

Formula Injection vulnerability in Solarwinds Web Help Desk
INTRODUCTION
eSecForte Technologies Security Researcher – Abhinav Khanna found Formula Injection vulnerability in the Solarwinds Web Help Desk and it has been assigned CVE-2019-16959 by the MITRE.
Solarwinds Web Help Desk centralizes and automates ticketing management tasks so you can better support your customers. Keep track of tasks, including ticket assignment, routing, and escalation. Link incident tickets to a single problem for better organization, associate problem tickets with IT assets, and track the history of asset service requests.
Description: Formula Injection vulnerability
It occurs when the data in the file is not properly validated prior to export. The attacker usually injects a malicious payload or formula into the input field. Once the data is exported and the file is opened, the spreadsheet application executes the malicious payload on the assumption of a standard macro.
Impact:
A possible attack scenario is demonstrated below:
- Hijacking the user’s computer by exploiting vulnerabilities in the spreadsheet software, such as CVE-2014-3524
- Hijacking the user’s computer by exploiting the user’s tendency to ignore security warnings in spreadsheets that they downloaded from their own website
- Exfiltrating contents from the spreadsheet, or other open spreadsheets.
Recommendation:
This attack is difficult to mitigate and explicitly disallowed from quite a few bug bounty programs. To remediate it, ensure that no cells begin with any of the following characters:
- Equals to (“=”)
- Plus (“+”)
- Minus (“-“)
- At (“@”)
Steps to Reproduce:
1. Open the application and login using valid credentials.

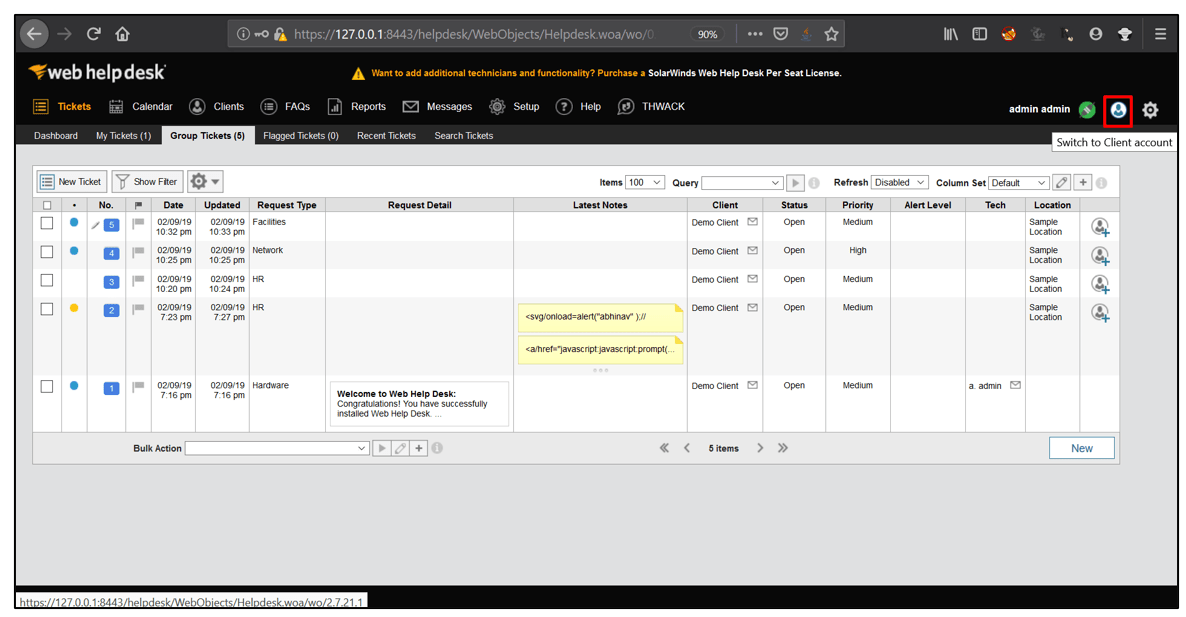
2. After logging in, click on the Switch to Client account button.

3. Then, select the values for Request Type and Location parameters from their drop down options and click on Add File. Select the file and then click on Upload

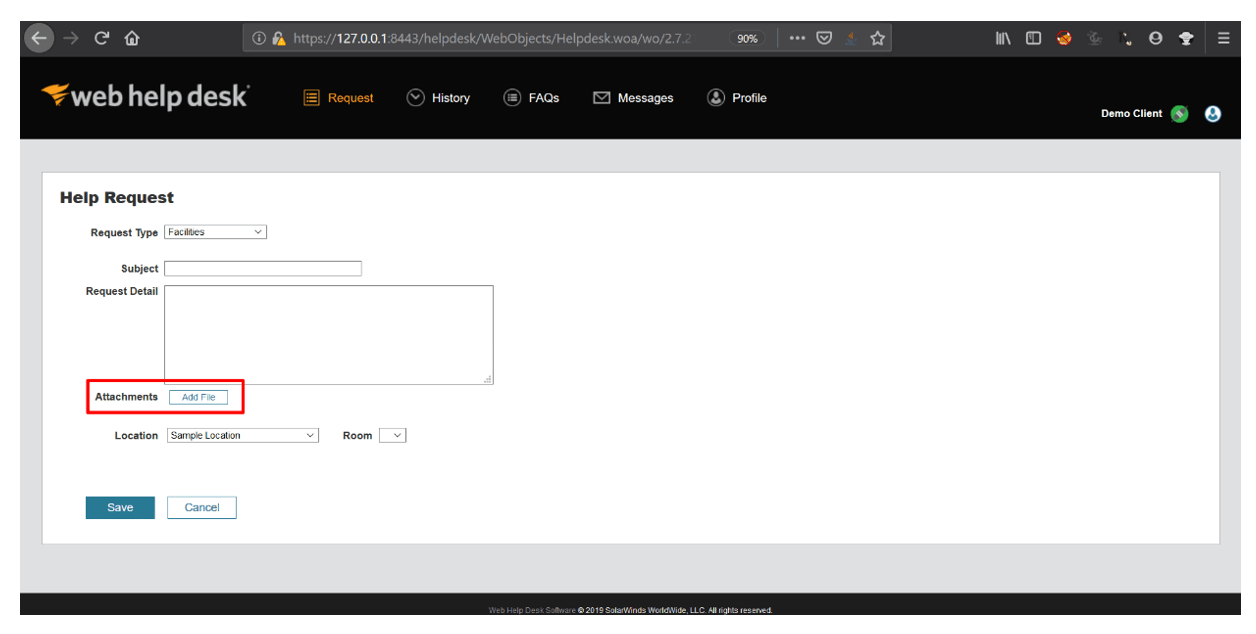

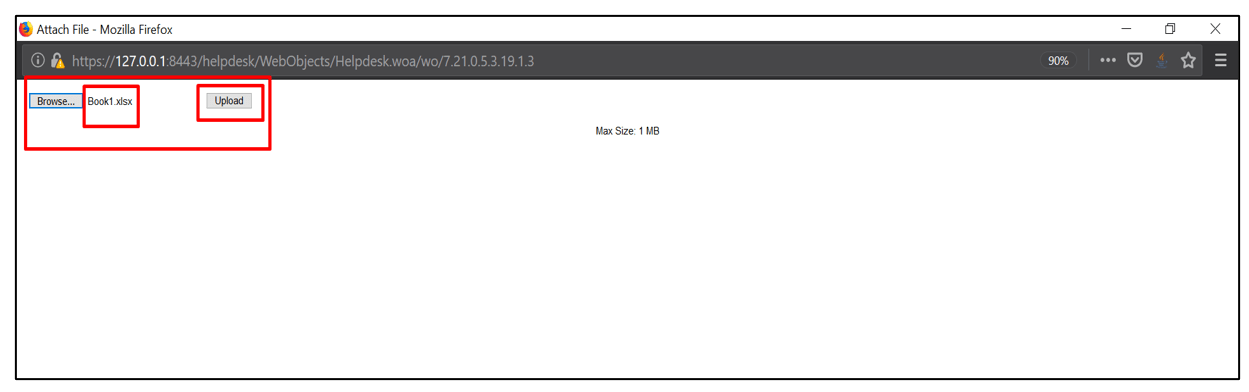

4. After uploading the file, click on save.
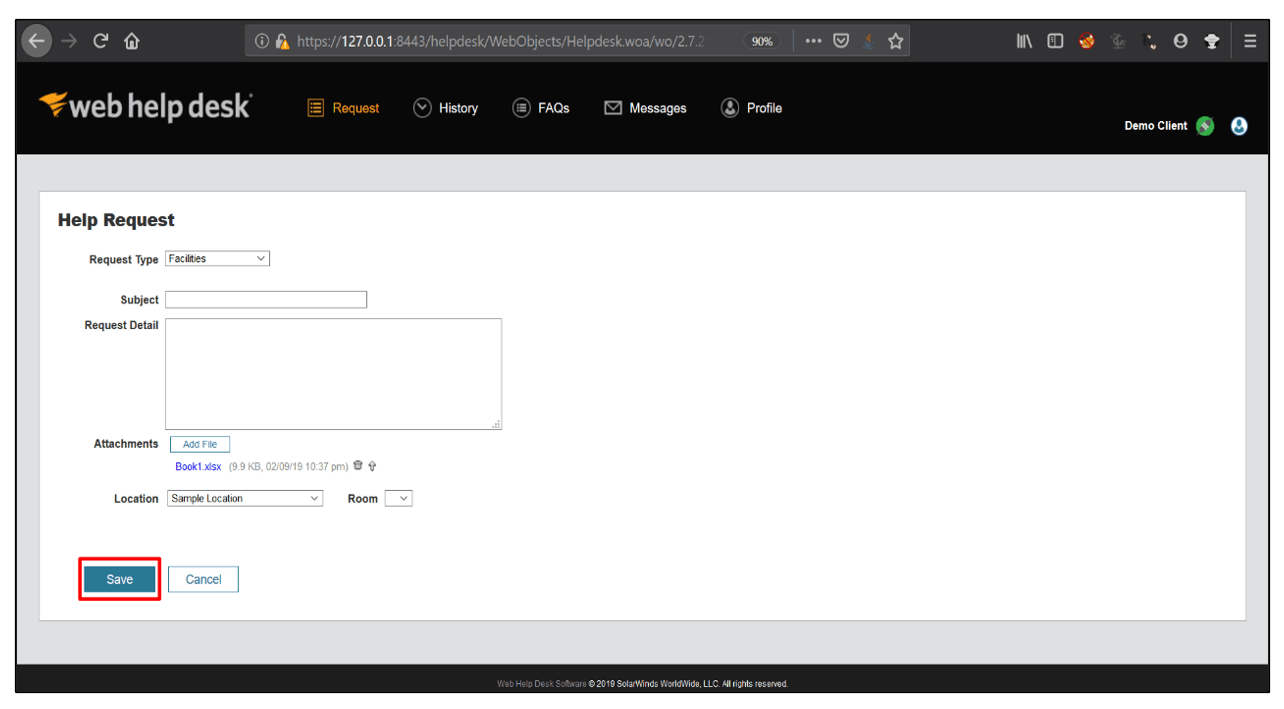

5. Then, note the ticket number and click on Switch to Tech account button.
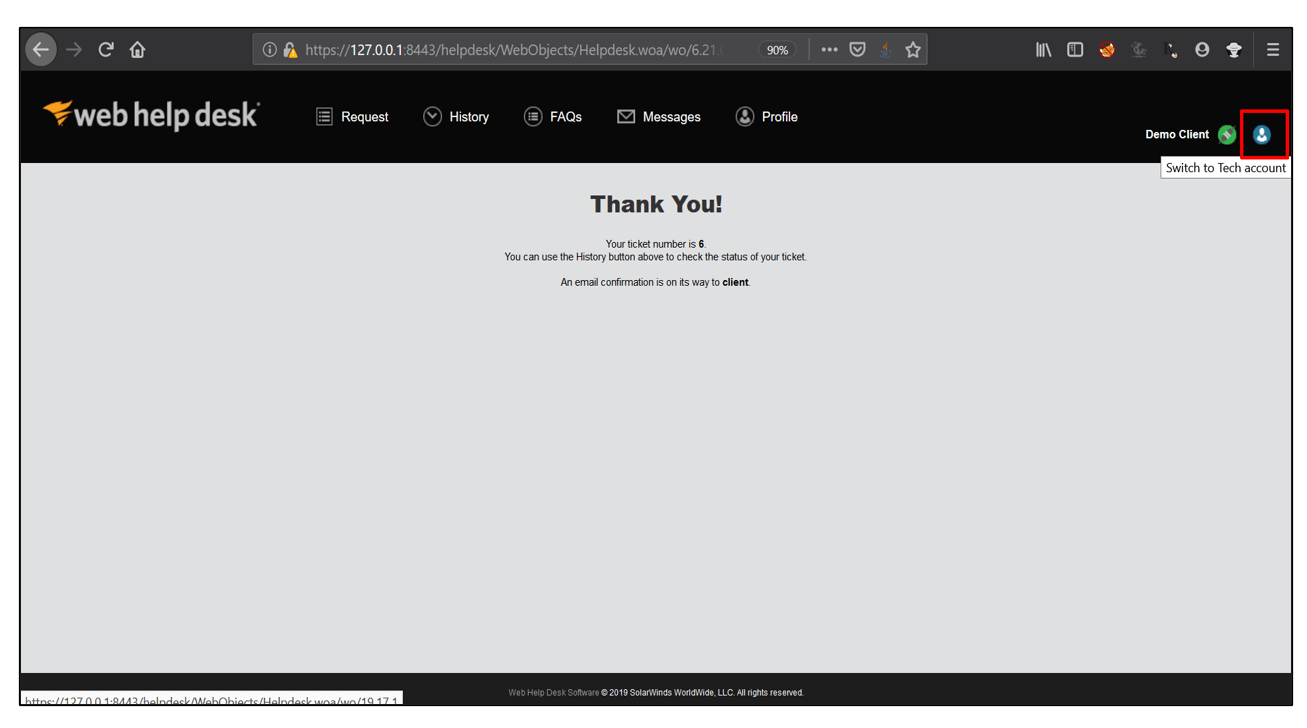

6. Now, click on Tickets and select Group Tickets, open the ticket with the ticket number you noted. Now, open the file attached with the ticket.
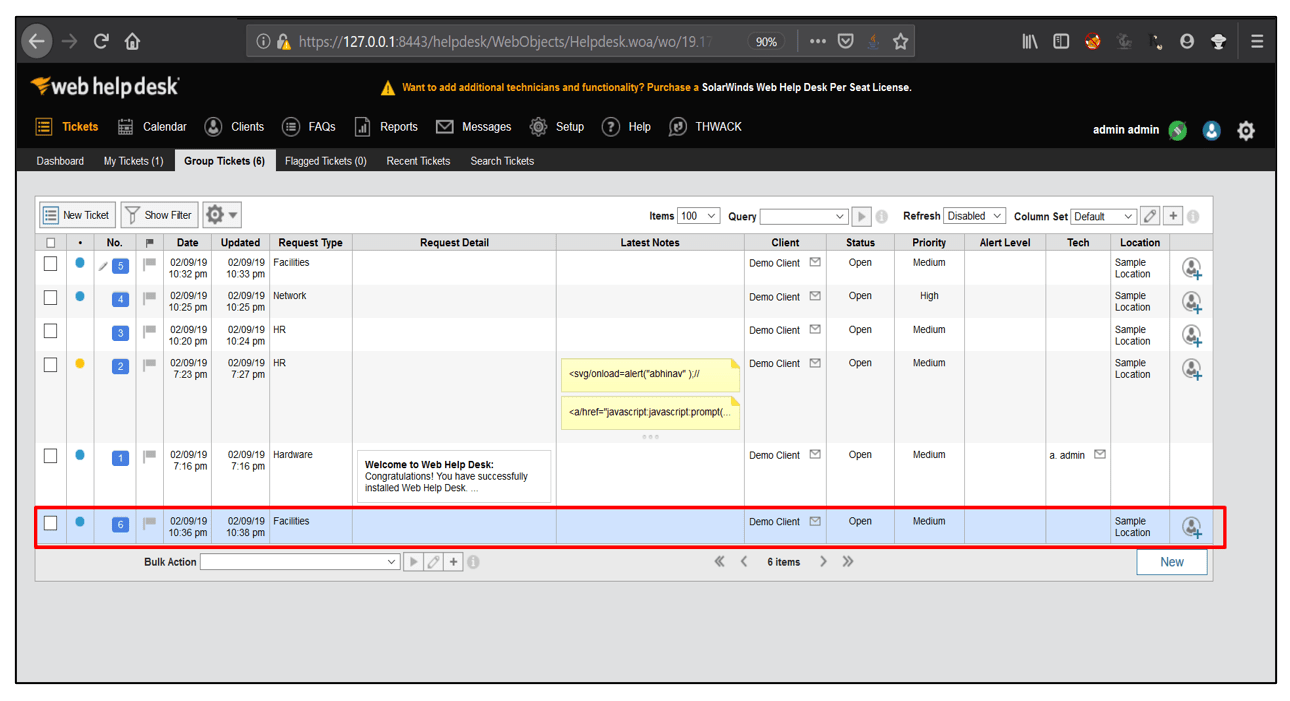

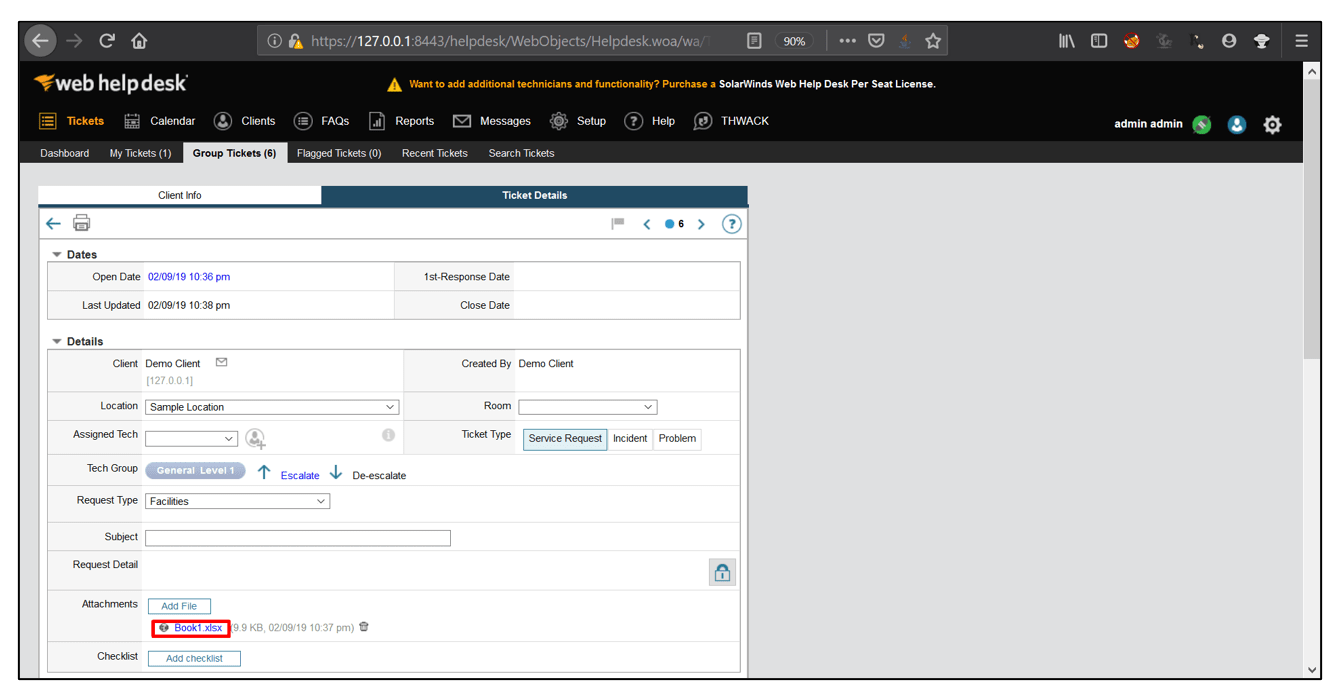

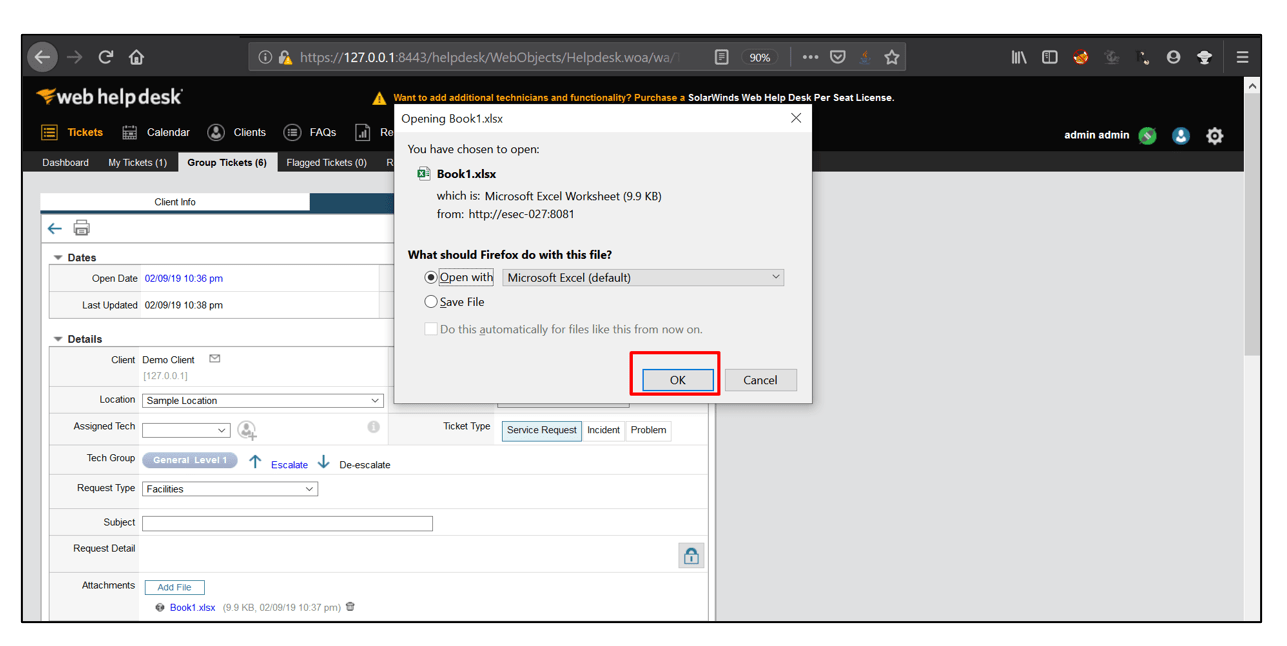
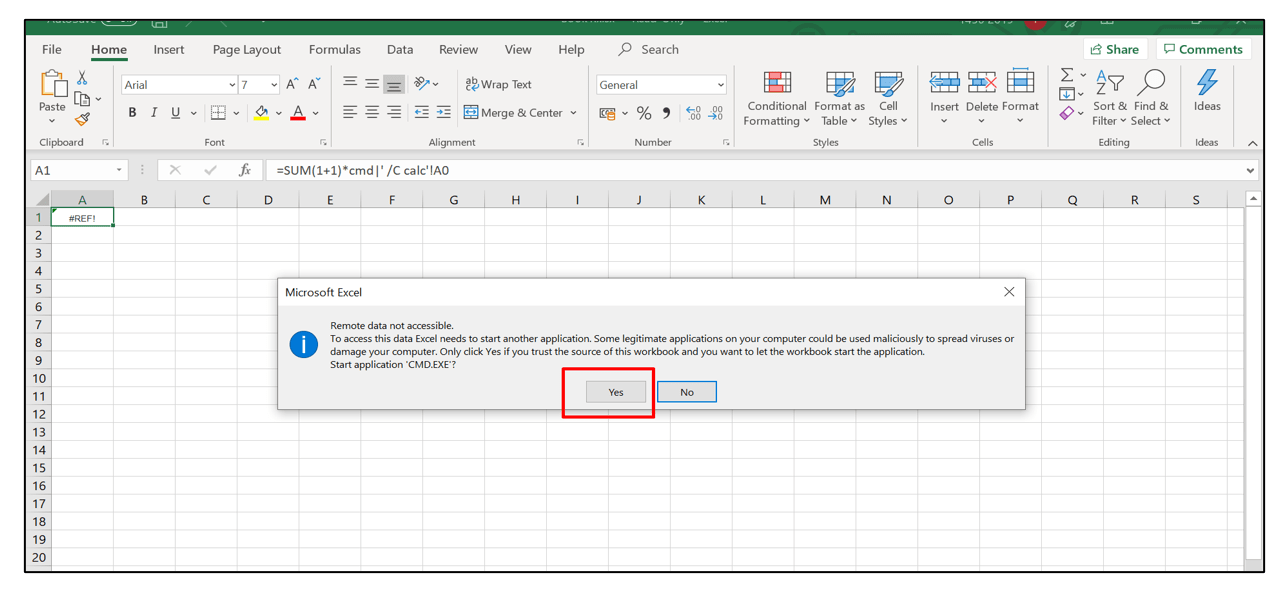
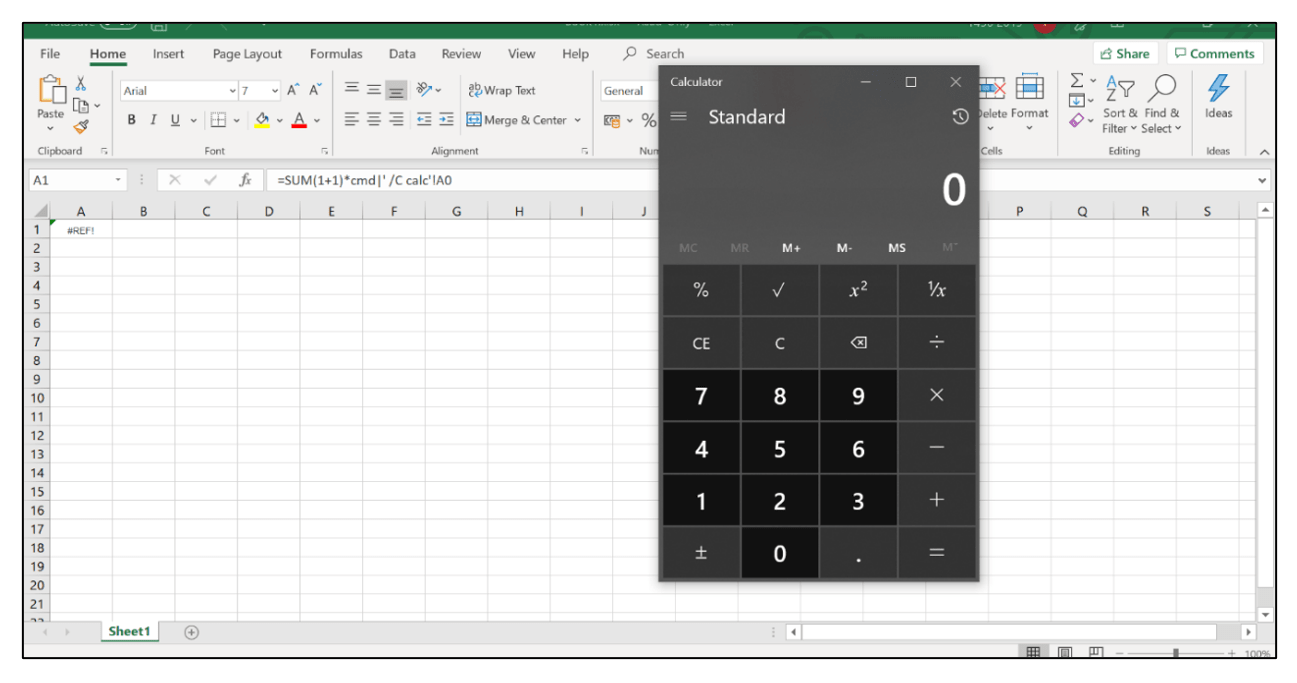
7. On opening the file, the calculator gets opened indicating that our formula injection payload worked.



Disclosure Process
- Reported the Vulnerability to the Vendor Security or PSIRT Team.
- Acknowledged confirmed from the Vendor that vulnerability exists.
- CVE has been filed in NVD.
- The vendor confirms that the vulnerability is fixed or the latest version, the patch is released.
- Vulnerability disclosed to the public.
Reference
https://www.solarwinds.com/web-help-desk
https://owasp.org/www-community/attacks/CSV_Injection
Has the vendor confirmed or acknowledged the vulnerability?
Yes
Discoverer
Abhinav Khanna from eSec Forte Technologies Pvt Ltd
