Pentesting Networks for weak passwords using Metasploit
Basic Test Using Metasploit Penetration Testing Tool
In the previous post on metasploit, we did a basic penetration test of a network using the WebUI of Metasploit. In this post we will see how metasploit can help us in identifying systems in a network that do not follow a strong password policy. Basically, we are going to use the scan and bruteforce option of Metasploit WebUI to accomplish this task.
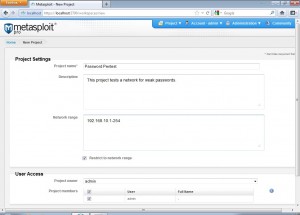
First we complete the project creation process.
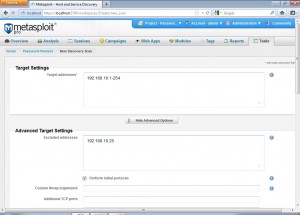
Now we click on the scan option of the discovery module and fill in all the project related settings.
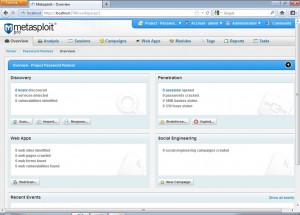
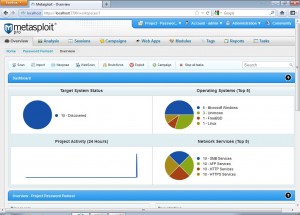
After the scan is completed, we get to the following screen which shows us all alive systems within the target network, the various top 5 operating systems found and the top 5 network services found.
Now after the basic scan is completed, we know what our target systems are with their corresponding operating systems and services, so we can start bruteforcing these systems to find weak passwords in the remote services that require authentication and were found listening on systems within the target network.
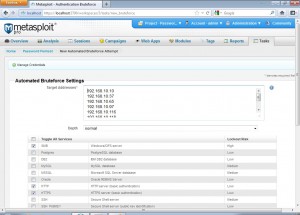
So we click the bruteforce option to start the password cracking process and we get a screen like the following.
We can choose the target addresses and services for which we want to launch the attack. Advanced users can check various options to mutate the default passwords tried in a password cracking session. This can be really helpful where users use a concatenation of easy to guess passswords. But for keeping this post simple, we only go with the default options.
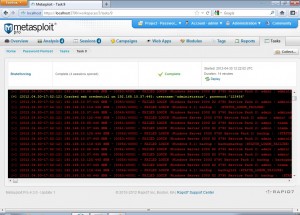
After launching the bruteforce, we will see a screen like the following
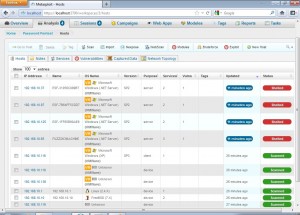
The services that were successfully compromised are highlighted with yellow. After the bruteforce session is complete, we can go to Analysis->Hosts to get the following
Metasploit Flags
As we can see. metasploit flags all the compromised hosts with “Shelled” and all the systems that were scanned but not compromised with “Scanned”.
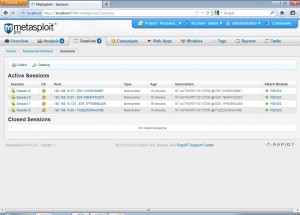
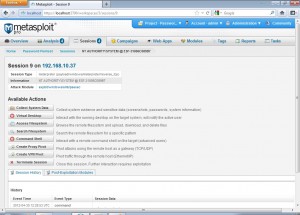
Again we go to the sessions tab to see all the details of the compromised hosts.
PSEXEC Module of Metasploit
We can see that all systems were compromised using the PSEXEC module of metasploit. Clicking on a session we see the details of that session.
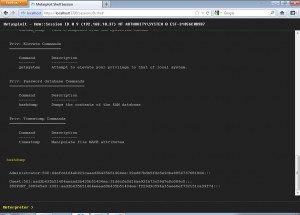
From here we can launch the command shell on the shelled target. We can use this to get the password hashdump for offline cracking purposes.
Basic Password Cracking Session Using Metasploit
This was a basic password cracking session using Metasploit WebUI. Quite easy and time saving, right :
eSecForte is the Authorized Reseller of Rapid7 Security Products in India, Bangladesh & Srilanka
See More eSecForte’s Information Security Solutions :-
- Metasploit Professional – Penetration Testing Tool
- Nexpose – Vulnerability Management Software
- InsightIDR- Detection and Investigation Solution
- Appspider – Desktop Web App Security Scanner Tool
- Burp Suite- Web Security Testing Software
- Vulnerability Scanning and Vulnerability Management
- Vulnerability Assessment and Penetration Testing (VAPT)
We Want to Hear from You !!
Contact us today to learn more about our products and services.