

CVE-2023-27152-OPNSense-Brute force
September 25, 2023
– Vendor of the product(s): Deciso B.V.
– Product name: OPNsense
– Vendor Mail-ID: [email protected]
– Version: OPNsense23.1
– Affected component: OPNsense login page
– Attack vector: Custom list of username and passwords
– Suggested description of the vulnerability for use in the CVE: OPNsense firewall login page do not impose rate limits which makes it easier to attempt brute-force attacks against the login page and attacker can brute force the login credentials.
– Discoverer(s) / Credits: Pragati Bhardwaj
– Overview:
PoC Details:
Step-1 Login to the application
Visiting via this URL: http://10.118.20.160/ (https://github.com/osTicket/osTicket/releases )

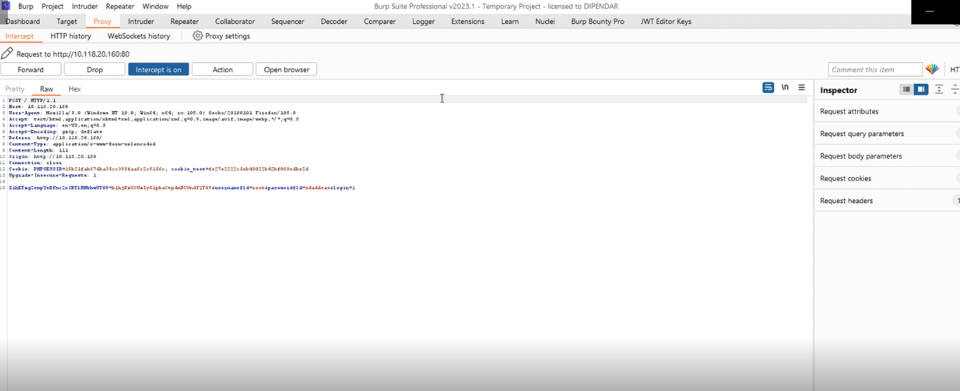
Step-2 In this step, we capture the request in Burp suite of login credentials.

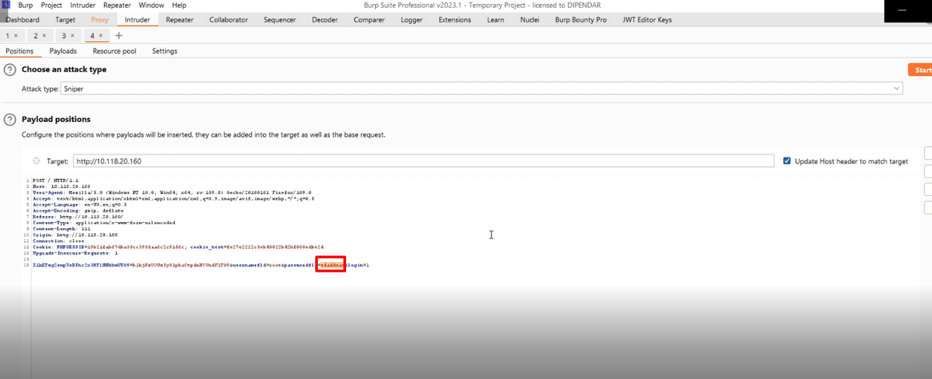
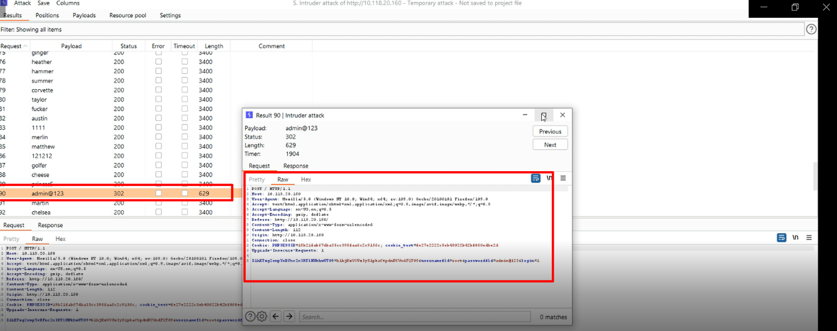
Step-3 After that, the request is sent into intruder and Brute force the Password parameter.

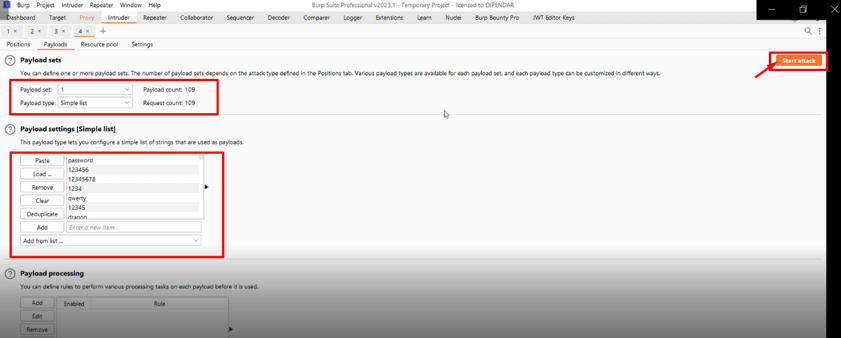
Step-4 Now, we set Payload of 100+ and start the attack.

Step-5 We Successfully found the Correct password – admin@123

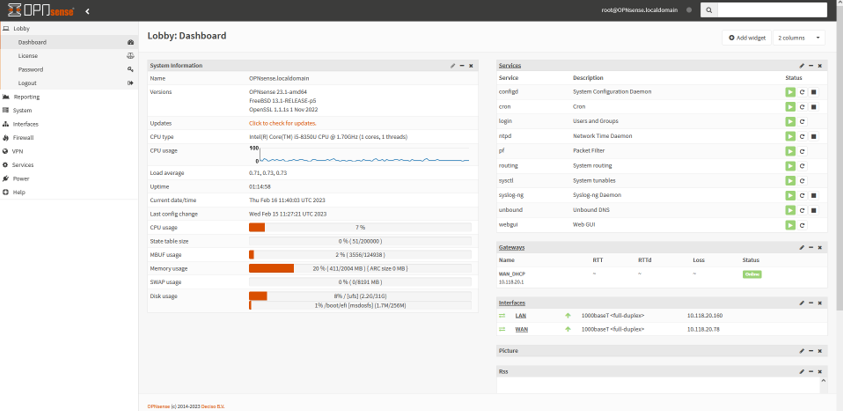
Step-6 We had successfully login.

Prevention:
- Account lockout after failed attempts.
- Limit logins to a specified IP address or Range.
- Use CAPTCHA.
- Whitelisting procedure.
- Strong Password Mechanism.
