Race Condition
Title: Race condition
Description
Race conditions are most associated with computer science and programming. They occur when two computer program processes, or threads, attempt to access the same resource at the same time and cause problems in the system. Race conditions are considered a common issue for multithreaded applications. If an attacker used our hypothetical race condition above to perform malicious operations and help bypass secured mechanisms, it then becomes “Race Condition Vulnerability.” This vulnerability commonly occurs when threads use the same shared memory to update the values of variables
By this attack, the User can perform one action multiple times with the same request which is not the intended behavior
Attack Scenario:
1-Let suppose the program name is redacted.com.
2-Go to the profile section and Click on the collection.
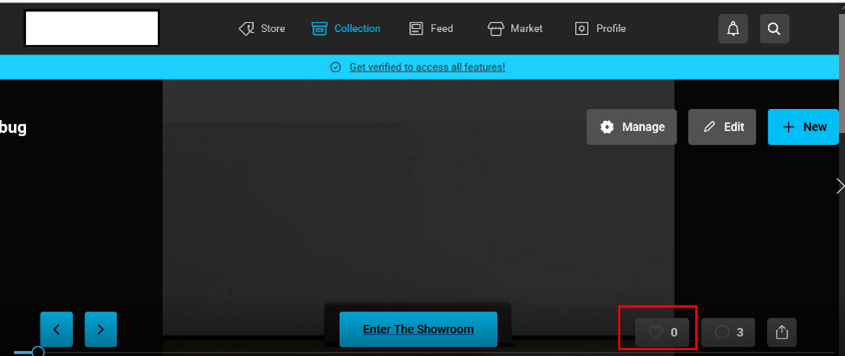

3-There is a Like option. Only a one-time user can use this function, but the user can use the function multiple times by performing this attack.
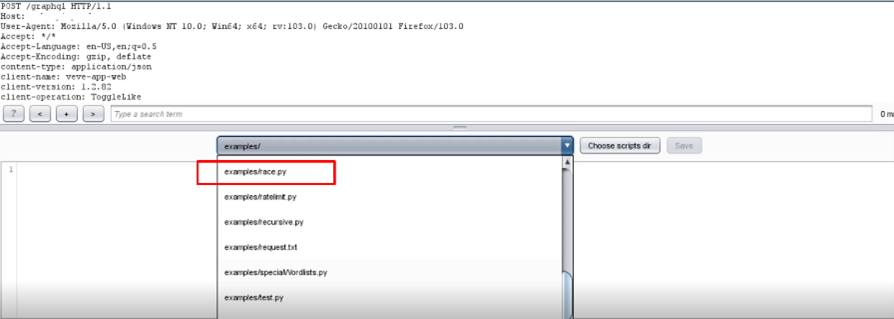
4-Add extension Turbo Intruder in your proxy tool.
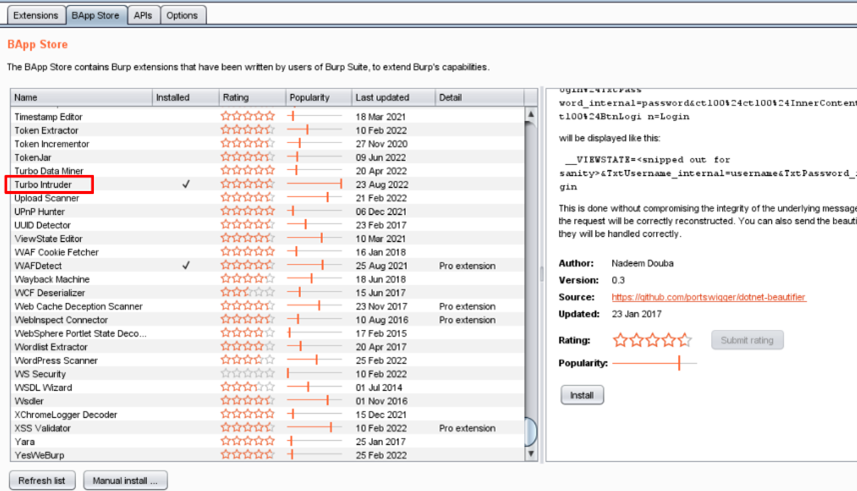

5-Click on the like option and intercept the request on the burp suite.


6-Send this request to the turbo intruder.
7-Write TesT %s after the header in the request
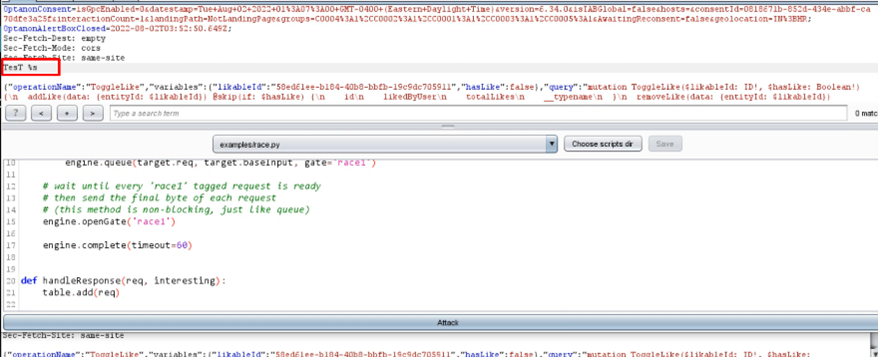

8-Select Race.py python payload and start the attack.

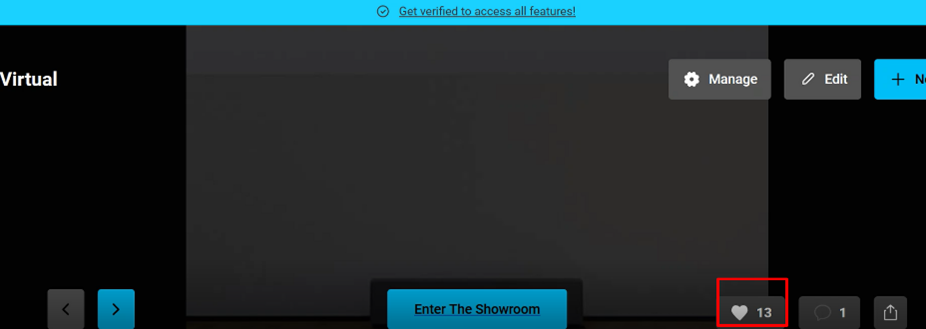
9-I was able to make more than one like.

Recommendation: The processing of multiple requests simultaneously and shared Database Management Systems (DBMS) are prime culprits for race condition occurrences.
So, what’s the fix?
We need to implement a pause and execute method. In other words, implementing resource locks for the shared memory and creating a condition that requires each request to be processed a single time. The remaining requests will be in a paused state as if they were in a queue.
[Discoverer]
Abhishek Pal from eSec Forte Technologies Pvt. Ltd
Reward