

Hyperlink Injection Vulnerability in Cisco Webex Meetings and Server
INTRODUCTION
eSec Forte Technologies Security Researcher – Abhinav Khanna found Hyperlink Injection vulnerability in the Cisco Webex Meetings and Cisco Webex Meetings Server and it has been assigned CVE-2021-1221.
Cisco WebEx is a cloud-based suite of productivity tools that keeps teams connected. Including WebEx Teams, WebEx Meetings, and WebEx Devices, this suite merges the web conferencing platform and the Spark team collaboration tool from Cisco.
Description: Hyperlink Injection vulnerability
Hyperlink Injection vulnerability arises when the attacker’s injected hyperlink gets successfully sent in the emails. Majority of the times, this attack involves user interaction.
Impact:
It might lead to redirecting victim to a malicious website or download trojans/viruses on victim’s system.
Proof of Concept:
The following parameters were found to be vulnerable to Hyperlink Injection which were being successfully reflected in the email body.
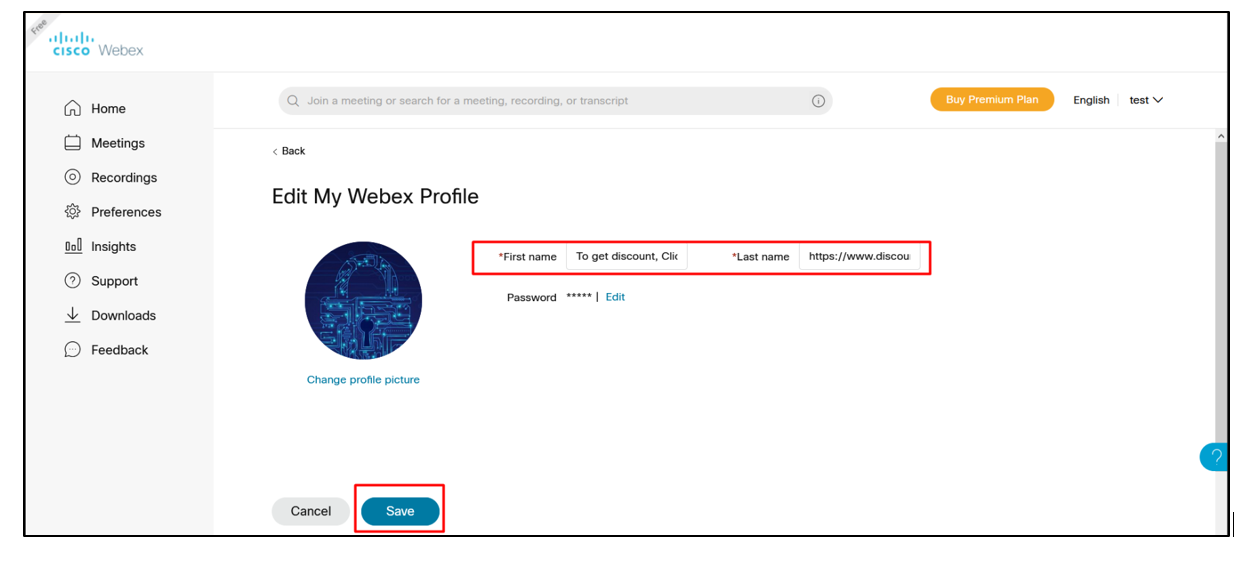

Disclosure Process
- Reported the Vulnerability to the Vendor Security or PSIRT Team.
- Acknowledged confirmed from the Vendor that vulnerability exists.
- CVE has been filed in NVD.
- The vendor confirms that the vulnerability is fixed or a latest version, the patch is released.
- Vulnerability disclosed to the public.
Reference
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-wbx-linkinj-WWZpVqu9
Has the vendor confirmed or acknowledged the vulnerability?
Yes
Discoverer
Abhinav Khanna from eSec Forte Technologies Pvt Ltd
a
