

CVE-2023-27148-osTicket_XSS
Vendor of the product(s) – Enhancesoft
Product Name – osTicket (https://github.com/osTicket/osTicket/releases )
Version – v1.17.2 (Latest)
Affected component(s) – Role “Name” Field
Attack vector(s) – Local
Suggested description of the vulnerability for use in the CVE- Stored Cross Site Scripting (XSS) in Admin Panel: osTicket Admin Panel provides the facility to add Roles. It has been observed that the input taken by user is not properly sanitized. This allows the attacker to inject the malicious JavaScript code in the “Name” input field. The malicious code can then be executed whenever the vulnerable web page is accessed by any user and will remain persistent.
Discoverer(s)/Credits – your name -Vaibhav Kumar Srivastava
Title: Stored Cross Site Scripting (XSS) in Admin Panel
INTRODUCTION
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it. In a Stored XSS attack, the vulnerable application receives user-supplied input from untrusted sources and stores it. This malicious content also gets included in the later HTTP responses sent by the server.
eSecForte Technologies Security Researcher – Vaibhav Kumar Srivastava reported a Stored Cross Site Scripting (XSS)
Description: osTicket Admin Panel provides the facility to add Roles. It has been observed that the input taken by user is not properly sanitized. This allows the attacker to inject the malicious JavaScript code in the “Name” input field. The malicious code can then be executed whenever the vulnerable web page is accessed by any user and will remain persistent.
Platform/Product: osTicket (v1.17.2 – Latest)
Vulnerability Name: Stored Cross Site Scripting (XSS)
Affected Component: Role “Name” Field
Attack Type: Persistent/Stored
Impact:
Stored XSS attacks can have serious consequences, such as stealing sensitive data, modifying the content of the web page, or redirecting users to a malicious site.
Recommendation:
Implement proper input validation and output encoding to prevent malicious code from being injected into the web application. Use server-side validation to ensure that user input is properly sanitized before being stored in a database or displayed on a web page. Use output encoding to ensure that any user input that is displayed on the web page is properly encoded to prevent malicious code from being executed.
Method of Exploitation
Step to reproduce: –
Step-1 Navigate to the GitHub release of the osTicket and download the latest release (v1.17.2) of osTicket (https://github.com/osTicket/osTicket/releases ). Install and Setup the osTicket on local system using XAMPP.
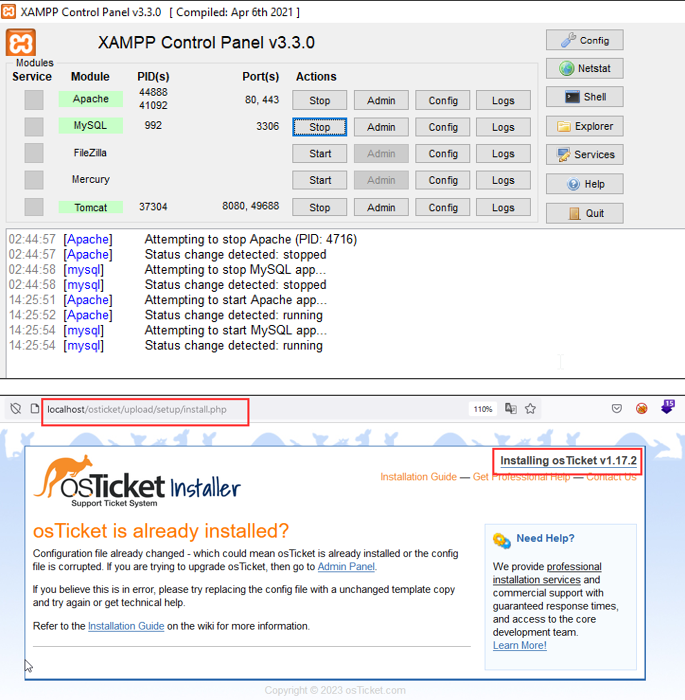

Step-2 Visit the Admin panel and login into the application with the valid credentials.


Step-3 Visit the Admin panel and login into the application with the valid credentials.
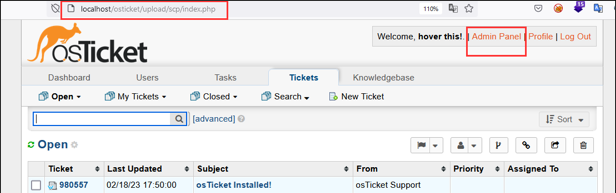

Step-4 In the Admin Panel, navigate to the “Roles” tab.
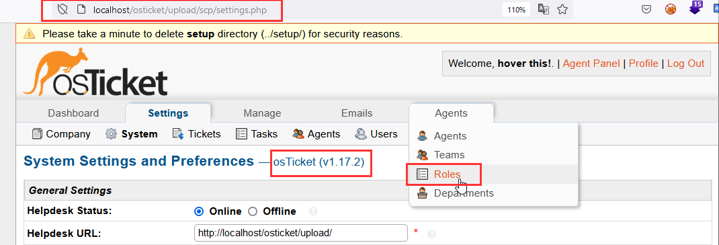

Step-5 Click on “Add New Role” and add the payload (<x onmouseover=alert(document.cookie)>hover this!) in the “Name” field. Make sure you also assign some permission to the new role before saving it.
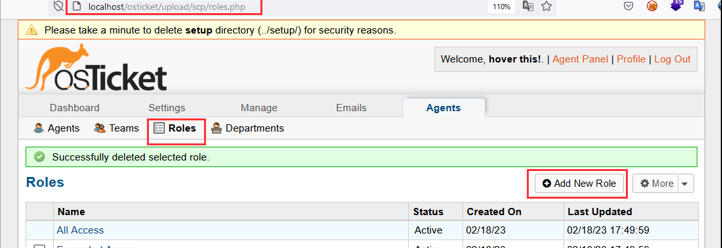

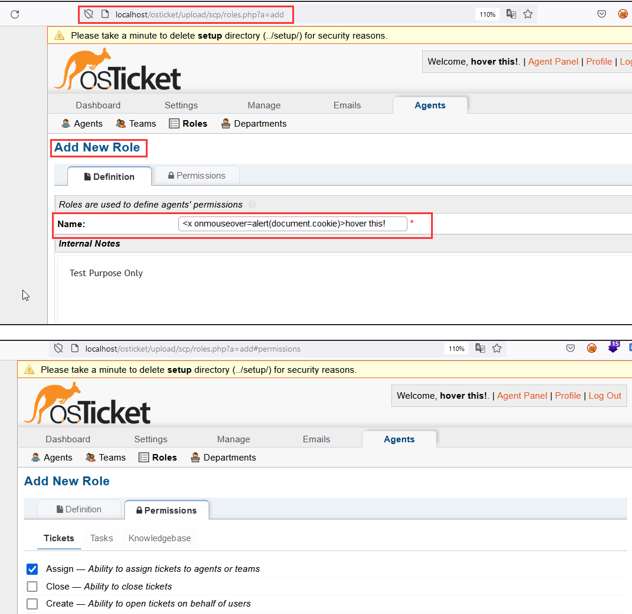

Step-6 Click on “Add Role” to save the details.
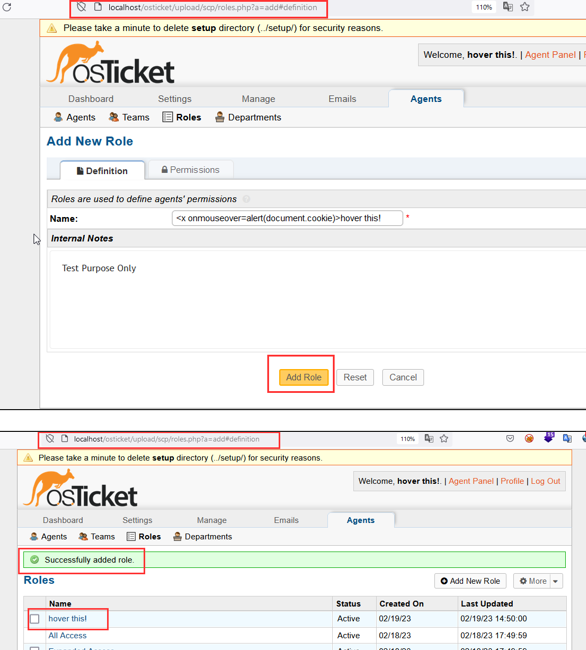

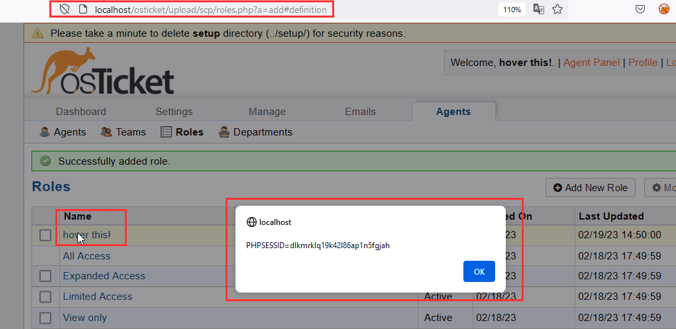
Step-7 Hover on the newly added role and it has been observed that the injected payload is executed successfully. It should be noted that the payload will remain persistent/stored in the application and will trigger once the user interact with the page.

[Discoverer]
Vaibhav Kumar Srivastava from eSec Forte Technologies Pvt. Ltd
