

Solarwinds NPM Orion platform 2018 – vulnerable for stored xss
Network Performance Monitor – Introduction
Network Performance Monitor is a powerful network monitoring software that enables you to quickly detect, diagnose, and resolve network performance problems and outages. NPM uses to identify network elements. During Discovery, NPM scans the network for nodes, and when a node and associated elements are found, you can add them to the SolarWinds database for monitoring.
eSecForte Technologies Security Researcher – Vaibhav Rai found a stored XSS vulnerability in the latest version for SolarWinds NPM (Orion Platform 2018, NPM 12.3, NetPath 1.1.3) and it has been assigned CVE-2019-12954 by the MITRE. SolarWinds Network Performance Monitor (Orion Platform 2018, NPM 12.3, NetPath 1.1.3) allows XSS by authenticated users.
Method of Exploitation
Steps to Reproduce:
Stored XSS
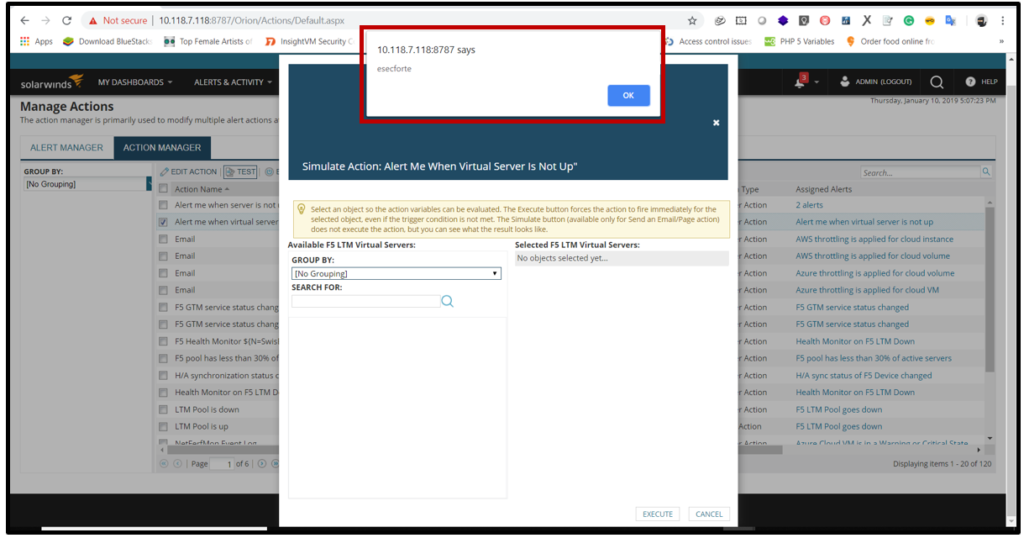
1. Open the solar wind console login with credential then click on ALERT&ACTIVITY and open
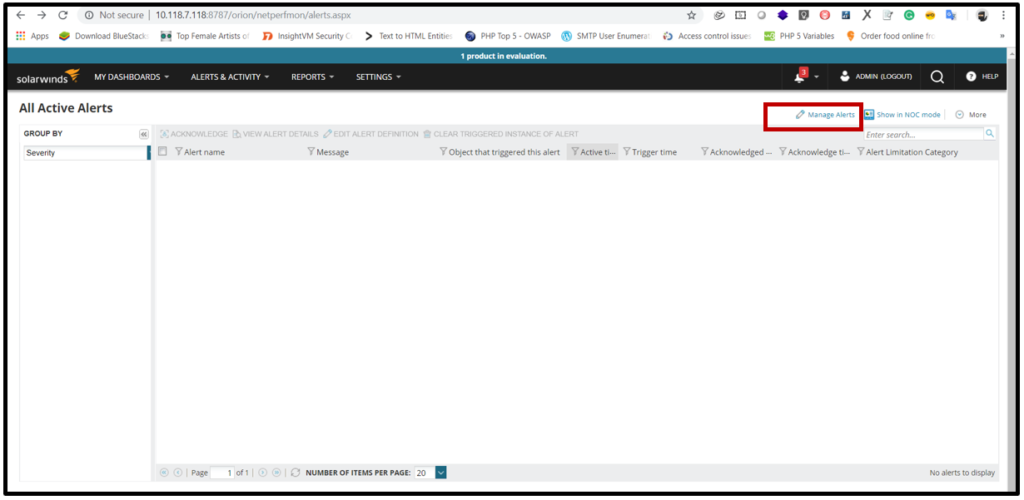

2. Now click on action manager.
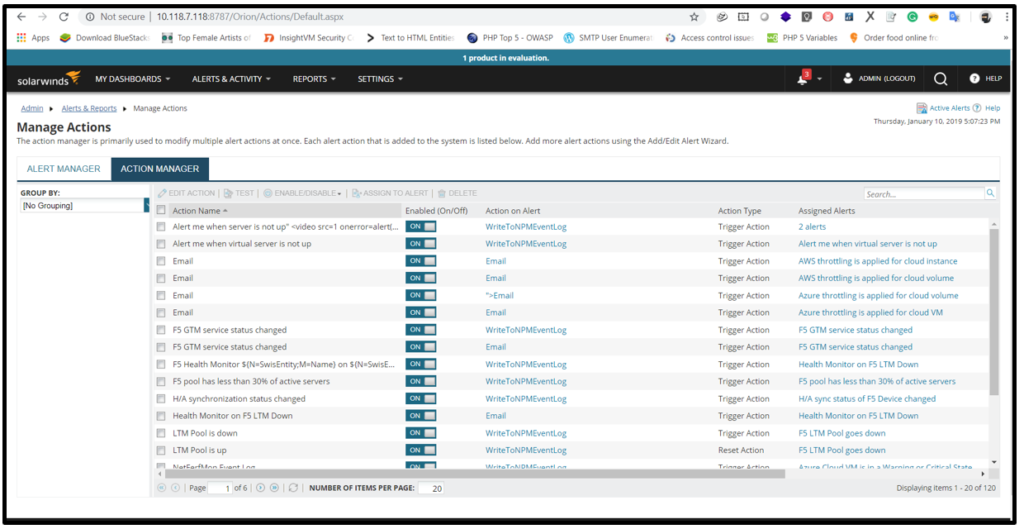

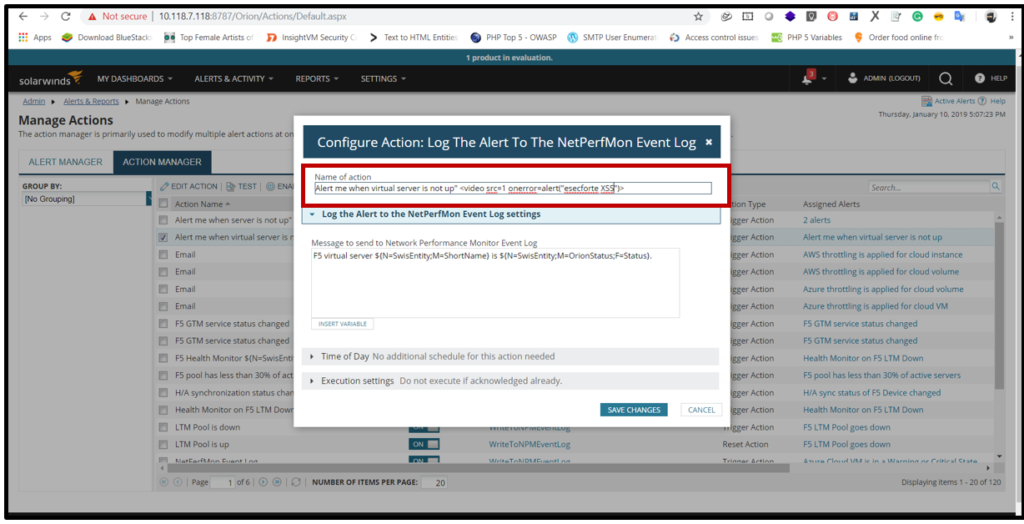
3. Select action name then click on edit action and put the script tag “<video src=1 onerror=alert(esecforte)>” in Name of action Click on save changes

4. Now select the action alert and Click on TEST.
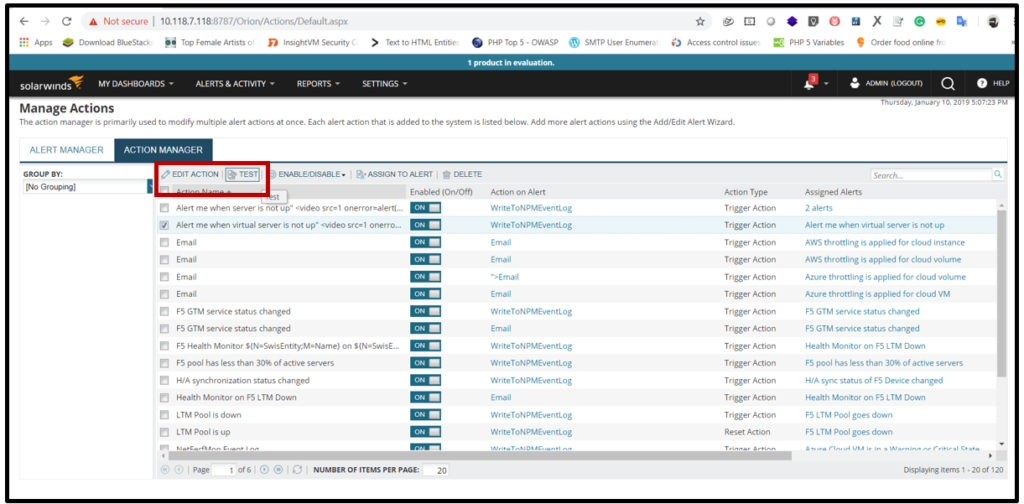

5. The script was executed successfully.

[Disclosure Process]
- Reported the Vulnerability to the Vendor Security or PSIRT Team
- Acknowledged confirmed from the Vendor that vulnerability exist
- CVE has been filed in NVD
- Vendor confirm that the vulnerability is fixed or a latest version, patch is released
- Vulnerability disclosed to the public
[Reference]
https://www.solarwinds.com/network-performance-monitor
https://owasp.org/www-community/attacks/xss/
https://en.wikipedia.org/wiki/Cross-site_scripting
[Has vendor confirmed or acknowledged the vulnerability?]
Yes
[Discoverer]
Vaibhav Rai from eSecForte Technologies Pvt Ltd https://www.esecforte.com/
