

CSV Formula and Link Injection Vulnerabilities in Cisco Umbrella Dashboard
eSecForte Technologies Security Researcher – Abhinav Khanna found CSV/Formula Injection and Link Injection vulnerabilities in Cisco Umbrella Dashboard and they have been assigned CVE-2021-1474 and CVE-2021-1475.
Cisco Umbrella is a taut cloud driven Internet Gateway that fortifies users from all kinds of cyber proliferation, no matter the user’s environs. It is one of the most comfortable way to safeguard the end users anywhere, in minutes.
Description:
Formula Injection – It occurs when the data in the file is not properly validated prior to export. The attacker usually injects a malicious payload or formula into the input field. Once the data is exported and the file is opened, the spreadsheet application executes the malicious payload on the assumption of a standard macro.
Link Injection – Link Injection vulnerability arises when the attacker’s injected hyperlink gets successfully sent in the emails. Majority of the times, this attack involves user interaction.
Possible Impacts:
Link Injection – It might lead to redirecting victim to a malicious website or download trojans/viruses on victim’s system.
Formula Injection:
- Hijacking the user’s computer by exploiting vulnerabilities in the spreadsheet software.
- Exfiltrating content from the spreadsheets, or other spreadsheets.
- Hijacking the user’s computer by exploiting the user’s tendency to ignore security warnings in spreadsheets that they downloaded from their own website.
PROOF OF CONCEPT:
Formula Injection:
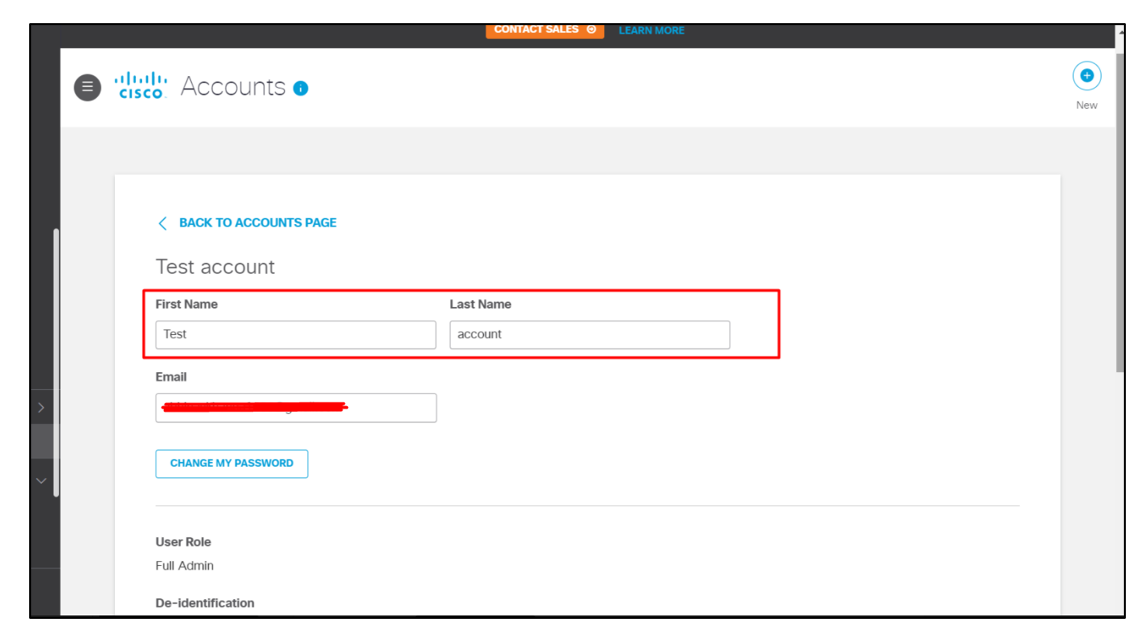
- The following parameters were found to be vulnerable to Formula Injection as by injecting the payload in these parameters, the payload was getting executed when someone downloaded the excel file.

Link Injection:
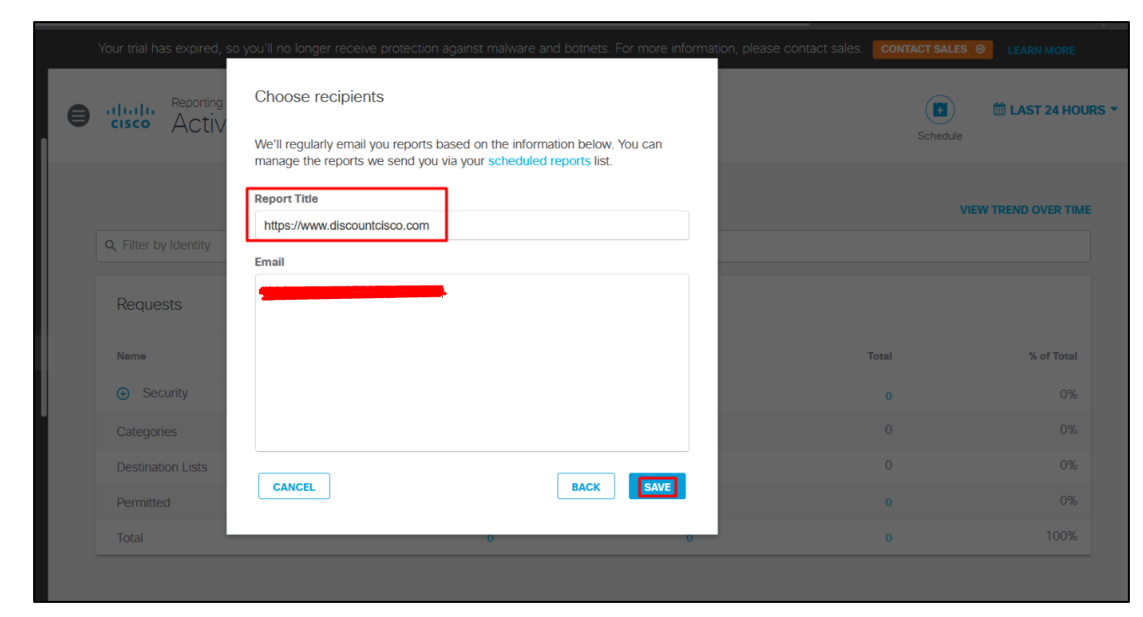
- The Report Title parameter was found to be vulnerable to hyperlink injection as the hyperlink entered in this parameter was being successfully inserted in the email.

[Disclosure Process]
- Reported the Vulnerability to the Vendor Security or PSIRT Team.
- Acknowledged confirmed from the Vendor that vulnerability exist.
- CVE has been filed in NVD.
- Vendor confirm that the vulnerability is fixed or a latest version, patch is released.
- Vulnerability disclosed to the public.
[Reference]
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-umbrella-inject-gbZGHP5T
https://nvd.nist.gov/vuln/detail/CVE-2021-1475
https://nvd.nist.gov/vuln/detail/CVE-2021-1474
[Has the vendor confirmed or acknowledged the vulnerability?]
Yes
[Discoverer]
Abhinav Khanna from eSec Forte Technologies Pvt Ltd
