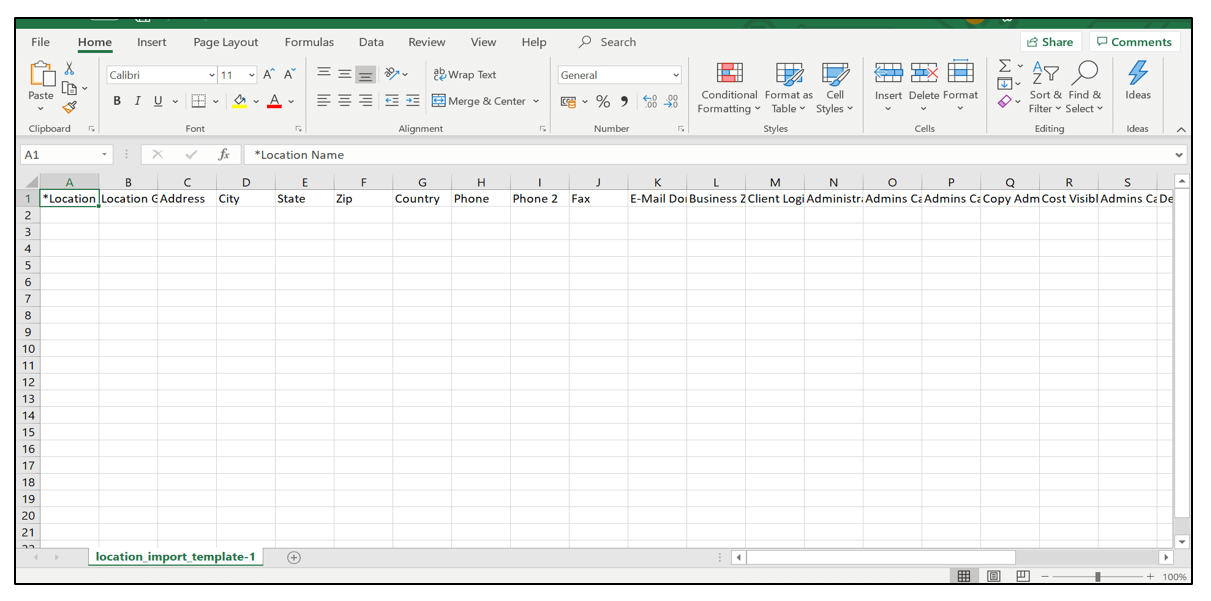
5. Now, edit the template and insert XSS payload in it as shown below.

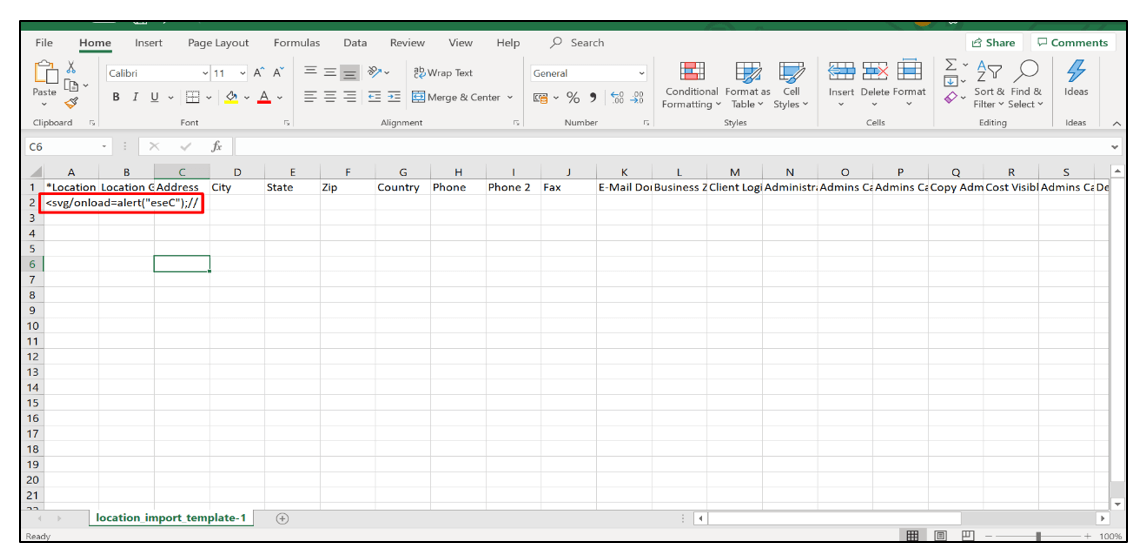

6. Now, upload the file and click on Import. Then, log out and log in again.
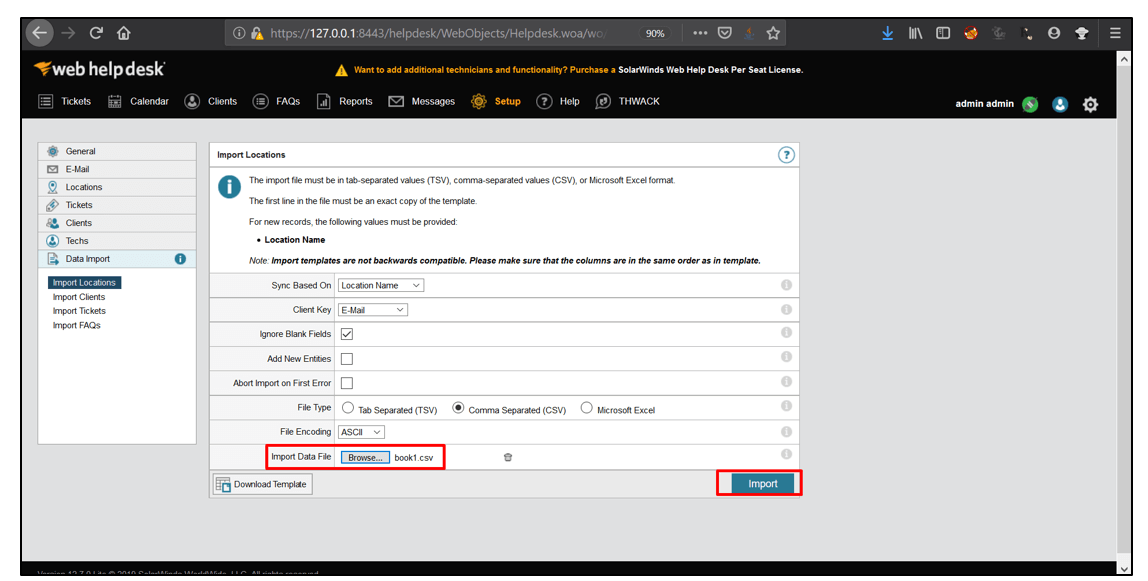



7. After logging in, go to Setup, select Locations and click on Locations & Rooms.


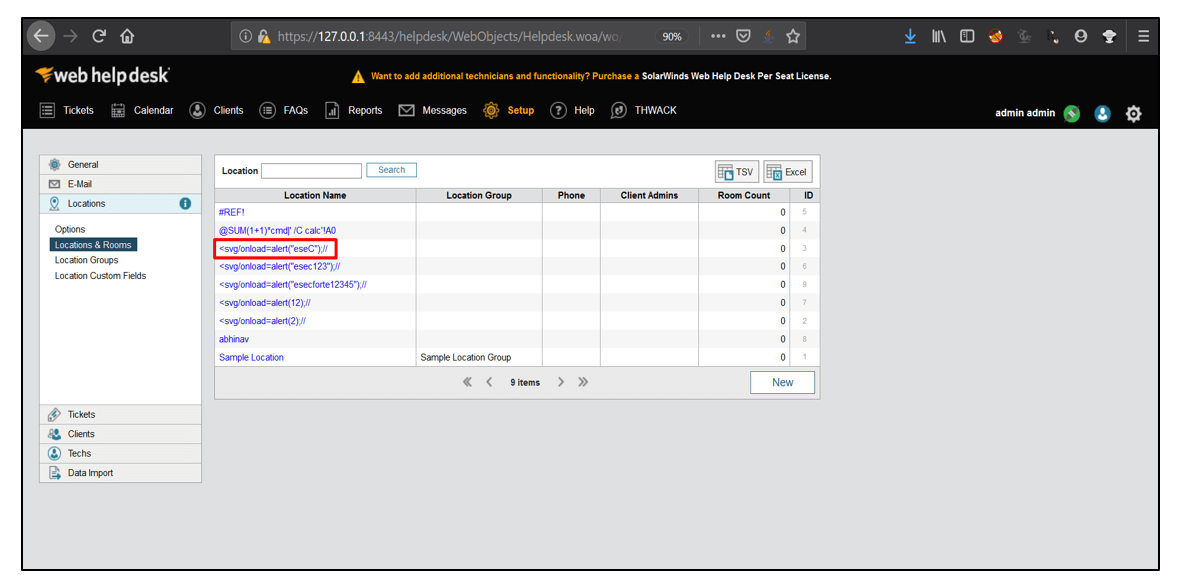

8. Click on <svg/onload=alert(“eseC”);// . It was imported from the CSV file. The XSS payload gets executed successfully as shown below.
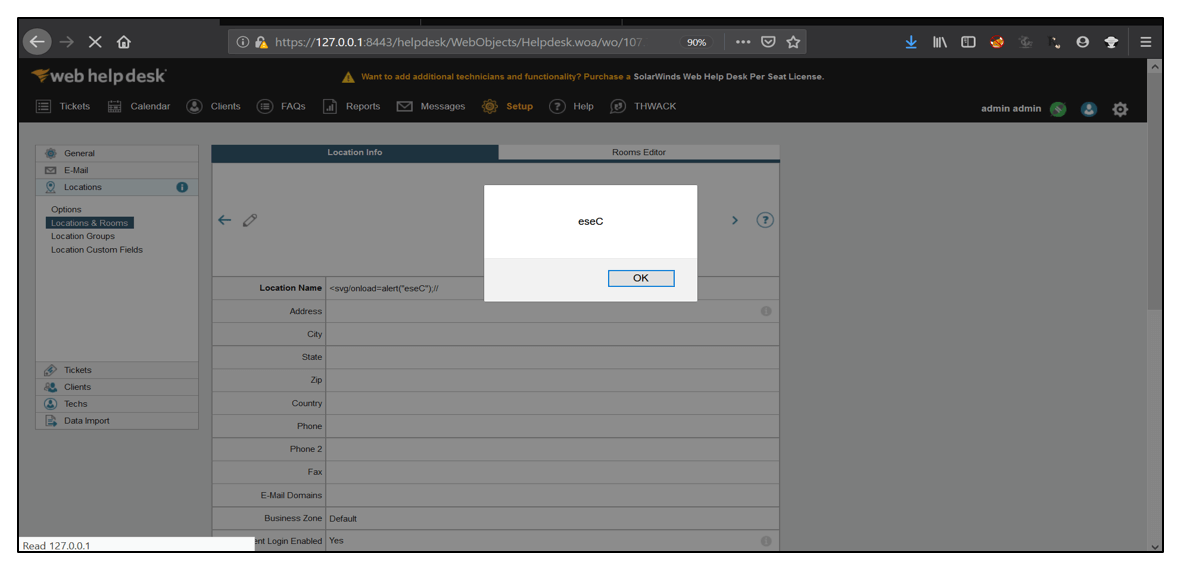

[Disclosure Process]
- Reported the Vulnerability to the Vendor Security or PSIRT Team.
- Acknowledged confirmed from the Vendor that vulnerability exists.
- CVE has been filed in NVD.
- The vendor confirms that the vulnerability is fixed or the latest version, the patch is released.
- Vulnerability disclosed to the public.
[Reference]
https://www.solarwinds.com/web-help-desk
https://csrc.nist.gov/glossary/term/Cross_site_Scripting
[Has the vendor confirmed or acknowledged the vulnerability?]
Yes
[Discoverer]
Abhinav Khanna from eSec Forte Technologies Pvt Ltd
