

CVE-2023-40813-HTML injection-Saved Search
-
- Vendor of the product(s) –
- Product Name – OpenCRX
- Version – exact ver of the product which is vulnerable – 5.2.0
- Affected component(s) – Saved Search Creation
- Attack vector(s) – Web Application
- Suggested description of the vulnerability for use in the CVE- HTML injection on the Saved Search Creation
- Discoverer(s)/Credits – your name -Nandini Sharma
- Step by Step POC written in sequential order – prepare a word file for all this.
Title: HTML injection at Saved Search Creation
INTRODUCTION
HTML Injection is a type of web application security vulnerability where an attacker is able to inject malicious HTML code into a web page viewed by other users. The attack can be launched by an attacker who enters specially crafted HTML code, such as script tags or iframe elements, into the input field. The web application may then display this malicious HTML code to other users, potentially executing the code in their web browser and allowing the attacker to carry out their malicious actions.
eSecForte Technologies Security Researcher – Nandini Sharma reported a HTML Injection
Description: HTML Injection in which attacker simple insert payload at Saved Search Creation filed and it executed when attacker save the Saved Search Creation
Platform/Product: OpenCRX
Vulnerability Name: Html Injection
Affected Component: Activity Saved Search Creation
Attack Type:
Impact:
HTML injection can result in the modification of web page content or the execution of malicious scripts, leading to the theft of sensitive information, malware distribution, phishing attacks, defacement of websites, or denial of service. It can have a significant impact on the reputation and security of a website and the organization that runs it.
Recommendation:
Preventing HTML injection requires proper input validation and sanitization of user input.
Method of Exploitation
Step to reproduce: –
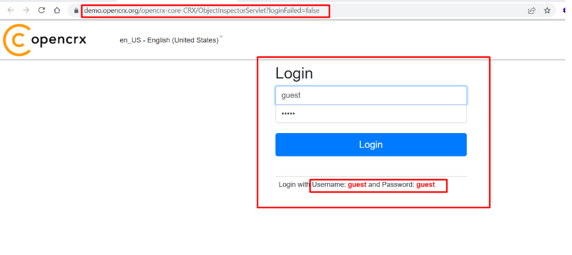
Step-1 Navigate to https://demo.opencrx.org/opencrx-core-CRX/ObjectInspectorServlet?requestId=3D06QMASG8CMLDTV63YISTS8F&event=24?loginFailed=false and login as Guest credentials

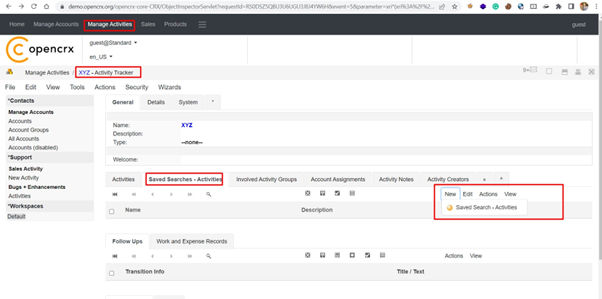
Step-2 Now, create new Saved Search-Activity in the Activity Tracker as shown below: –

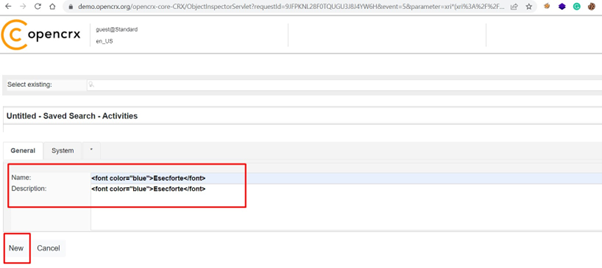
Step-3 Now, Insert Html payload in the Name and description field as shown below: –
Paylaod – <font color=”blue”>Esecforte</font>

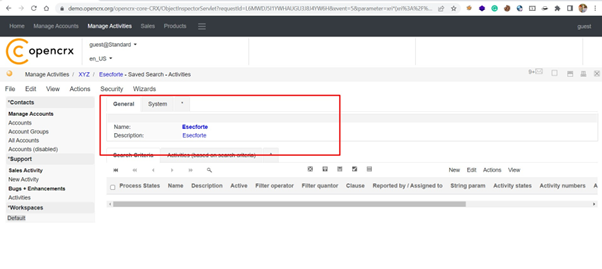
Step-4 Now, click on the save button to save this activity. It has been observed by the auditor that HTML payload executed.

[Discoverer]
Nandini Sharma from eSec Forte Technologies Pvt. Ltd
