

Defect Advisory for Host Header Injection in CISCO UMBRELLA DASHBOARD
INTRODUCTION
eSecForte Technologies Security Researcher – Abhinav Khanna found a Host Header Injection vulnerability in Cisco Umbrella Dashboard and a defect advisory was generated by Cisco for the same.
Cisco Umbrella is a taut cloud-driven Internet Gateway that fortifies users from all kinds of cyber proliferation, no matter the user’s environs. It is one of the most comfortable ways to safeguard the end users anywhere, in minutes.
Description: Host Header Injection vulnerability
HTTP header injection is a general class of web application security vulnerability that occurs when Hypertext Transfer Protocol (HTTP) headers are dynamically generated based on user input. Header injection in HTTP responses can allow for HTTP response splitting, Session fixation via the Set-Cookie header, cross-site scripting (XSS), and malicious redirect attacks via the location header.
Remediation:
The web application should use the SERVER_NAME instead of the Host header. It should also create a dummy host that catches all requests with unrecognized Host headers. This can also be done under Nginx by specifying a non-wildcard SERVER_NAME, and under Apache by using a non-wildcard serverName and turning the UseCanonicalName directive on.
Advisory:
The following advisory was issued by CISCO’s team for Host Header Injection vulnerability:
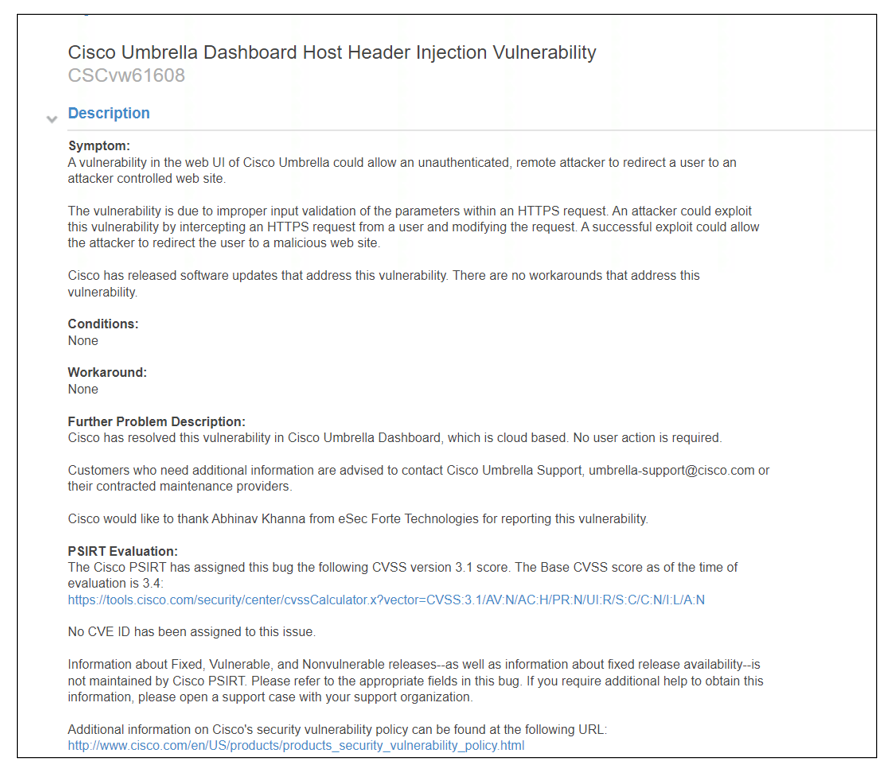

[Disclosure Process]
- Reported the Vulnerability to the Vendor Security or PSIRT Team.
- Acknowledged confirmed from the Vendor that vulnerability exists
- The vendor confirmed that the vulnerability is fixed or the latest version, the patch is released
- Defect Advisory is released.
[Reference]
http://www.cisco.com/en/US/products/products_security_vulnerability_policy.html
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvw61608/?rfs=iqvred
[Has the vendor confirmed or acknowledged the vulnerability?]
Yes
[Discoverer]
Abhinav Khanna from eSec Forte Technologies Pvt Ltd
