Response Manipulation Led to Authentication Bypass Vulnerability Description
Title: Response manipulation led to Authentication bypass Vulnerability Description
INTRODUCTION
Response manipulation is a technique where attackers make changes in the response before it reaches the browser. With the help of response manipulation, sometimes you can bypass 2FA or Authentication and many more things.
eSecForte Technologies Security Researcher – Abhishek Pal reported a 2FA bypass in P3 severity and an Authentication Bypass in P1 severity. Both vulnerabilities Got Accepted and rewarded. In different Severity.
Description: This attack is called Response manipulation. Here, the Attacker is able to know the victim’s email address and By reproducing the same step attacker is able to take over the victim’s account
Platform/Product: Example.com
Vulnerability Name:
Affected Component: Reset Password Functionality
Attack Type:
Impact:
The attacks use this attack to take over the full account of the Victim. The attacker can change the response on the server side and execute on the client side.
Recommendation:
- The entire login flow was revamped and the client-side JavaScript validation was removed the application was not accepting any user value to the response and manipulating the response gave us an error message.
Method of Exploitation
Steps to Reproduce #:-
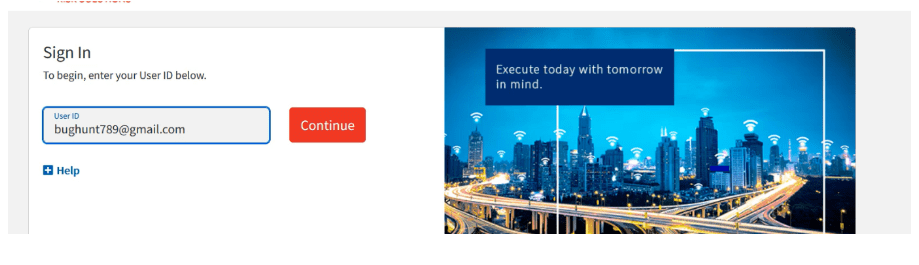
1- Navigate to the URL. Create accounts at [email protected].
2- Go to reset password functionality.

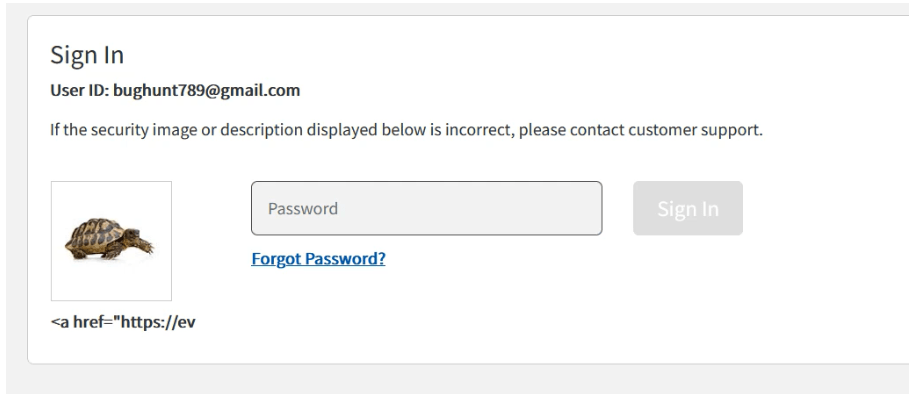
3- Open Gmail you received an OTP having 6 digits.

4- Enter the wrong OTP and Click on Verify OTP
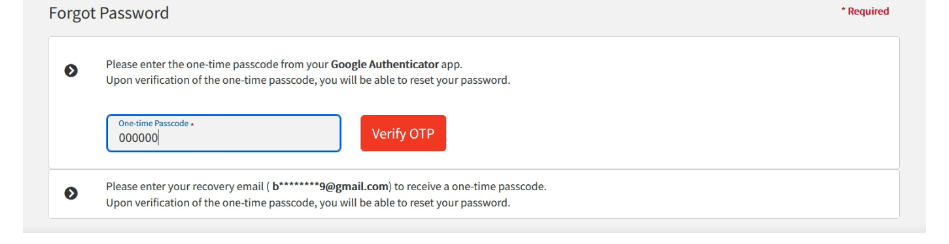

5- Capture the request on the burp-suite and intercept the request and send it to the response to the request.
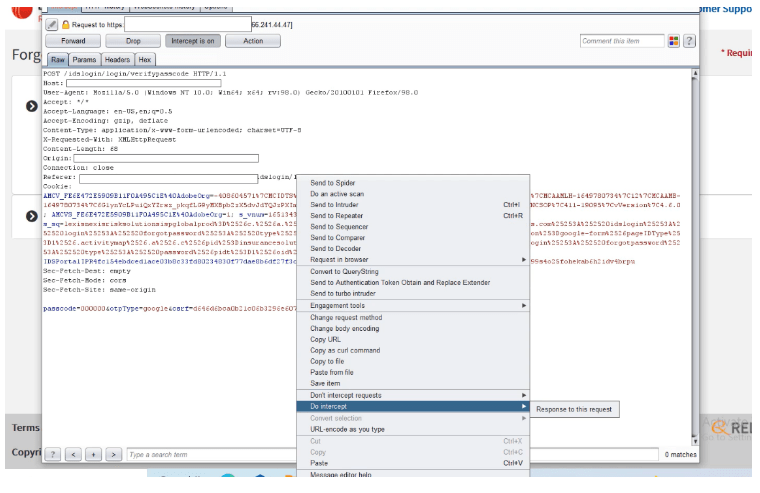

6- It shows 200 OK with the error=False.
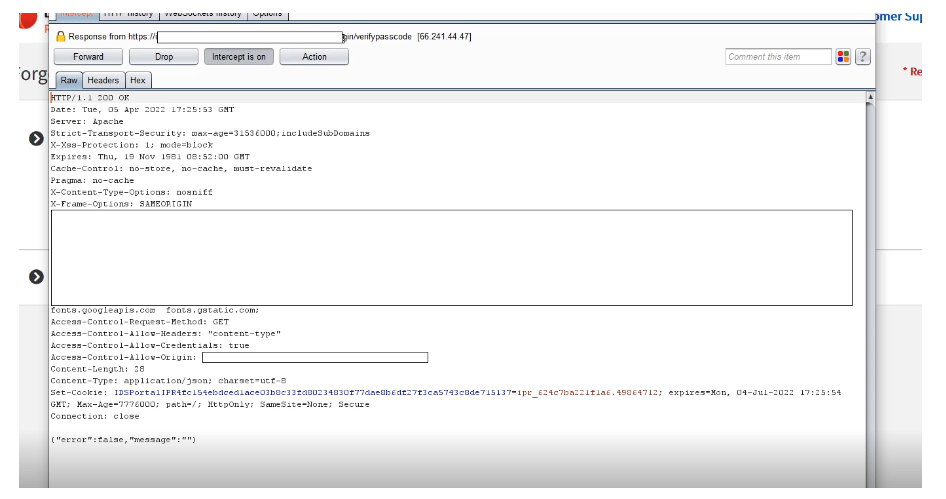

7- Change the success parameter value from false to true.
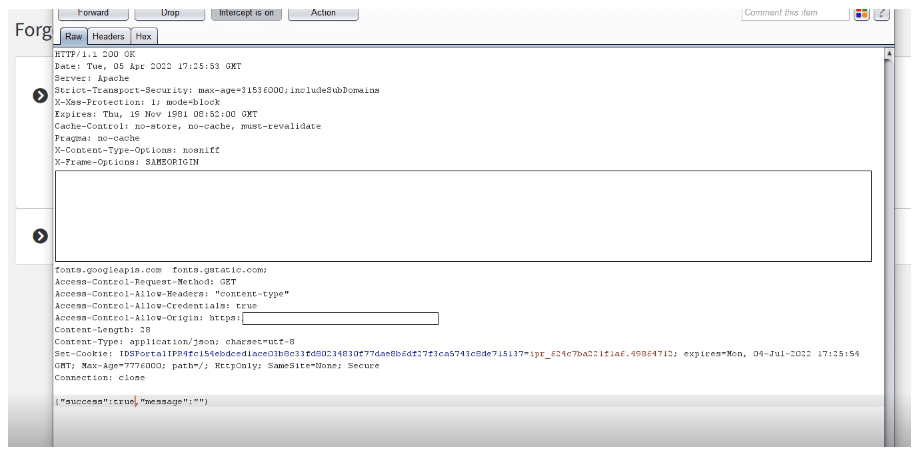

8- The server accepts the response and redirects to the Forget password page.
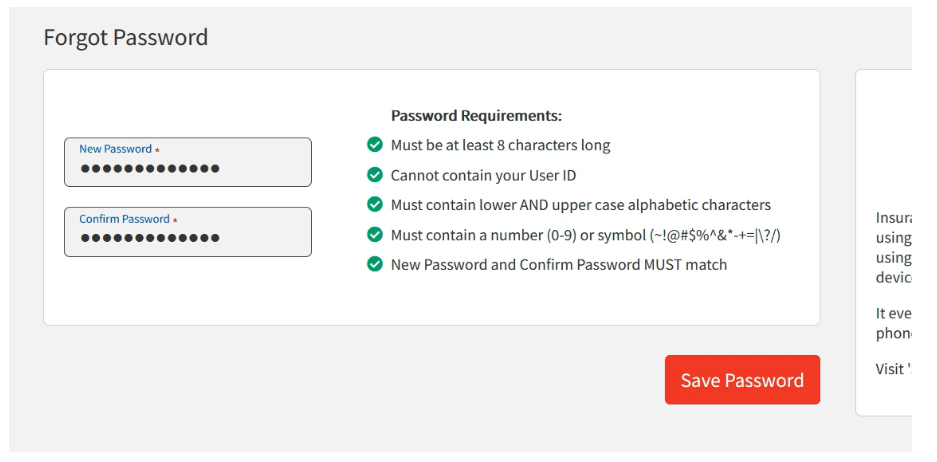

9- Set the new password and Click on the save password. The victim’s account password has been changed and logged in to the account

[Discoverer]
Abhishek Pal from eSec Forte Technologies Pvt. Ltd