Twistlock Container Security Platform
Twistlock is the cloud native cybersecurity platform for modern applications.
Twistlock Container Security – Overview
Enterprise adoption of DevOps methodologies alongside the utilization of containers and microservices has changed the way modern applications are built and deployed. Organizations deliver value via software faster than ever before. Traditional security lacks the capabilities and depth required to protect modern applications and slows down development — putting blockers in front of the value. Twistlock Container Security is purpose-built to deliver security to modern applications, offering better protection than ever before.


BENEFITS
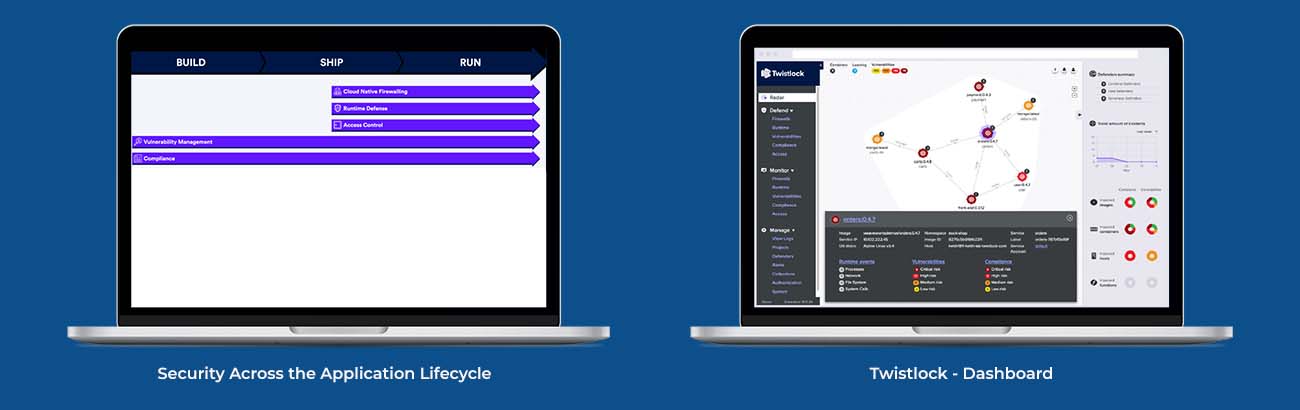
Advanced threat intelligence and machine learning capabilities deliver automated policy creation, runtime protection, and firewalls. As soon as code is built and deployed, Twistlock automatically acts based on your compliance state
From CI/CD, to SIEM, to access control and secrets management, Twistlock integrates with the tools your developers use to deliver software and the tools your security teams already leveraage for protection
Twistlock runs in any environment, be it bare metal, public cloud, or anything in between. Twistlock is engineered to automatically scale up and down as your environment and applications do.
Twistlock Container Security – Features


We Want to Hear from You !!
Contact us today to learn more about our products and services.
