

ManageEngine DesktopCentral v 10 – Vulnerable to HTML Injection
INTRODUCTION
ManageEngine DesktopCentral is a Unified Endpoint Management (UEM) solution that helps manage servers, desktops, virtual machines, mobile phones, tablets, Its features includes Patch Management, Software Deployment, Remote Desktop Sharing, IT Asset Management, Desktop Configurations, Service Pack Installation, Active Directory Reports, User Administration, Mobile Device Management and many more.
eSecForte Technologies Security Researcher – Tarun Sehgal found a HTML Injection vulnerability in the ManageEngine DesktopCentral v 10 and it has been assigned CVE-2019-15510 by the MITRE.
Description:-
HTML injection is a type of injection issue that occurs when a user is able to control an input point and is able to inject arbitrary HTML code into a vulnerable web page. This vulnerability can have many consequences, like disclosure of a user’s session cookies that could be used to impersonate the victim, or, more generally, it can allow the attacker to modify the page content seen by the victims.
This vulnerability occurs when the user input is not correctly sanitized and the output is not encoded. An injection allows the attacker to send a malicious HTML page to a victim. The targeted browser will not be able to distinguish (trust) the legit from the malicious parts and consequently will parse and execute all as legit in the victim context.
Impact:-
A possible attack scenario is demonstrated below:
- Attacker discovers injection vulnerability and decides to use an HTML injection attack
- Attacker crafts malicious link, including his injected HTML content, and sends it to a user via email
- The user visits the page due to the page being located within a trusted domain
- The attacker’s injected HTML is rendered and presented to the user asking for a username and password
- The user enters a username and password, which are both sent to the attackers server
Recommendation:-
This type of Injection the whole design of your website may be destroyed or even the user’s login data may be stolen. Your script should filter meta characters from user input.
This type of injection attack occurs when the input and output are not properly validated. Therefore, the main rule to prevent HTML attack is appropriate data validation. Your script should filter meta characters from user input. It should be remembered that good security testing is also a part of prevention. I would like to pay attention, that as HTML Injection attack is very rare, there is less literature to learn about it and less scanner to select for automatic testing.
Method of Exploitation
Steps to Reproduce:-
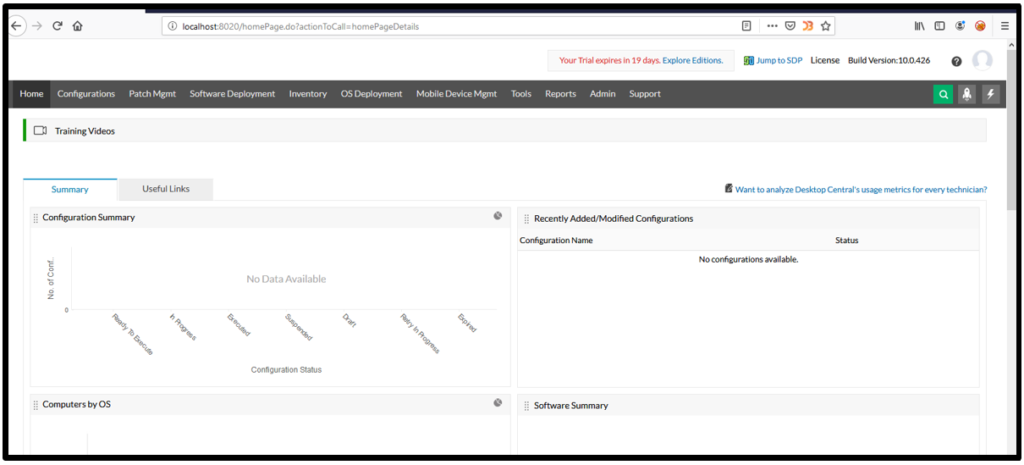
1. Open the application after login with admin credentials in Desktop Central application :

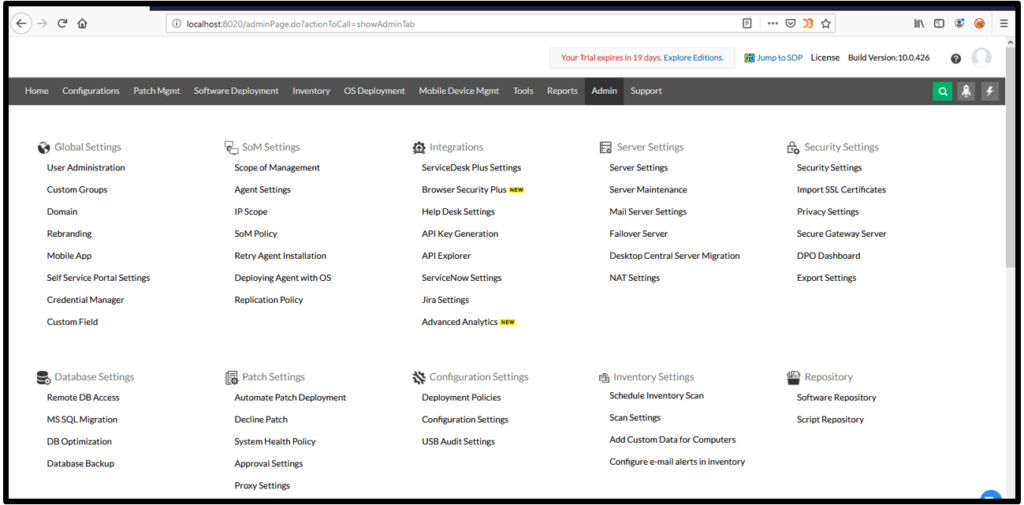
2. Click on admin – User administration button as shown below :

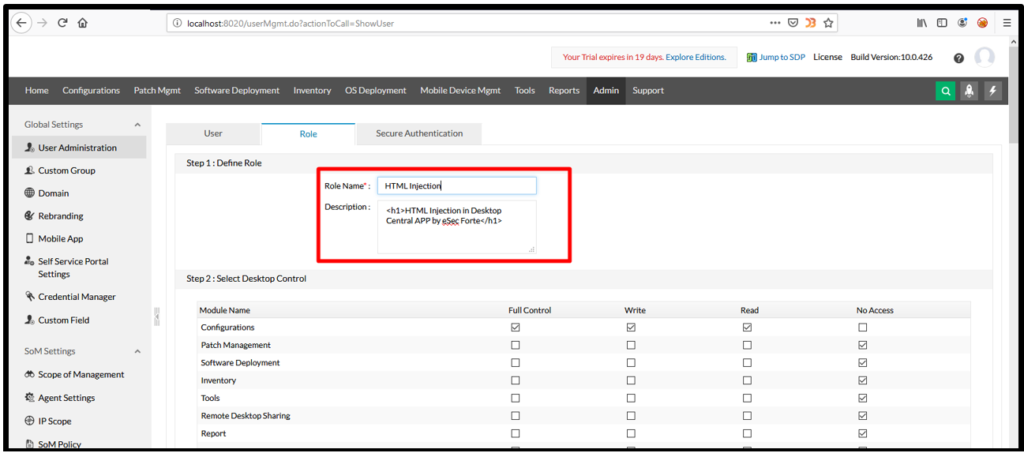
3. In user administration page click on role button and put HTML tag in description box:

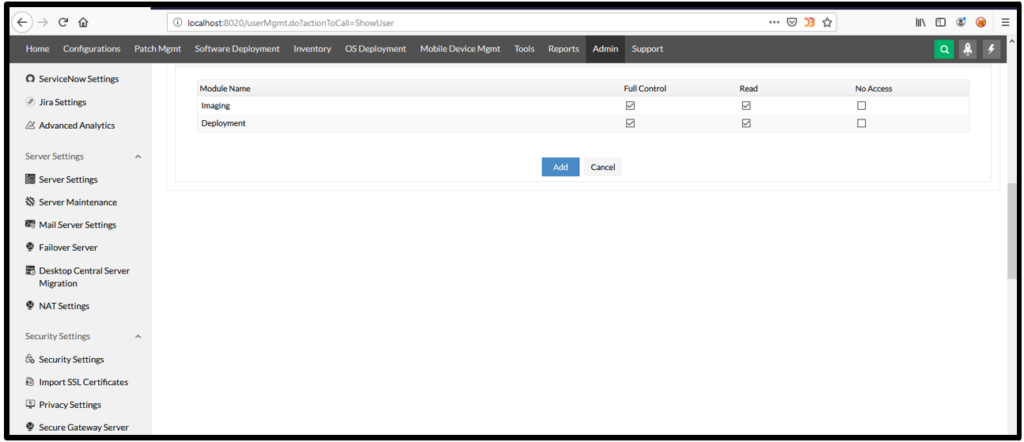
4. Now click on add button:

5. After clicking on add button, HTML tag executed as shown below:
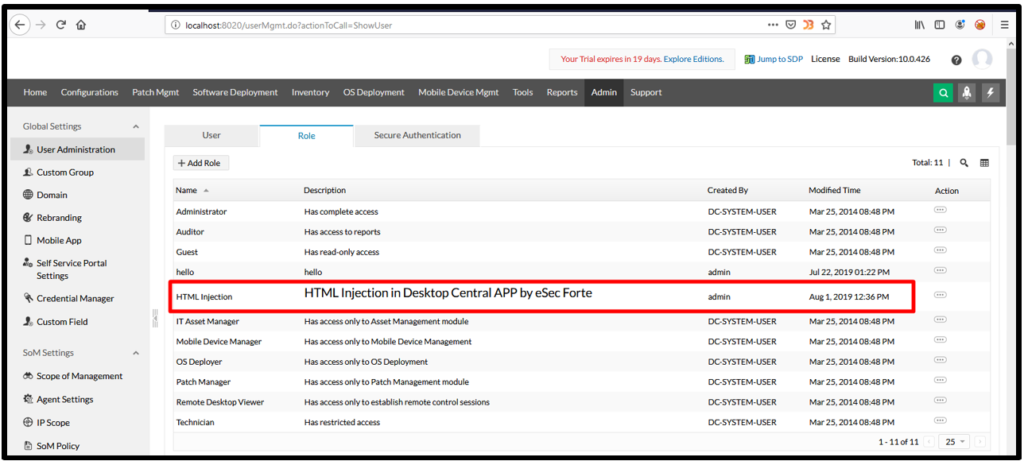

6. Similarly, I have put video tag in the description box and it was executed:
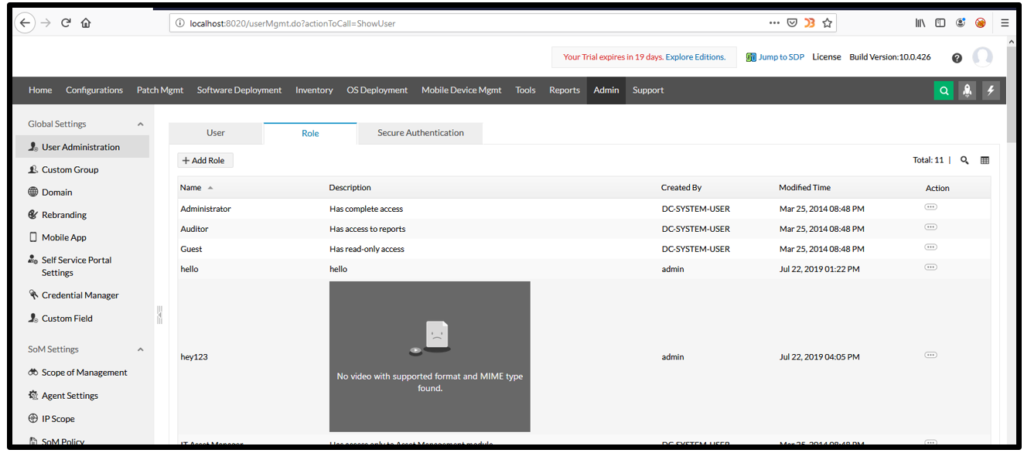

[Disclosure Process]
- Reported the Vulnerability to the Vendor Security or PSIRT Team
- Acknowledged confirmed from the Vendor that vulnerability exist
- CVE has been filed in NVD
- Vendor confirm that the vulnerability is fixed or a latest version, patch is released
- Vulnerability disclosed to the public
[Reference]
https://www.manageengine.com/products/desktop-central/html-injection.html
https://www.manageengine.com/products/desktop-central/features.html
[Has vendor confirmed or acknowledged the vulnerability?]
Yes
[Discoverer]
Tarun Sehgal from eSec Forte Technologies Pvt Ltd

