Incident Response Services
What is Incident Response?
The IT industry thrives on data and information exchange; it is critical to secure the data and devise ways to protect it. Considering the number of attacks and vulnerability of the systems, an incident response mechanism is crucial to a company. Incident response Services is a mechanism to monitor and detect events on the operations and plan security responses to those events in a well-planned and coordinated manner ensuring minimal loss of money, time and effort.
It is a formal and consistent response to an IT, computer or security incident to timely manage the consequences of a security breach or a cyber-attack. The effectiveness of the response is judged by the magnitude of damage the event has caused. Many companies develop incident responses, but an effective response plan is the one in which time, money and effort are wisely used while ensuring that the damages are minimal and their re occurrence is negligible. The effectiveness of the response is also judged by the number of improvements it has brought into the system to minimize the future attacks.
Incident Response Steps
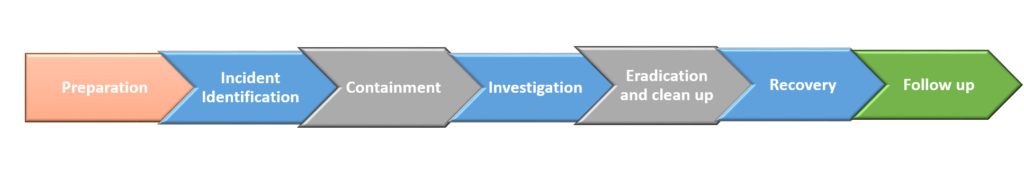

Why is incident response important?
An incident like a security breach or a cyber-attack can cause a business unexpected and unpredicted losses. It is essential to establish an incident response as it manages the aftermath of the incident limiting the losses in time, costs and damages. Incident Response services aims to quickly identify an attack and minimize its effects on the business.
Incident response plan
An organised and structured plan to systematically approach and manage the crisis post an incident. They are used in IT enterprise environments. The program is documented well and signed off from various stakeholders, the plan comprises of the actions which should be taken to minimize the damage, contain the cost and eradicate the issues. The strategy should be cost-efficient and ensure that the losses are limited. The plan should be reviewed post implementation for any learnings and knowledge that can be used in the subsequent projects. The plan should be comprehensive yet specific addressing the concerns immediately while identifying and eradicating the cause of the problem.
Incident response Life Cycle
It can be broadly divided into four stages:
- Preparation and Identification – Defining, analyzing, identifying and preparing for handling the incident. Detection and analysis for checking whether the event can be called as an incident or not. This stage also includes ensuring that you have the necessary plans in place to start the response. The team members of the incident team including the external agents need to be identified and prepared well for the response action.
Defining the event as the incident so that the appropriate action can be taken for it. Identification is a very critical stage in the lifecycle. Preparation and Identification are to be carried out well to proceed to further steps.
The companies should have onboard the right number of executives to execute the response plan; the team should be cross-functional, apart from forming the team of technical experts, the companies should also pick up people from various functions as they would help in describing the functional aspects of the problem.
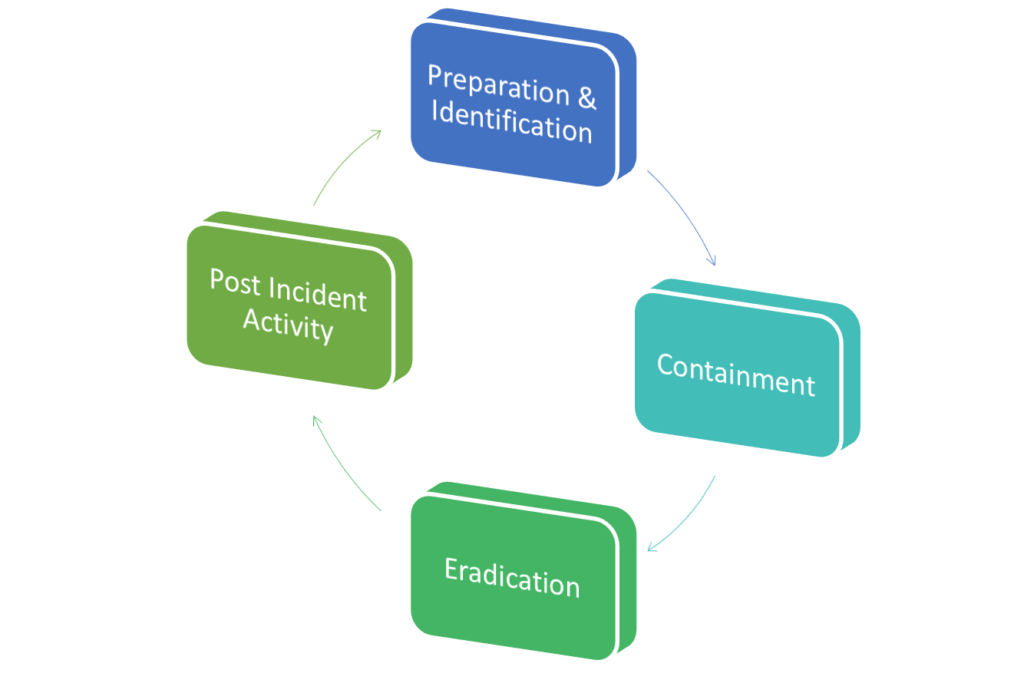

- Containment – This is to ensure that the incident is contained and does not spread further. The event needs to be limited so that it doesn’t affect the other parts of the business and ensure that the damages are not dispersed further. These include long-term and short-term activities.
- Eradication – This is to ensure that issues are eradicated, and a clean system is restored. This may include reinstalling a new system or restoring from a back-up. Mitigating the risks and resolving the problems which caused the attack is another critical step in the entire lifecycle.
- Post-incident activity – This is to review the process of handling the incident and ensuring that a similar event doesn’t reoccur. Also, the gaps in the handling procedure are checked and improved. The system needs to be monitored and reviewed well to look for any signs of abnormal activity and to use the lessons learned from the entire event to improve the processes further.
Incident response management
Incident Response management, also known as IcM is the process of effectively managing activities to identify, analyse and rectify the hazards causing damages to prevent reoccurrence of the incidents in future times. The immediate plan is to restore normalcy as soon as possible and reduce the impact on business. The IcM is needed to protect the organisation from growing threats every day.
Incident response services by eSec Forte
eSec Forte is a CMMi Level 3 certified Cyber Security company. It is crucial for businesses to choose the right partner who can help them with incident response services. Even if we have the right plan and tools available, there are high risks that something may go wrong in the process. With the Incident Response, it is essential to maintain zero tolerance levels and ensure that nothing goes wrong in any stage as minor errors can lead to significant monetary losses to the businesses.
eSec Forte provides the best solutions towards managing incidents and ensuring that the damages are minimized by planning the response well in time. Moreover, the team of professionals managing the show will make sure that you get the apt solution and save the business from future attacks. The experienced and seasoned team will help you identify early warning signs and proactively works towards resolving them.
They understand that communication is the key to ensure that the plan is valid and it proactively eradicates issues causing the incident. Therefore, with eSec, focus is emphasized on developing great communication patterns with the client. The client is provided with a detailed report of the accessed data as well as the stolen data. An exhaustive analysis of vulnerabilities and identification of affected applications, network systems and user accounts will be given by the team.
We Want to Hear from You !!
Contact us today to learn more about our products and services.
