Cybersixgill
AUTOMATED | ACTIONABLE | COMPREHENSIVE | REAL-TIME


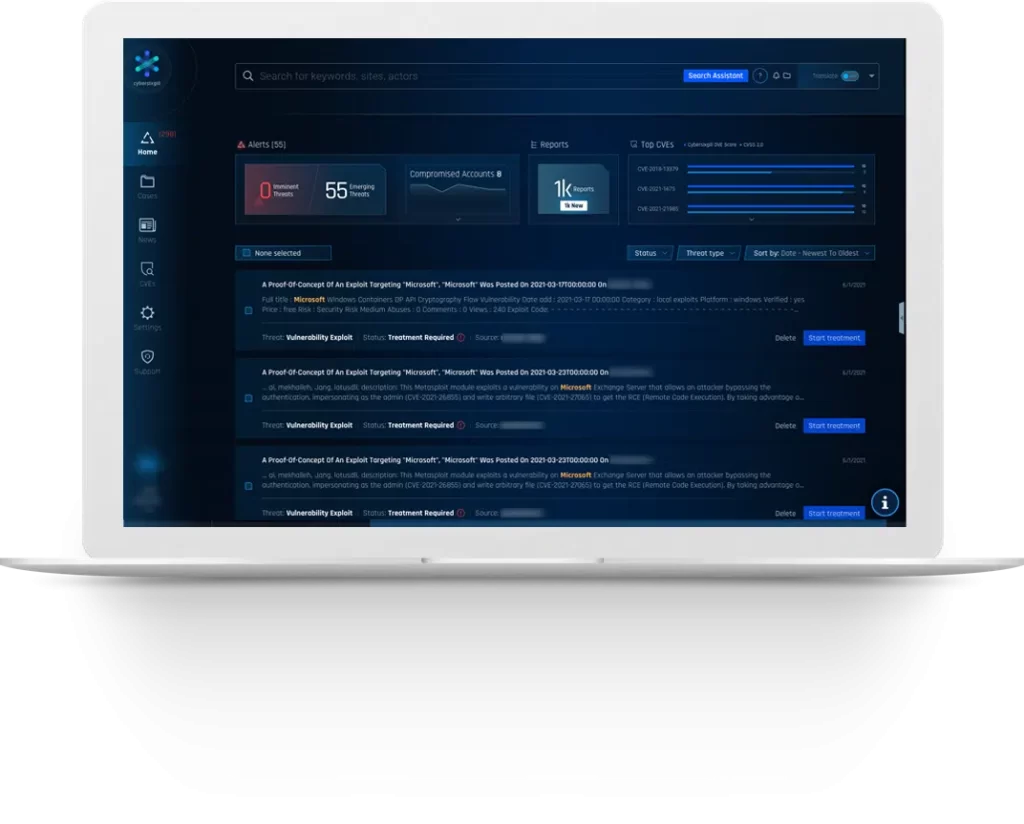

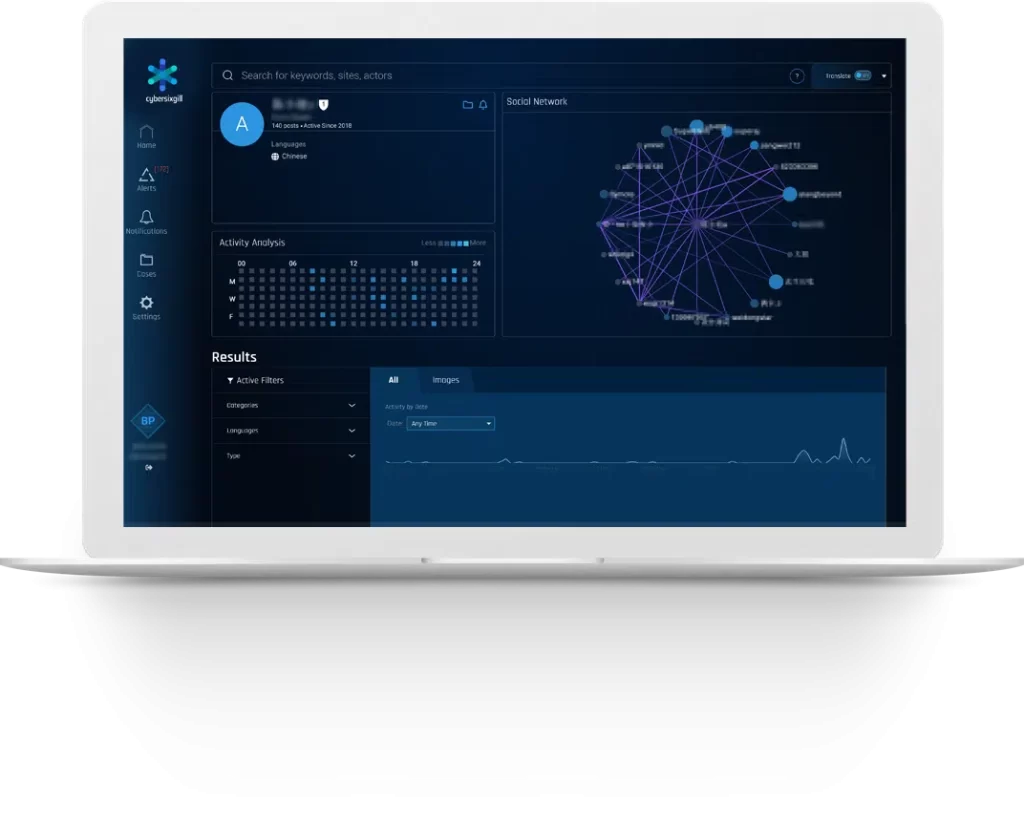

Cybersixgill Functionalities
Cybersixgill Use Cases :
Cybersixgill can be deployed in various scenarios. It features a centralized, multi-tenant and role-based architecture for direct use as well as MSSPs. Organizations from all sectors can use Sixgill to tackle a wide range of scenarios
Compromised Credentials
Alerts of leaked credentials of its employees. These credentials were either posted on the underground, or were part of a leaked DB that was shared or sold on the underground
Cyber Incidents Detection +
Incident Response
Investigate a specific threat or incident across wide datasets from the deep, dark and surface web. Including but not limited to: enrich the investigation with context, attribute an incident to a specific threat actor, and more
Executive/VIP Monitoring
Alerts if an executive is being targeted by a cyber or physical threat, including spear – phishing attacks, CEO scams, doxing, and more
Vulnerability Assessment
Investigate a specific vulnerability across wide datasets from the deep, dark and surface web. Including but not limited to: enrich the investigation with context, attribute a POC exploit code to a specific threat actor, and more
Fraud Management (Root-Cause Analysis)
Allow financial institutions to better implement a root-cause analysis of credit card leaks and mitigation
Law Enforcement Terror
Investigations
Access dozens of terror-related forums and thousands of Telegram channels. Intuitively correlate between different datasets and create a coherent intelligence picture in real-time
Cybersixgill Pricing
Its cost is dependent upon the license you wish to choose as it gives you various options. The detailed price structure can be availed through Value Added Distributor eSec Forte Technologies who are well versed with all the data associated.
Contact us today to learn more about our products and services.
We are headquartered in Gurugram & Regional Offices in Mumbai, Delhi, Bangalore – India.




