SYSTEM SECURITY
System Security: Overview
eSec Forte’s system security solution includes creating a protection net for the entire computer system such as the CPU, disk, memory, software and stored data. If an operating system is run by an unauthorized user, it may severely damage the system. To prevent this, we offer protection against unauthorized access, viruses, worms, malicious access to the system memory and so on. We cover areas such as authentication, passwords, program and system threats.


System Security: Challenges
Even the most private network server needs to maintain at least one connection with the outside world. Be it a website, email server, or a backup repository, a 24 hour connection must be open to the outside world. Even the biggest of enterprises face security issues in their operating systems as patches issued for vulnerabilities are discovered later. An attacker can easily exploit these vulnerabilities, steal information, and run ransomware in the operating system.
How can we help?
We at eSec Forte set up security traps that can disrupt an attack before it can impact an
endpoint by implementing multiple methods of prevention. Our system security tools block
security breaches that attempt to leverage exploits and malware, both known and unknown,
before they can impact the operating system. Our system security encompass all
steps needed to safeguard the OS from viruses, threats, malware, worms and remote hackers.
Our team adopts all techniques for preventive control to safeguard all computer assets
Features of our System Security
Benefits of our System Security
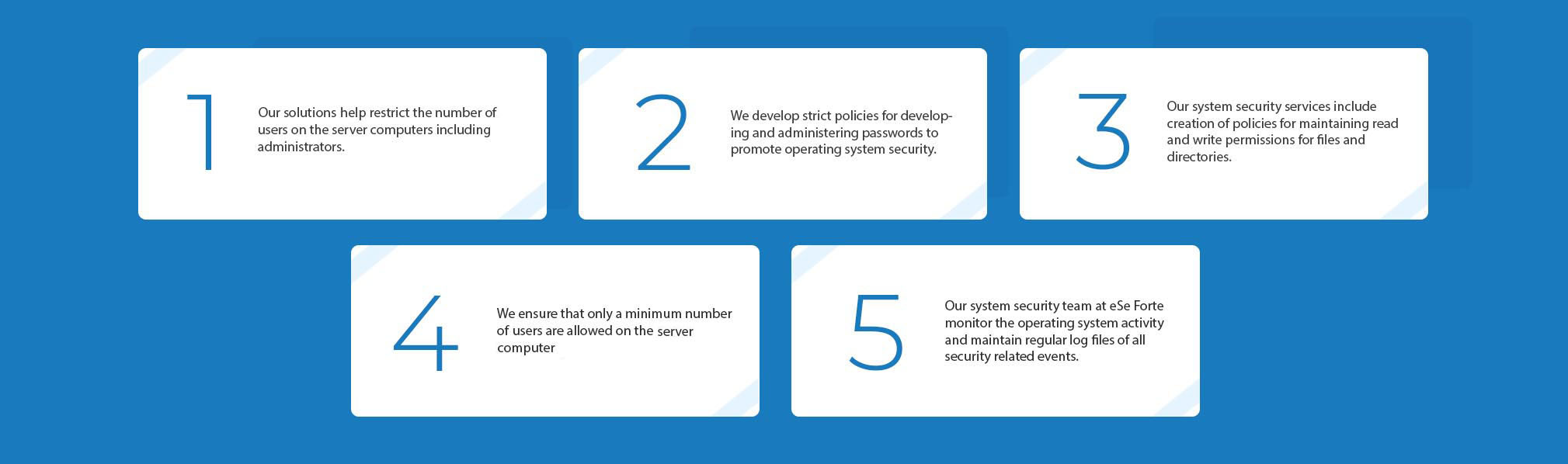

5 W’s of System Security
1. What are the most common security requirements of an operating system?
The most common security needs of an operating system are performing OS patch updates, installing antivirus software, monitoring network traffic and securing accounts with privileges.
2. How does it protect my operating system?
Our solution ensures optimal security of your operating system through regular software updates, updated antivirus software, multi-layered security policies for user accounts and regular system backups.
3. Why is operating a security system important for my business?
Operating it ensures that all your computer system resources including CPU, memory, disks and software programs are safeguarded against unauthorized access, malicious attacks, worms and viruses.
4. What are the various types of operating system?
The types of operating system are Batch OS, Time-sharing OS, Distributed OS, Network OS and Real-time OS.
5. What does the OS hardening feature of your solution achieve?
We perform OS hardening to avoid maximum security vulnerabilities in the OS by removing non-essential software programs from the system.



































