Vulnerability Management Services
Vulnerability Management: Overview
Vulnerability Management can be defined as “the cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities.”Organizations use it to preemptively defend against the exploitation of vulnerabilities in company applications, software, and networks. Organizations that can effectively implement this service will be significantly safer from data breaches and theft.


Vulnerability Management Methodology
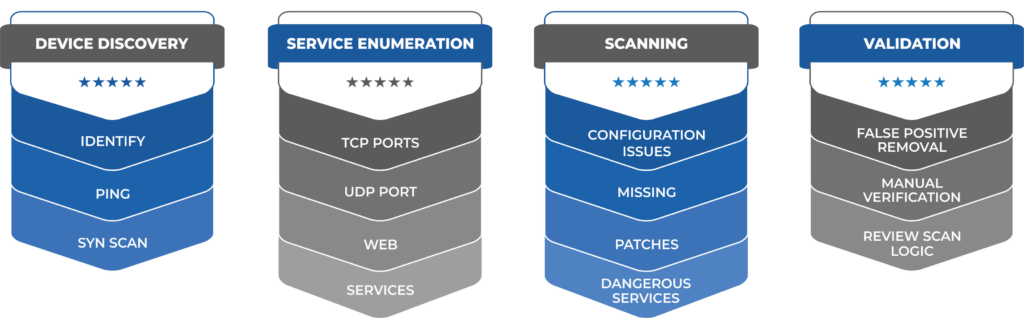

Features of Vulnerability Management Services
- Managed Security Testing
- Managed Web Application Firewall
- Database & Big Data Scanning
- Application Scanning
- Network Vulnerability Scanning
Why Use Vulnerability Management Services?
To stay secure from hacking attacks, the every Enterprise need to have an ideal Vulnerability Audit strategy.
This process can be viewed in five key steps:
- Outline vulnerability management policy.
- Discover existing vulnerabilities.
- Analyze the current level of security and rank vulnerabilities by threat level/remediation actions required.
- Mitigate the causes of vulnerabilities.
- Maintain security through ongoing testing and discovery.

The number of servers, desktops, laptops, phones, and personal devices accessing network data is constantly growing. The number of applications in use grows nearly exponentially. And as known vulnerabilities grew in number, IT managers found that traditional Vulnerability Management Solutions could easily find more problems that could be fixed.
One solution has been to concentrate on building better walls around the network to keep attackers from accessing the weaknesses. Vulnerabilities are addressed when and if there are resources available. Other solutions are to scan just the most important network resources, or to prioritize the vulnerabilities so that limited resources could be applied to fixing just those that were most likely to be misused.
None of these solutions are working very well. Even random and unfocused attackers are routinely bypassing antivirus, firewall, and IPs to find and exploit the vulnerabilities on secondary systems or that were left unrepaired because they weren’t high risk.
The vast majority of successful attacks are on the most well-known, serious, easily discovered, and easily exploited vulnerabilities. Most attackers study up on a specific vulnerability then search broadly for any network that has that weakness and then they exploit it to gain access. From that beachhead, they expand their control through the network and then look for the valuable data they can steal without being discovered.
The Business Impact of Vulnerability Management Services
- Get an application centric view of risk which is always up-to-date
- Remediate vulnerabilities quickly based on their criticality and impact on the business
- Improve accountability for risk across the organization
- Facilitate effective communication between security teams and application owners regarding risk
- Minimize your organization’s exposure to risk
eSec Forte Technologies : Vulnerability Management Company
eSec Forte Technologies is an CMMi Level 3 | ISO 9001:2008 | ISO 27001-2013 certified Vulnerability Management & Audit Company and IT Services Company with service offerings in Information Security like VAPT Services, Penetration Testing Services, Vulnerability Assessment Services , Amongst our clients we proudly count Government Organizations, Fortune 1000 Companies and several emerging companies. We have been rated as one of the leading Service Provider in Cyber Security like Vulnerability Management & Vulnerability Assessment, VAPT, Pentesting & Application Security Services. We are also Authorized Technology partners of Tenable Tool.
We are headquartered in Gurugram, Mumbai, Delhi, Bangalore – India & Singapore. Contact our sales team @ +91 124-4264666 you can also Drop us email at [email protected] for Vulnerability Assessment & Vulnerability Management Services at your Enterprise, Network, Application etc.
