

HTML Injection vulnerability in ManageEngine Remote Access Plus
INTRODUCTION
eSecForte Technologies Security Researcher – Tarun Sehgal found HTML Injection vulnerability in the ManageEngine Remote Access Plus and it has been assigned CVE-2019-16268 by the MITRE.
ManageEngine Remote Access Plus is an Enterprise Remote access software that helps system administrators and IT help desk technicians in troubleshooting remote computers from a central location.
Description: HTML Injection vulnerability
HTML injection is a type of injection vulnerability that occurs when a user is able to control an input point and is able to inject arbitrary HTML code into a vulnerable web page.
Impact:
A possible attack scenario is demonstrated below:
- Attacker discovers injection vulnerability and decides to use an HTML injection attack
- Attacker crafts malicious link, including his injected HTML content, and sends it to a user via email
- The user visits the page due to the page being located within a trusted domain
- The attacker’s injected HTML is rendered and presented to the user asking for a username and password
- The user enters a username and password, which are both sent to the attackers server
Recommendation:
- Your script should filter metacharacters from user input.
Steps to Reproduce:
1. Login using valid credentials and go to Roles.
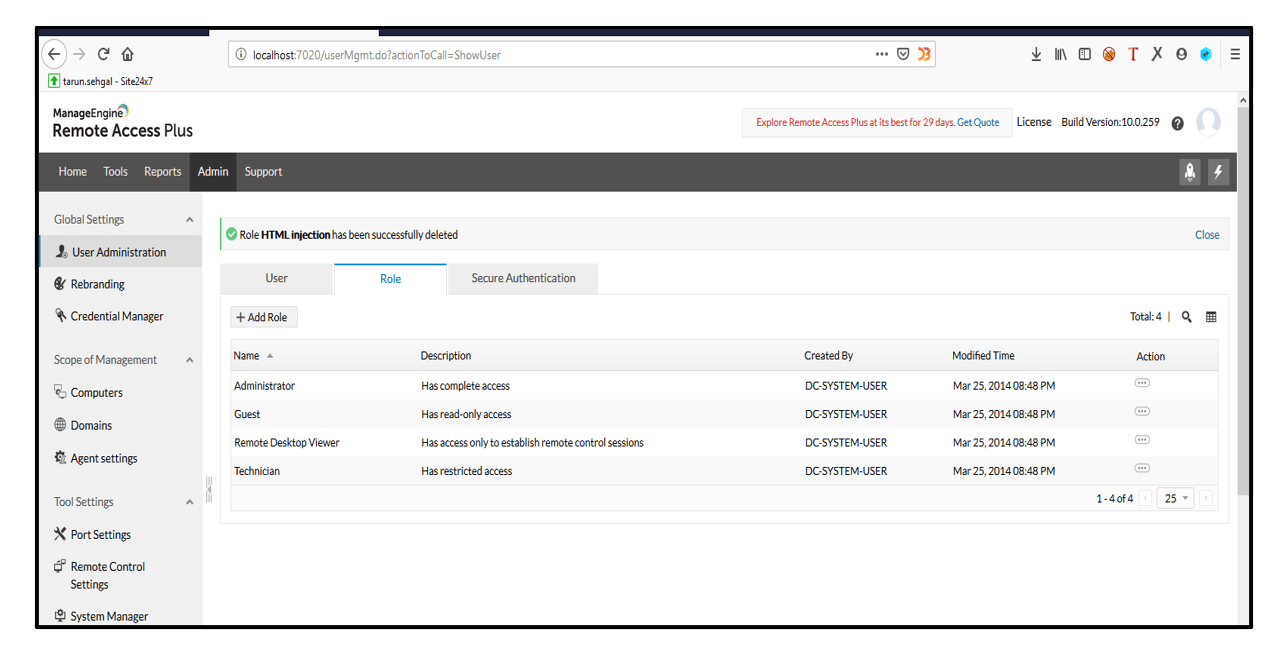

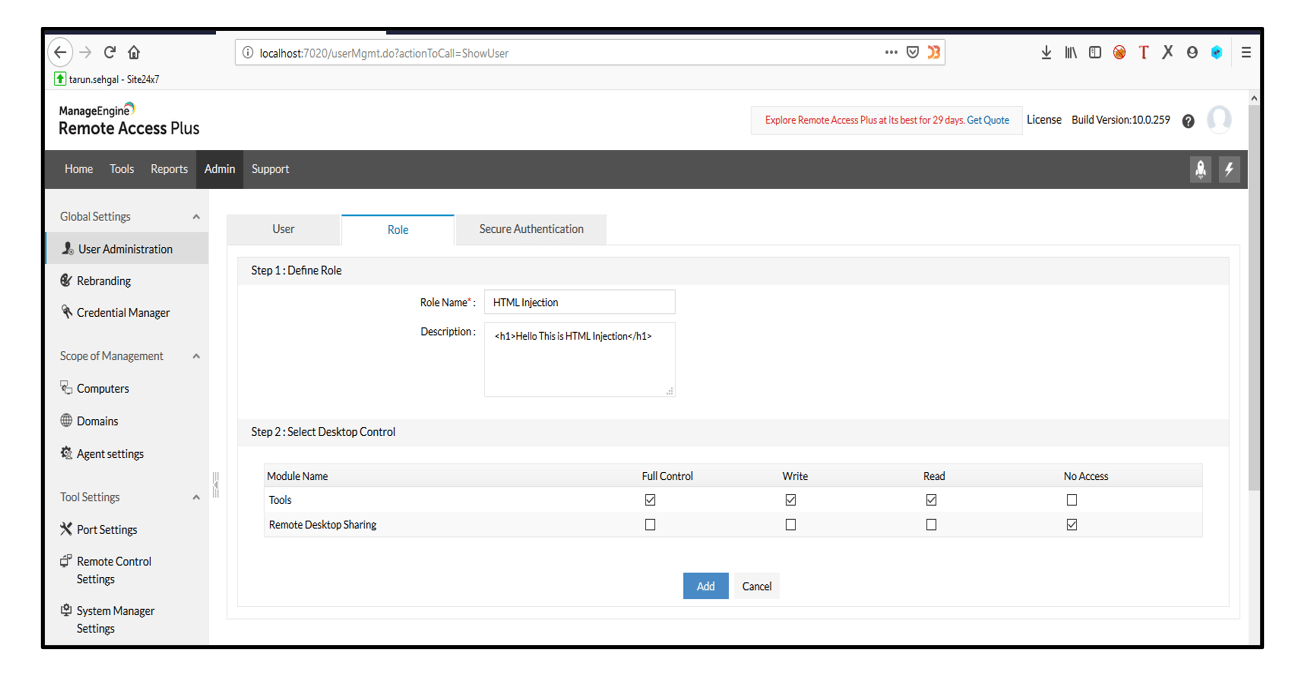
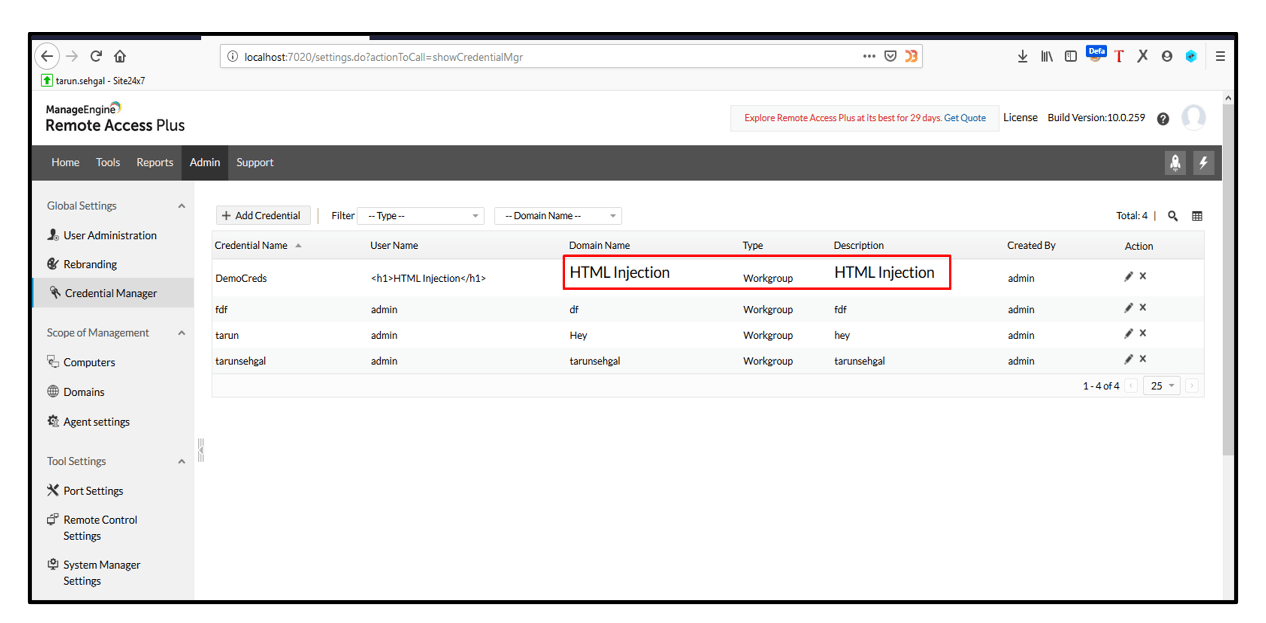
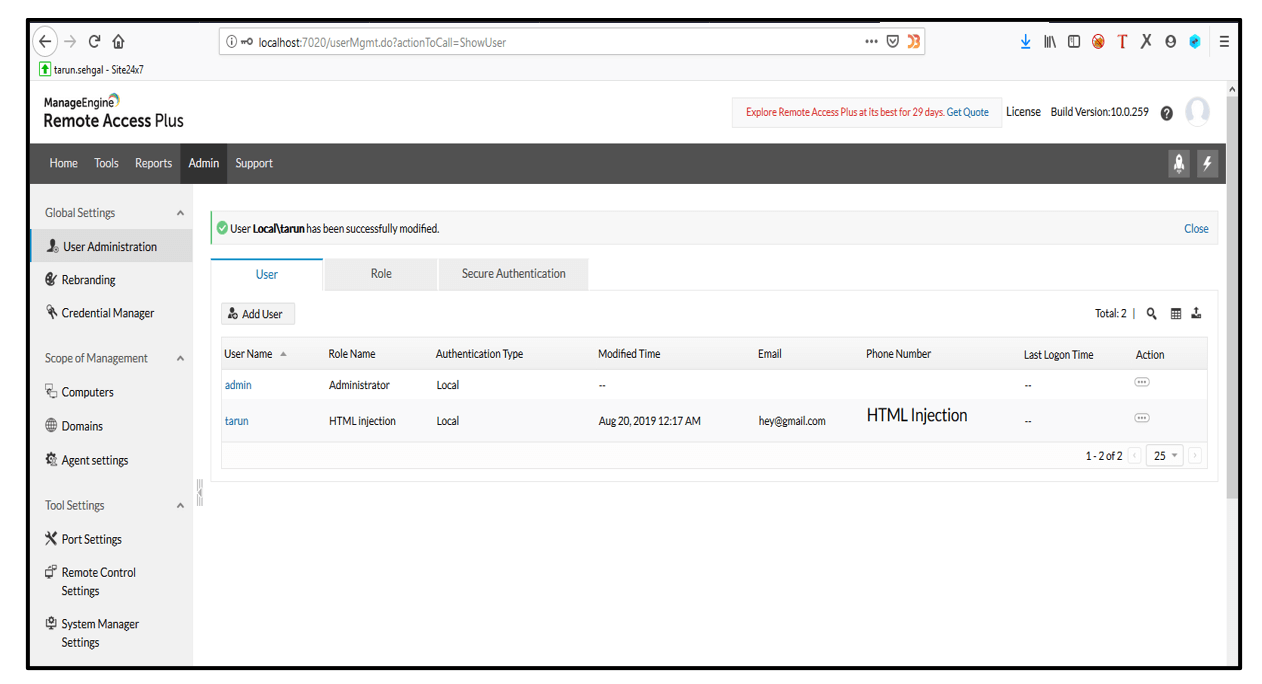
2. Click on +Add Role button and put the HTML injection payload in Description parameter and click on Add button. The HTML Injection payload gets executed.

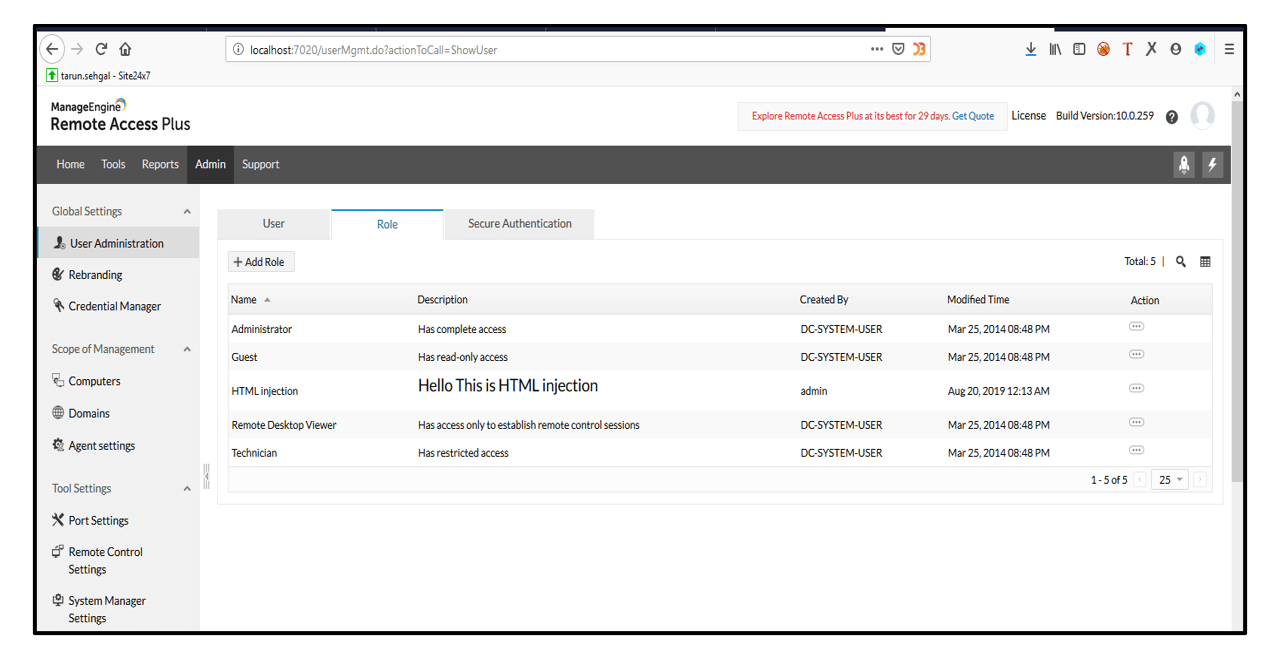

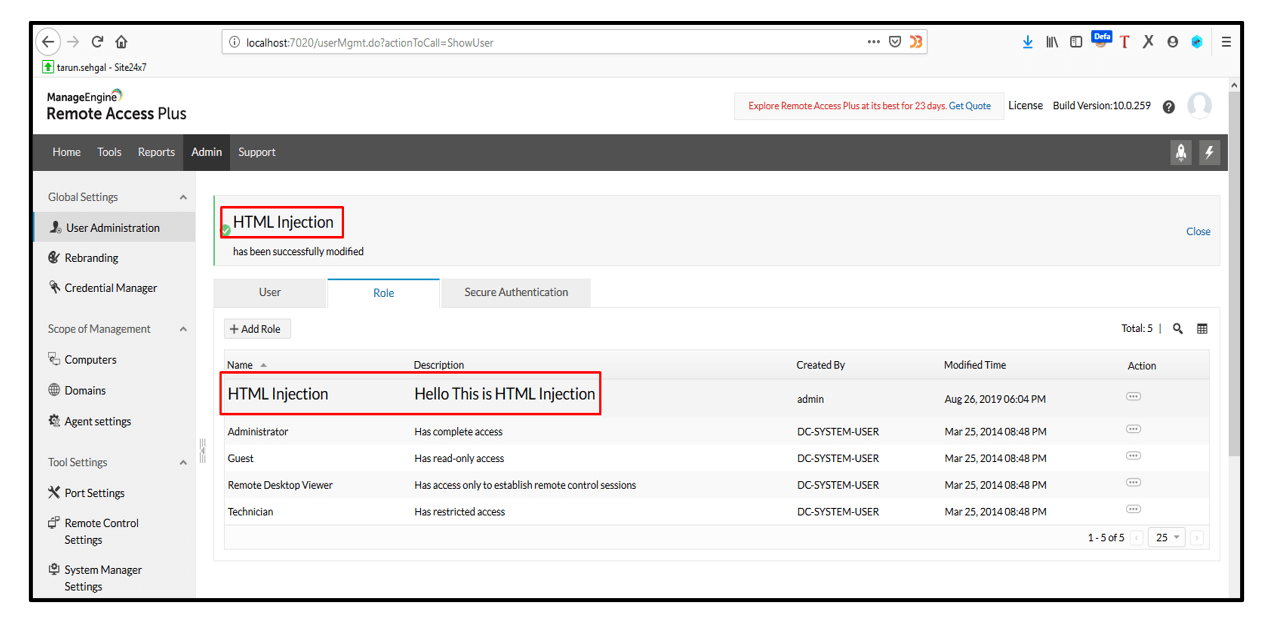
3. Likewise, other parameters in the application were found to be vulnerable to HTML Injection as well.



[Disclosure Process]
- Reported the Vulnerability to the Vendor Security or PSIRT Team.
- Acknowledged confirmed from the Vendor that vulnerability exists
- CVE has been filed in NVD
- The vendor confirms that the vulnerability is fixed or the latest version, the patch is released
- Vulnerability disclosed to the public.
[Reference]
https://www.manageengine.com/remote-desktop-management/knowledge-base/html-injection.html
https://www.acunetix.com/vulnerabilities/web/html-injection/
[Has the vendor confirmed or acknowledged the vulnerability?]
Yes
[Discoverer]
Tarun Sehgal from eSec Forte Technologies Pvt Ltd
