

Unverified Password Changed
Required Details
Vendor of the product(s): Rubicon Communications, LLC (Netgate).
Product Name:Netgate
Vendor Mail –ID: [email protected]
Version – exact ver of the product which is vulnerable: Pfsense firewall version 2.6.0 CE
Affected component(s) :Password change functionalities
Attack vector(s):NA
Suggested description of the vulnerability for use in the CVE :Unverified Password change in Pfsense CE
Discoverer(s)/Credits – :Dipendar Sharma
Overview:-
All Pfsense CE, are vulnerable to unverified password change, due to lack of MFA. This allows to attacker change the password of user without MFA
Details :-
Vulnerability covered under CWE-620 — Unverified Password Change.
When setting a new password for a user, the product does not require knowledge of the original password, or using another form of authentication. This could be used by an attacker to change passwords for another user, thus gaining the privileges associated with that user.
Poc Details:-
Login to the application as admin:pfsense via visiting http://10.118.20.200/system_usermanager.php?act=edit&userid=2
Click on system>user manager>users and attacker can change any user password without MFA or old password.
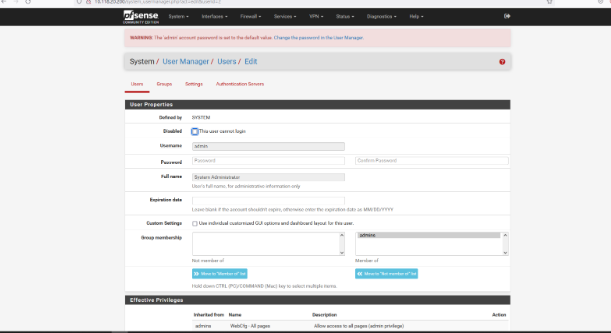

Affected Environments
Pfsense CE all version
Prevention
It’s vitally important to consider every action in an application not only from the user experience perspective, but the attacker’s as well. Critical access points in applications should always be protected by at least a second factor of authentication. In this case, the application should require the current password at a minimum. Ideally the application could require MFA authentication to the application, as well as an MFA token to modify those critical points.
