

Login Brute Force on Login Page
Login BruteForce
Vendor of the product(s) – UVDesk
Product Name – Community Skeleton v1.1.1
URL of the Product – https://github.com/uvdesk/community-skeleton
Affected component(s) – memberLogin
Attack vector(s) – Remote
Suggested description of the vulnerability for use in the CVE – UVDesk Community v1.1.1 allows and unauthenticated, remote attacker to perform login brute-force password on login pages.
Discoverer/Credit – Sahil Dari
Title: Login Brute Force on Login Page
Introduction
A brute force attack is a hacking method that uses trial and error to crack passwords, login credentials, and encryption keys. The hacker tries multiple usernames and passwords, often using a computer to test a wide range of combinations, until they find the correct login information.
eSecForte Technologies Security Researcher – Sahil Dari reported a Login Brute Force
Description : UVDesk Community v1.1.1 allows and unauhenticated, remote attacker to perform login brute-force password on login pages.
Platform/Product: UVDesk Community Skeleton v1.1.1
Vulnerability Name: Brute Force on Login Page
Affected Component: memberLogin
Attack Type: Authentication Errors
Impact: An attacker could perform an arbitrary number of authentication attempts using different passwords, and eventually gain access to the targeted account
Recommendation: Common protection mechanisms include:
- Disconnecting the user after a small number of failed attempts.
- Implementing a timeout
- Locking out a targeted account
- Requiring a computational task on the user’s part.
Affected Parameter – Login Page
Affected URL – http://localhost/uvdesk-community/public/en/member/login
Methods of Exploitation:
Steps to reproduce: –
Step-1 Navigate to http://localhost/uvdesk-community/public/en/member/login and enter the username and password.

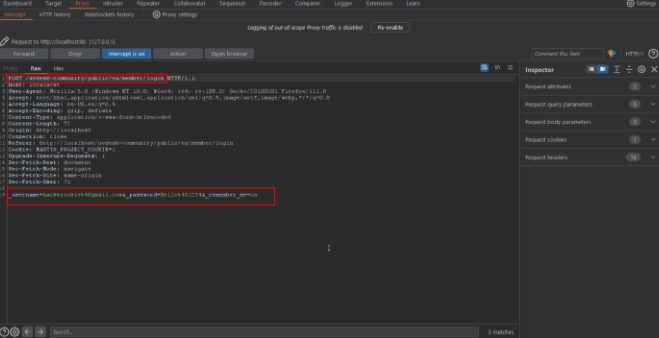
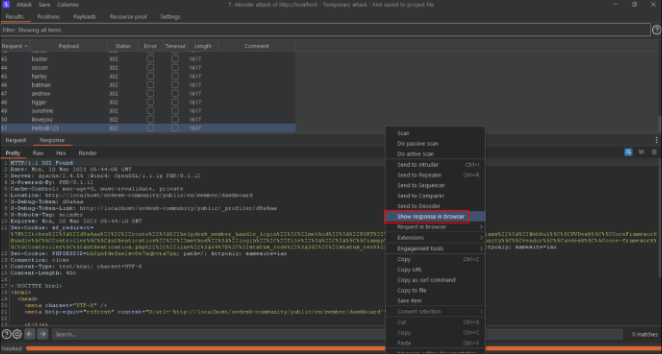
Step-2 Intercept the request in the burp suite proxy tool. Send the request to Intruder tab for brute-force attack.

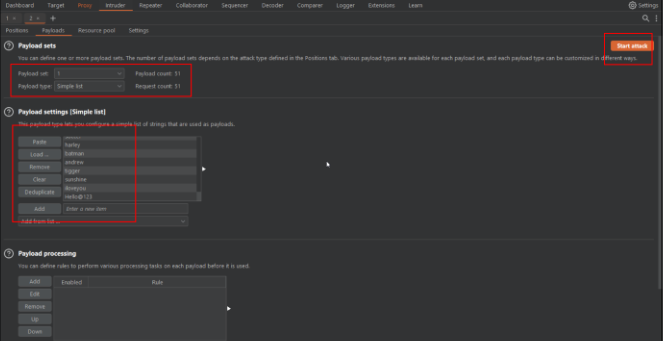
Step-3 Using password as payload position craft 50+ payloads and start the attack.

Step-4 The auditor noticed that the attack was successful.
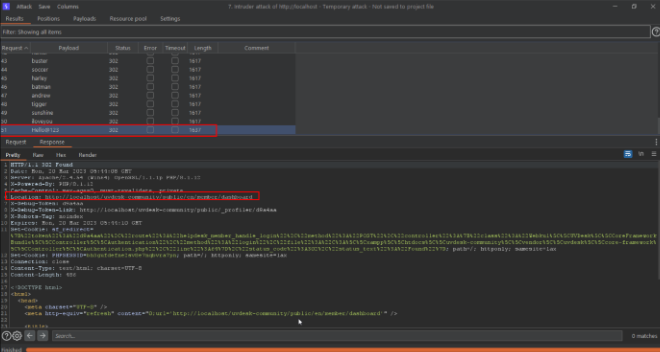

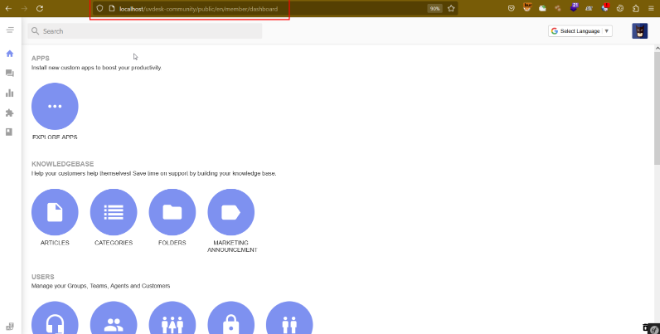
Step-5 Now show the request in the browser, the auditor noticed that the application is logged in successfully.


[Discoverer]
Sahil Dari from eSec Forte Technologies Pvt. Ltd.
